Since the release of Configuration Manager 1806, some customers report that the WSUS signing certificate isn’t being populated in the Third Party Updates tab of the software update point. It occurs even when the option Configuration Manager manages the certificate is enabled.
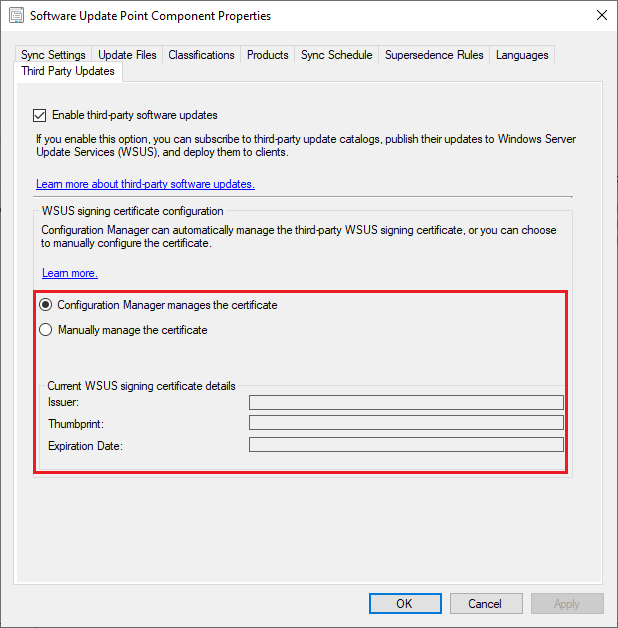
Configuration Manager Manages the Certificate Overview
The option to have Configuration Manager manages the certificate will allow ConfigMgr to create a self-signed WSUS signing certificate or to deploy an existing signing certificate.
More details about the option to Automatically manage the WSUS signing certificate can be found on Microsoft Docs
Why’s Does This Option Not Work?
The most common reason why the WSUS signing certificate doesn’t automatically get generated during a software update point synchronization (wsyncmgr.log) is that the software update point site system role is remote from your site server and the remote WSUS server isn’t configured for HTTPS.
For example, in the screenshot below SCCM3-DPMPSUP-1 is our Software update point and it’s remote from the primary site server SCCM3-SITESVR-2
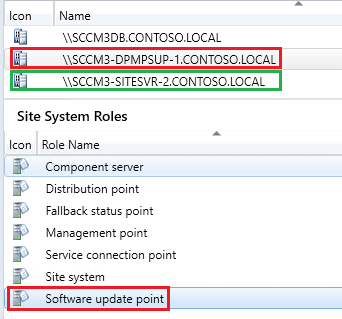
When your software update point is remote from your site server, the option Configuration Manager managed the certificate will only work if the WSUS/SUP is configured for HTTPS/SSL as described in the Microsoft Docs.
If the WSUS server doesn’t have a web server certificate and hasn’t been properly enabled for SSL, you will see the following warning in the wsyncmgr.log during a synchronization.
Warning: Remote WSUS connection is not HTTPS. This prevents software update point from getting the signing certificate for third-party updates.
Possible Resolutions for SUP not in HTTPS Mode with this Option Enabled
You have two options to work around this issue:
Option 1: Manage the WSUS signing certificate manually
The first workaround is to create a self-signed or import a PKI-based code-signing certificate for the WSUS Signing Certificate using our Publishing Service and deploy the certificate to clients using an alternative method mentioned how to deploy the WSUS signing certificate. If you choose this method, you can change the option to Manually manage the certificate in SCCM.
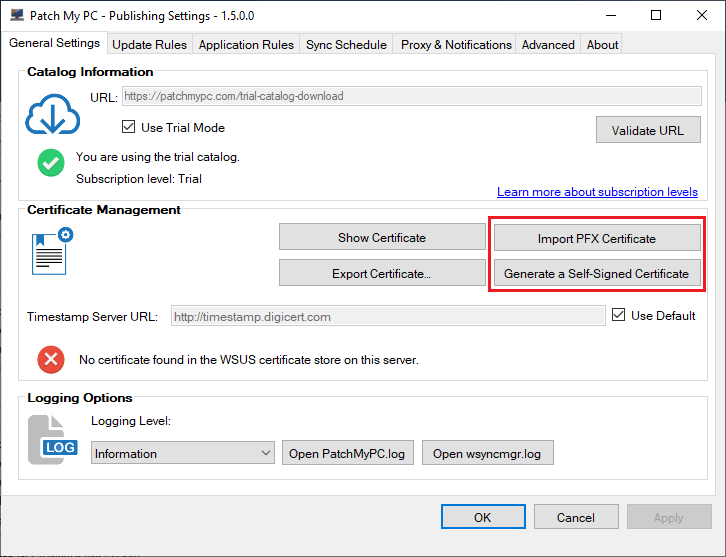
This option will generally be the most straightforward because you won’t need to request a web server certificate for WSUS and configure WSUS to use SSL. The one disadvantage to this option is clients won’t have the WSUS Signing Certificate automatically deployed to their Trusted Root and Trusted Publishers certificate store natively using the SCCM client setting to enable third-party updates.
Option 2: Switch Software Update Point to HTTPS
Configure the WSUS/SUP to use SSL/HTTPS to use the built-in option for Configuration Manager manages the certificate. Here are some resources that may help configure WSUS to use SSL.
– PKI certificate requirements for System Center Configuration Manager
