Attackers are always looking for the opportunity to breach a system, so a tight security posture is required—and this means being on top of any potential cyber security vulnerability. Patch management is an essential part of the process that helps IT staff protect business resources.
Vulnerabilities in cyber security may appear even on the largest enterprise product, as on the Windows Print Spooler in 2021. That weakness left users of Windows 10 and Windows Server 2012 and 2016 systems vulnerable to attacks, including data breaches. Even after Microsoft released a patch, many computers are still unpatched and risk an exploit.
Every modern software product and system today can face a security vulnerability. Hence, organizations that want to protect their critical processes and operations need to understand cyber security vulnerabilities and how to prevent them.
What Is a Vulnerability in Cyber Security?
Let’s start with a definition: A vulnerability is a weakness in an IT system that an attacker can exploit to deliver an attack. Security vulnerabilities can result from a system flaw, an error in software features, or more. When an attacker finds a vulnerability, they will use it to bypass security controls and gain illegitimate access to a system or network.
Types of Vulnerabilities
There are six main categories of security vulnerabilities, classified according to where they are found.
The Hardware
Computer hardware and physical infrastructure can be exposed to sabotage, firmware vulnerabilities, or theft.
The Software
Software may have design flaws, input validation errors, insufficient testing, side-channel attacks, user interface failures, format string attacks, HTTP header injection, and more.
The Network
Networks are complex infrastructures, and a typical control system uses multiple computing and communications tools. Each of them, as well as their software, can be a victim of an attack. Network vulnerabilities can include insecure network architecture, poor network security practices, man-in-the-middle attacks, or poor authentication practices.
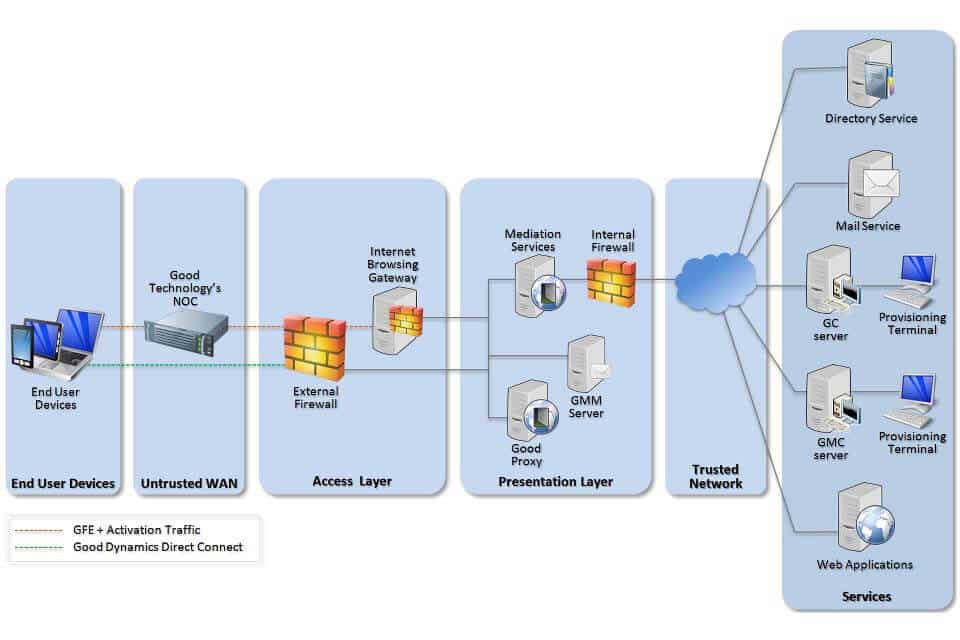
Example of BYOD Network Architecture
The Personnel
People are the first line of defense and the first cause of security vulnerabilities. Security weakness can come from a poor recruiting policy, insufficient security training, or inadequate security hygiene, such as a lack of password management, or employees accidentally downloading malware.
Organizational Deficiencies
Organizations may put themselves at risk with poor internal controls and a lack of an incident response plan or continuity plan.
Physical site
Cyber security vulnerability can also stem from a poor choice of place, such as an area with high foot traffic, an unreliable power source, or poor connectivity.
Vulnerability vs. Risk vs. Threat
The terms vulnerability, threat, and risk are not interchangeable—they refer to different things you should protect your system from. Let’s explain each definition in more detail.
As we said before, a vulnerability is a weakness in a system that malicious actors can exploit. For example, an excess of permissions in accounts or mistakes in code that cybercriminals can use to access the network.
A threat is what cybercriminals do to exploit a vulnerability.
A risk is the probability and impact of a vulnerability being exploited—the damage the attack can cause, the potential loss, destruction, or theft of your assets. Risk is the measure of what can happen when the attacker exploits the vulnerability.
Watch this video that explains the differences between bugs, cyber security vulnerabilities, exploits, and threats:
What Causes Vulnerabilities?
There are many causes of security vulnerabilities. Here is a summary:
Complex systems: The more complex the infrastructure, the more moving parts it has, increasing the risk of flaws, misconfiguration, or unauthorized access.
Familiarity of the attacker with the system: Sharing or reusing code, operating systems, and hardware increases the probability that an attacker knows about the system’s vulnerabilities.
Weak credentials: Weak passwords are easy to break. Reusing or sharing passwords can easily result in a data breach.
Operating system flaws: Unpatched or outdated operating systems can allow malicious actors to gain access and inject malware.
Software bugs: Any software can have exploitable bugs, either because of a programming error or a deliberate attack. Robust patch management prevents attackers from exploiting bugs.
What Are the Most Common Security Vulnerabilities to Watch For?
Every organization must control cyber security vulnerabilities. Hence, understanding what you need to watch for is critical to prevent giving cybercriminals an opening. Here are the seven most common cyber vulnerabilities.
Zero-Day Vulnerability
Frequently used in cyber attacks by sophisticated cybercriminals, these vulnerabilities can quickly pose a risk to any unpatched computer or system. A zero-day vulnerability is a flaw or error discovered by the attackers that are not yet patched by the software vendor.
This type of exploit may cause extensive damage because the attack may be well on its way by the time it’s detected. To detect and mitigate zero-day attacks, the key is prevention through a strong security posture and patch management. A solid response plan is also essential to respond quickly in the event of an exploit.
Remote Code Execution
Remote code execution is a type of vulnerability that enables a cybercriminal to execute malicious code remotely on a computer. An RCE vulnerability, when exploited, can range from executing malware to completely controlling the system.
Misconfiguration of Firewalls
Outdated firewall software is a common vulnerability—it’s easy to fall behind the scheduled updates and patches. Poor patching habits can result in an exposure. Misconfiguration and poorly applied security controls are other potential vulnerabilities.
Legacy or Unpatched Software
Vendors release patches and application updates periodically for a reason; either they want to add new features, or they want to patch discovered vulnerabilities. When you don’t patch or update your software in time, your system is an easy target for cybercriminals.
Unsecured APIs
Because APIs often have a public IP address, they are easily exposed to attackers if not properly secured. An unsecured API is usually a result of human error or lack of security control. Good IT hygiene and specific controls are critical to prevent APIs from being used in breaches.
Features
A malicious actor can manipulate a function to breach a system. For instance, JavaScript is one of the most used functionalities by attackers.
User Errors
Users are a common source of vulnerabilities. Poor password management, falling for phishing or malicious emails, installing malware unknowingly, or revealing credentials are some of the vulnerabilities caused by users.
OS Command Injections
Shell injections happen when a malicious actor executes an OS command on the victim’s server with the intention of reaching deeper into the organization. Typically, poor input data validation causes this vulnerability. To prevent this, you should implement strong validation protocols.
SQL injection
This web security vulnerability enables an attacker to view or modify a database by injecting malicious SQL code into an application. The attacker interferes with the communication between the application and the database, accessing the sensitive data.
What Makes a Vulnerability Exploitable?
Vulnerabilities need to be examined on a case-by-case basis—not every vulnerability is worth an exploit for an attacker. For instance, if the attack surface is reduced, the attacker can’t do much damage. Or the opposite may happen: the vulnerability gives the cybercriminal privileged access to business-critical applications. A vulnerability may also be linked to other vulnerabilities in your system, which can cause a snowball effect. Therefore, it’s important to understand the exploitability of a specific vulnerability.
What is Risk-Based Vulnerability Management?
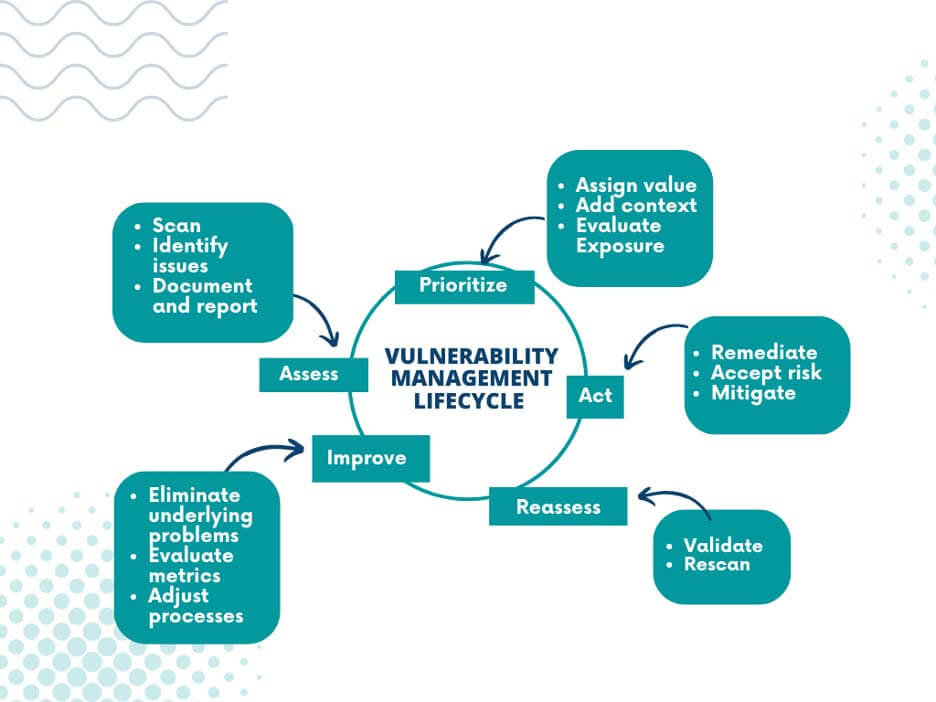
There are five critical steps in the vulnerability management lifecycle:
Assess
Start by knowing what assets you need to evaluate for vulnerabilities, and then assess each one, mapping which assets are at risk and may need patching.
There are two ways of installing an agent on each asset or using a network-based solution:
- Agent-based assessments: These involve installing an individual sensor on each asset. This is the most popular method today. The problem is that organizations often need to scan only part of the environment at a time on large systems.
- Network-based scans: These require that all endpoints are on the network. The problem with network-based scans is that they cannot evaluate assets that are not connected to the network.
After the scan, the solution usually produces a report. These legacy methods present the challenge of not being up to date—the report presents a static picture, not a dynamic one.
Modern vulnerability management tools provide a continuous assessment, thanks to cloud technologies. They allow security teams to see vulnerabilities in real time so they can be prioritized and addressed.
Prioritize
Once you know which assets and systems are potentially vulnerable, there are three steps to evaluate the situation:
- Identify the most valuable assets. Prioritize critical assets.
- Gauge the degree to which they are exposed to threats. Investigate the level of risk for each essential asset.
- Add context. Tapping into threat intelligence will provide the insights you need to correctly determine the risk you assessed in steps 1 and 2.
Act
Once the vulnerabilities and cyber security risks are identified, security teams can opt to accept the risk or mitigate or remediate the vulnerability. Accepting the risk is a relatively safe option if there is a vulnerability with low exploitability or for non-critical assets.
Mitigation is a better option for medium risk essential assets. For critical assets or high-risk vulnerabilities, remediation—patching or upgrading the asset—is the only safe choice.
Reassess
After acting on the vulnerability, it’s time to reevaluate. This helps you determine if your line of action was correct. It will also show if any new vulnerabilities have appeared linked to the ones you just remediated.
Improve
This final stage involves examining the entire vulnerability lifecycle and looking for ways to improve it. This is a time to strengthen weak defenses and work to eliminate potential issues.
Why is Vulnerability Management Important to Prevent Attacks in CyberSecurity?
Vulnerability management strengthens the organization’s security posture overall, but also has specific benefits:
- Allows security teams to respond faster to threats. For example, the Log4j vulnerability was identified before the holiday season started in 2021, which could have been a disaster if exploited.
- Leveraging vulnerability scans and assessments improves visibility over your assets, their level of exposure, and risks.
- Saves money. Prevents exploits and data breaches, which can cause loss of business and result in financial losses.
What Should You Do if You Find a Vulnerability in Your System?
This is a common dilemma: if you find a vulnerability, should you disclose it immediately, or not?
The full and immediate disclosure advocates believe that open sharing about problems—with the broader public and relevant authorities—facilitates faster patching, improving the overall security posture. Many security regulations require full disclosure within a certain period of time.
Detractors of the full disclosure say it makes attackers aware of the vulnerability. They support limited disclosure: limiting the news about the vulnerability to affected stakeholders and authorities.
Why Should Businesses Focus on Vulnerability Prevention?
Correct management of cybersecurity vulnerabilities strengthens the organization’s overall security posture by detecting weaknesses and flaws that an attacker could exploit. One of the keys to robust vulnerability management is patch management. Patch My PC automates patch management for third party applications in Microsoft Intune and Configuration Manager, enhancing IT security and preventing vulnerabilities from appearing in your infrastructure. Avoid cybersecurity vulnerabilities and their consequences with the leading third-party patching software, Patch My PC.
If you liked this content, please share it on social media.
