What is Remote Code Execution (RCE)?
Table of Contents
What is Remote Code Execution Vulnerability and how can you protect yourself and your organization?
What are the roots of RCE and why does it happen?
RCE attack types and examples of known RCE vulnerabilities
What is the Impact of RCE attacks?
How to find Remote Code Execution vulnerabilites
How to fix Remote Code Execution vulnerabilities
What is Remote Code Execution vulnerability and how can you protect yourself and your organization?
Remote code execution (RCE) attacks are a type of cyberattack in which an attacker executes arbitrary or malicious code on a victim’s machine, typically via a vulnerable software application or service. This type of vulnerability can lead to a variety of attacks including data theft, system compromise, the installation of malware or ransomware on the target machine, and using the compromised system to launch further attacks.
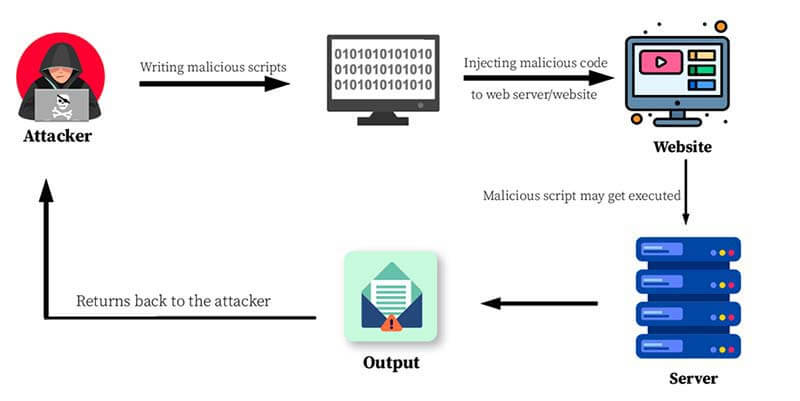
To prevent RCE vulnerability attacks, it is critical to implement safe and secure computer practices, such as keeping software up to date, using strong passwords, and avoiding questionable emails and links.
Arbitrary Code Execution: Any code or programming instruction that can be executed on computer system without built-in restrictions or protections is referred to as arbitrary code. This means that arbitrary or dynamic code execution could be used to do unauthorized or malicious actions on a system, such as stealing data, destroying files, and gaining control of the system.
Example:
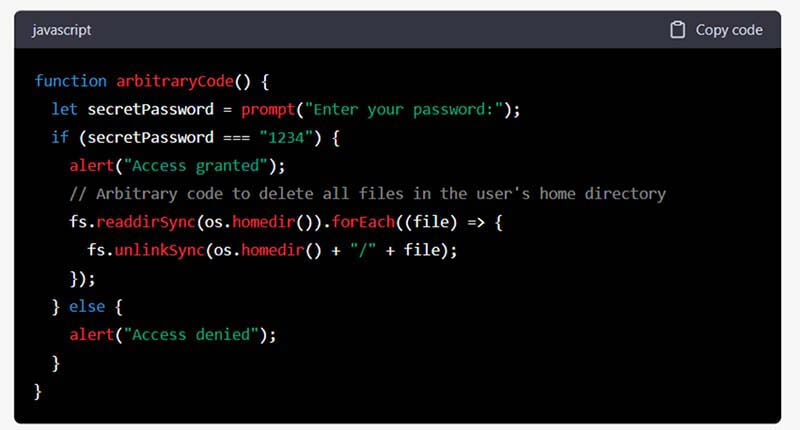
Note: Please do not run this code. This code asks the user to enter a password, and if the password is correct, it deletes all files in the user’s home directory. This could cause irreparable damage to the user’s computer and is an example of why arbitrary code execution is a serious security threat.
What are the roots of RCE and why does it happen?
Remote Code Execution attacks have their roots in the early days of computers and the development of networked systems. The possibility of attackers exploiting RCE rose as systems got increasingly interconnected, leading to the development of various security solutions such as firewalls and data encryption. But, as technology has advanced, so have attack strategies and their sophistication.
The proliferation of software vulnerabilities is one of the biggest reasons for the increase in remote code execution attacks. The number of potential vulnerabilities has expanded tremendously as software has become more complicated and widely used, giving attackers a diverse set of targets to exploit.
Another root cause of RCE attacks is the growing importance of data and information in the digital age. With data becoming the lifeblood of many organizations, attackers see valuable data as a key target, making RCE attacks an attractive option for accessing and exfiltrating sensitive information.
RCE attacks occur for several reasons, including:
-
Software vulnerabilities: Hackers use software flaws and internal vulnerabilities to execute remote code.
-
Inadequate remote machine and user input validation: Hackers use insufficient remote code evaluation and user input validation to run remote code on vulnerable device.
-
Outdated software: Vulnerable to remote code execution attacks.
-
Weak or default user inputs passwords: Allow hackers to easily gain access to systems and execute remote code.
-
Social engineering: Hackers lure individuals into remotely executing harmful malware.
-
Third-party integrations: Can bring weaknesses, vulnerable code, and application code into a network that hackers can exploit.
-
Malicious file downloads: Can be used by hackers to run remote code on systems.
Impact: Data Theft | System Compromise | Network Infiltration | Service Disruption | Reputation Damage
RCE attack types and examples of known RCE vulnerabilities
Attacks exist in different types. Some common ones are:
-
Command Injection: An attacker uses this to exploit a vulnerability in an application by injecting arbitrary commands. The attacker sends the program a malicious payload, which then executes the injected instruction.
-
SQL Injection: In this type of attack, an attacker exploits a database vulnerability by injecting malicious SQL code. The attacker can modify the database data or possibly acquire system access.
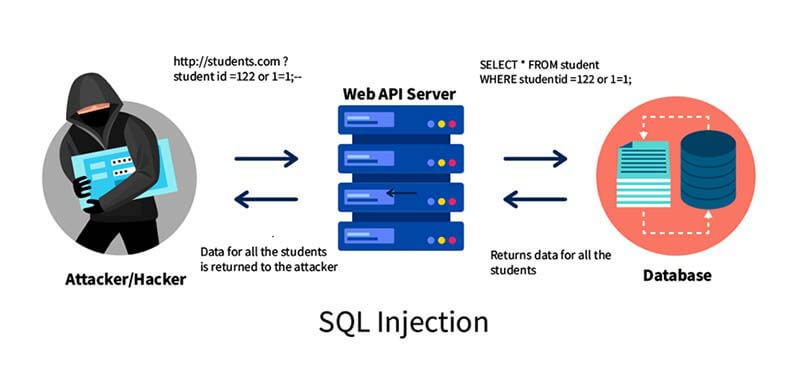
-
Remote File Inclusion: A file from a remote server is included by an attacker to exploit a vulnerability in a web application. By including a malicious file, the attacker can run arbitrary executable code.
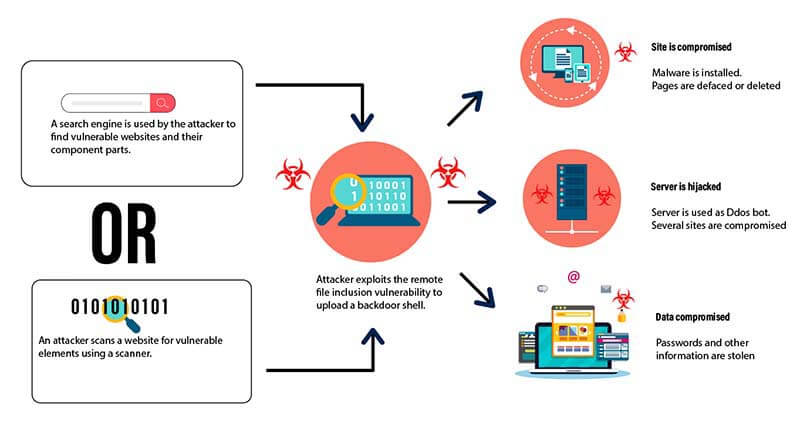
-
Cross-Site Scripting (XSS): An attacker injects malicious code into a web application in order to steal data, reroute visitors to other websites, and to execute arbitrary code.
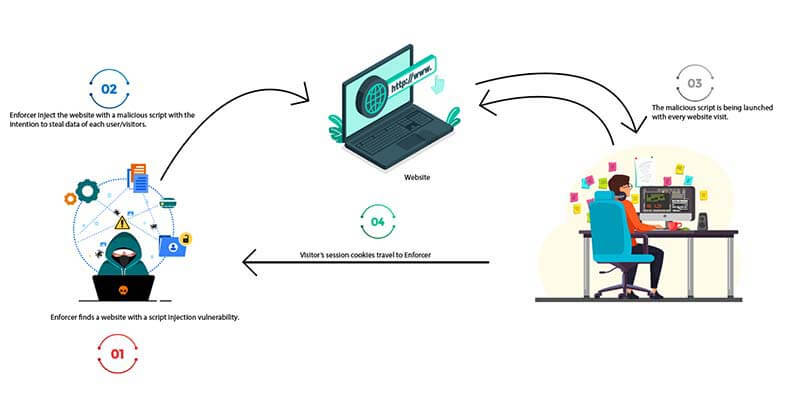
Examples of known Remote Code Execution vulnerabilities
Several significant RCE vulnerabilities exist:
Windows SMB RCE Vulnerability (WannaCry) – CVE-2017-0143
Microsoft Windows Remote Code Execution Vulnerability – CVE-2019-0708
Adobe Flash Player Remote Code Execution Vulnerability – CVE-2018-4878
Google Chrome Remote Code Execution Vulnerability – CVE-2023-0928
Oracle WebLogic Server Remote Code Execution Vulnerability – CVE-2019-2725
VMware vCenter Server Remote Code Execution Vulnerability – CVE-2021-21972
Microsoft Exchange Server Remote Code Execution Vulnerability – CVE-2021-26855
What is the impact of RCE attacks?
RCE attacks are a sort of cyberattack in which an attacker gains unauthorized access to a system or application and remotely runs arbitrary code. This has a wide range of implications, including:
Data theft: RCE vulnerabilities can be used to steal sensitive data such as financial data, personal information, intellectual property, and trade secrets.
Malware propagation: RCE can also be used to transfer malware and viruses to other computers, potentially inflicting extensive harm and causing disruption.
System compromise: A RCE vulnerability allows attackers to gain complete control of a system, which will then allow them to execute arbitrary code to modify, delete, or clear system memory, steal data, install backdoors, execute commands, and change system settings.
Service disruption: An RCE attack can be used to launch denial of service (DoS) or distributed denial of service (DDoS) attacks, making a system or web application inaccessible to users.
Reputation damage: A successful RCE assault can damage the reputation of a company or individual, resulting in legal liability, loss of revenue, and regulatory fines.
Financial loss: Because of asset theft, revenue loss, and the cost of remediation and recovery activities, RCE assaults can result in considerable financial losses.
How to find Remote Code Execution vulnerabilities
Remote code execution (RCE) vulnerabilities are a critical security flaw that allows an attacker to execute arbitrary commands via code injection on a remote system without requiring physical access. Here are some approaches to finding RCE vulnerabilities:
-
Manual testing: RCE vulnerabilities might be difficult to identify with automated scanners, so manual testing is essential. This includes testing the injection and execution of malicious code in web user input fields, intercepting and manipulating traffic, and exploiting known software flaws. You can use tools such as Metasploit, Nmap, or Burp Suite to scan the target web application for vulnerabilities.
-
Examine code for common vulnerabilities: RCE vulnerabilities occur frequently when code is not adequately vetted or sanitized. Examine the code for typical flaws such as buffer overflows, overflows errors, SQL injections, and cross-site scripting (XSS) attacks.
-
Monitor for suspicious activity: Employ network and system monitoring tools to keep an eye out for suspicious activity, such as unapproved remote code execution and odd network traffic.
-
Understand the technology: Begin by learning about the potential problems the technologies you will be programming for. This includes being familiar with the programming language, web framework, and any third-party libraries or tools that may be used to execute code.
-
Perform a vulnerability scan: Scan the system for RCE attacks and other common vulnerabilities using an automated vulnerability scanner tool. These tools can detect common RCE attack vectors and vulnerabilities in web applications, operating systems, and network protocols in a matter of seconds.
How to fix Remote Code Execution vulnerabilities
-
Patching: Ensure that all software and systems are up to date with the most recent security updates. Ensure that all software components, including the operating system, systems, applications, and libraries, are constantly updated. This helps to prevent code injection and vulnerabilities from being exploited. Learn how Patch My PC can reduce vulnerabilities within your ConfigMgr and Intune environment by automating Third-Party Patches.
-
Secure coding practices: Follow secure coding practices and perform regular code reviews to identify and address vulnerabilities in the codebase.
-
Code signing: Use code signing to confirm that software is authentic and evaluated code has not been tampered with. Learn more about WSUS Signing Certificates in regard to third-party software updates or Certificate Configuration from Patch My PC.
-
Network segmentation: Implement network segmentation to separate critical assets and limit the spread of malicious malware in case of a breach.
-
Least privilege: Ensure that all users of web apps and systems of web server have only the permissions necessary to the web server and apps and perform their tasks.
-
Secure configurations: Implement secure configurations for all systems, device web applications, and web applications.
Long term prevention strategies for Remote Code Execution
By following these steps, you can reduce the risk of RCE and keep your system and data safe. The first four strategies are recommended for most use case scenarios.
Keep your software up to date: Make sure you are running the latest version of all your software, including your operating system, web browsers, and other applications. Software updates often contain security patches that fix vulnerabilities, including those that could lead to RCE.
Disable unnecessary services: If you are not using a particular service or feature, consider disabling it. This can reduce the attack surface of your system and minimize the risk of RCE.
Be cautious when opening attachments: Be very diligent around email attachments, especially those from unknown senders. Do not open attachments unless you are expecting them and know they are safe.
Use two-factor authentication: Two-factor authentication can add an extra layer of security to your accounts by requiring a second form of authentication in addition to your password. This can help prevent attackers from gaining access to your accounts even if they have your password.
Disconnect from the network: The first step is to disconnect the infected system from the network. This will prevent the attack from spreading to other network devices.
Inform the security team: Notify the security team or IT department of the suspected attack as quickly as possible. They can take the necessary steps to confine the assault, identify its source, and prevent it from spreading.
Isolate the system: To prevent the spread of the attack, isolate the affected system from other systems and devices. This can be accomplished by disconnecting the network cable, turning off Wi-Fi, or removing the infected device from the network.
Disable remote access: If the attack is launched via a remote access tool, disable remote access to prevent the attacker from continuing the attack.
Detection strategies
Intrusion Detection Systems (IDS): By monitoring network traffic and alerting managers whenever unusual activity is discovered, IDS can be used to identify and mitigate RCE attacks.
Examples: SolarWinds Security Event Manager, ManageEngine EventLog Analyzer, ManageEngine Log360.
Log monitoring: Examine system logs for strange patterns or actions that may indicate an RCE attack.
Examples: Datadog Log analysis and troubleshooting, SolarWinds Security Event Manager, Sematext Logs, Splunk.
Endpoint Security: Install endpoint security software that monitors system activity and warns administrators when suspicious activity is discovered. Network security solutions can also be used.
Examples: ESET, Crowdstrike, Sophos, Manage Engine Endpoint Central, Symantec Endpoint Protection.
Behavioral analysis: Use behavioral analysis tools to detect and prevent anomalous behaviors that may signal an RCE assault.
Vulnerability scanning: Do vulnerability scans on a regular basis to identify and address potential vulnerabilities in software and systems.
Examples: Qualys, Crowdstrike Nmap, Tripwire.
Check out Patch My PC’s CVE Import Wizard feature for Matching CVE IDs for increased awareness of vulnerabilities within your environment.
By following these steps, you can reduce the risk of RCE and keep your system and data safe. However, remote code execution is just one of thousands of vulnerabilities that can negatively derail your website. Leveraging the patch management solutions like Patch My PC will keep your systems patched, up to date, and free of vulnerabilities. Learn how Patch My PC can improve your IT security posture by requesting a demo today.
Summary
In this post, we covered what remote code execution vulnerabilities are and how we can prevent and take action against those vulnerabilities. Patch management is one of the key elements to effective vulnerability control. By integrating third-party patch management for Microsoft and Intune platforms, Patch My PC improves IT security and guards against infrastructure vulnerabilities. By utilizing the top third-party patching program, Patch My PC, you can avoid cybersecurity vulnerabilities and their potentially disastrous effects in your environment.
You can leverage the use of CVE import wizard, as it is designed to help track the status of listed of CVEs. The CVE scan will quickly allow you to bulk match a list of CVEs to understand if the fix for the security vulnerability is available from Patch My PC
By automating the packaging 3rd party applications and updates in Standalone WSUS, SCCM and Intune environment, along with using tons of customization, Patch My PC saves you time, money, and helps your company stay secure.
Reference Articles
Vulnerability in Cyber Security – Patch My PC BlogCertificates overview – Configuration Manager | Microsoft Learn
Certificates and security – Configuration Manager | Microsoft Learn
What is the WSUS Signing Certificate and How to Create It – Patch My PC
Certificate Configuration – Getting Started (patchmypc.com)
How the CVE Import Wizard Works for Matching CVE IDs – Patch My PC
Manage Conflicting Processes when Updating Third-Party Applications – Patch My PC
Remote Command Execution Explained and Demonstrated! – YouTube
Microsoft 365 Defender – Threat Protection | Microsoft Security
Windows Update security – Windows Deployment | Microsoft Learn
