Somewhere in the world right now, a person is gaining internet access for the first time. To most of these new users the internet is a place for social media, education, and entertainment. To others, it is a way to make money, and some of the methods they use to gain their fortunes require hacking and exploitation. With over half the Earth’s population now having internet access, this means that these malicious actors are not rare, and they are only getting smarter and more advanced. That is why it is more important than ever that organizations take cybersecurity seriously.
So, let’s say you do take it seriously. You have multi-factor authentication (MFA) set up on your company accounts; you’re vetting your suppliers cautiously; you’re militant about annual security training for all employees (even the janitor!). What could go wrong? Well, in the words of Captain Jean-Luc Picard, “It is possible to do everything right and still lose”. This is where zero-day vulnerabilities come in.
What is a Zero-Day Vulnerability?
A zero-day vulnerability is an unknown flaw in released software or hardware. Since the hardware or software vendor are not aware of these security vulnerabilities, they end up shipping the product to customers with easily exploitable issues attached. These are called zero-day vulnerabilities (or, simply, “zero-days”) because there are zero days of protection or warning for users once the vulnerability is discovered. These are especially dangerous because zero-days are specifically sought out by malicious actors: it allows them to access as many systems as possible to collect sensitive company information to sell, and potentially hold ransom for large amounts of money.
Are They Different from Zero-Day Exploits and Zero-Day Attacks?
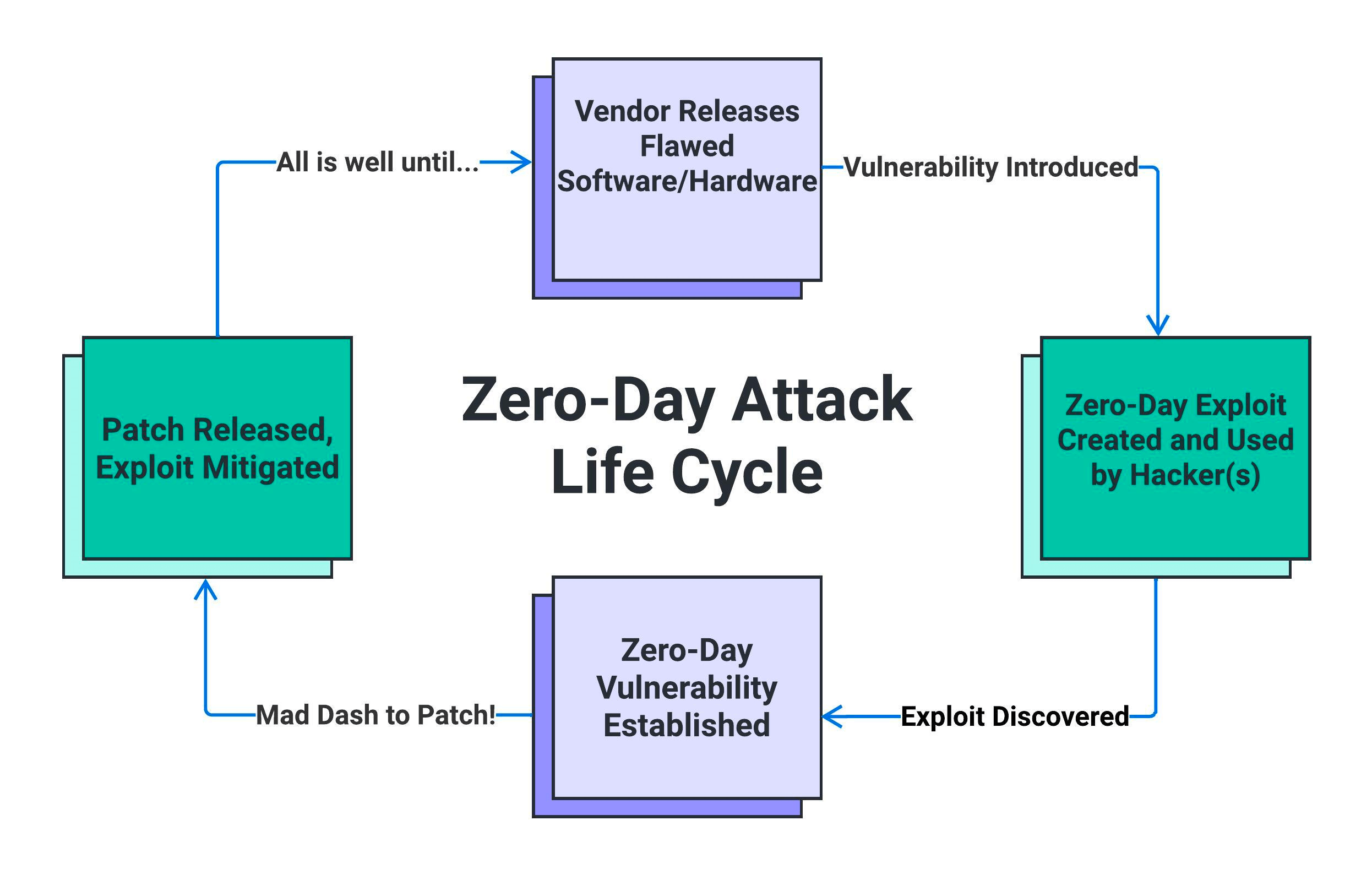
Zero-day vulnerabilities, exploits, and attacks are related terms, but they refer to different aspects of the same concept.
While a zero-day vulnerability is the flaw itself, a zero-day exploit is what cybercriminals develop in order to target those software or hardware vulnerabilities. Examples of exploits would be using malicious code, attack techniques, and backdoors to exploit vulnerabilities, all of which give the malicious actor unauthorized access to systems so they can steal data or carry out other malicious actions.
Then comes the zero-day attack where the criminals use the zero-day exploits to target vulnerable systems and networks. These attacks are incredibly challenging to defend against; since the vendor was unaware of the vulnerability, they have no patches to deploy to help protect customer organizations. Until the vendor resolves the product flaw, the organization is left vulnerable to such exploits.
To summarize: a zero-day vulnerability is a hidden weakness in software or hardware, a zero-day exploit is the code or technique used to take advantage of that vulnerability, and a zero-day attack is the actual act of exploiting the vulnerability in real-world attacks. Essentially, if a zero-day vulnerability is a wound, the exploit is the bacteria, and the attack is the resulting infection (gross, huh?).
Who Carries Out Zero-Day Attacks?

So, who is conducting these attacks? While they are all criminals, there are many different types of criminals that will conduct zero-day attacks for varying reasons.
The first group is cybercriminals.Cybercriminalscan be individualsor a part of criminal organizations, and they use zero-day exploits to compromise systems and steal valuable data for financial gain. They may use the information they obtain for identity theft, selling on the dark web, or any number of other malicious purposes.
There are also government-sponsored hacking groups called nation-state actors or advanced persistent threats (APT).APTs may use zero-day exploits to conduct cyber espionage, sabotage, or other forms of cyberattacks in pursuit of political, military, or economic objectives.
Another type of criminal to look out for are hacktivists. A famous example of a hacktivist group would be Anonymous, but hacktivists can also be individuals. These are hackers with an agenda: they usehacking as a means to promote social or political causes. They may employ zero-day exploits to disrupt services, deface websites, or steal sensitive information from organizations they perceive to be against their cause.
Lastly, there are regular ol’ criminal hackers.These are people or groups with the goal to cause harm to organizations or individuals for personal gain, which could be anything from money to infamy to just an ego boost. Those without a purpose use zero-day exploits just to show that they can, which makes them extra threatening.
These may be the major groups that engage in zero-day attacks, but it is important to remember that they are not always coming from outside your organization. Insider threats are also a possibility, as they can fall under any of these categories and have easier access to your systems. Without appropriate safeguards against both inside and outside threats, you are always at higher risk of a cyber-attack.
Who Are the Targets for Zero-Day Attacks?
Anyone can become a target for a zero-day attack so long as they have software vulnerability in their system.
Large corporations may be targeted by cybercriminals and nation-state actors to steal intellectual property, financial data, customer information, and other confidential data, while smaller enterprises are also targeted often due to having less security measures in place. This could easily lead to a supply chain attack,which is where attackers compromise suppliers and service providers as a way to gain access to larger organizations that rely on their services.
Government organizations are also a massive target. Nation-state actors frequently target government agencies to access sensitive information, carry out cyber espionage, or disrupt critical infrastructure. This critical infrastructure includes sectors such as energy, water, transportation, and education; disrupting these essential services has a widespread effect and harms the general public.
Another critical sector that often comes under attack is the healthcare system. The healthcare sector is vulnerable to attacks due to the value of patient data and the lack of emphasis on cybersecurity, which is why healthcare organizations are especially susceptible to ransomware attacks.
Although these are major targets, we’ve seen plenty of other sectors also fall prey to targeted attacks: financial institutions, non-governmental organizations (NGOs), and even manufacturing industries – such as the Colonial pipeline – have come under attack in recent years.
How Do Zero-Day Attacks Negatively Impact Businesses?
The effects of a zero-day attack are vast, regardless of sector or organization size.
Zero-day attacks can lead to significant financial losses for businesses. Attackers may steal sensitive financial data, initiate fraudulent transactions, or demand hefty ransoms in exchange for the organization’s systems and information. This can disrupt business operations by rendering critical systems and services unavailable. Not only can this downtime have a significant impact on productivity and revenue, but the costs associated with investigating the breach, recovering data, and implementing security measures can be substantial.
Along with the initial recovery costs, there are legal consequences and reputational damage to consider. Many countries have data protection and privacy laws that require organizations to safeguard customer and employee data. A zero-day attack that exposes sensitive data can lead to legal consequences, fines, and regulatory sanctions if the affected organization is found to be non-compliant. This process can severely damage a company’s reputation and erode customer trust, since no one wants to do business with an organization that cannot protect their data.
In order to recover from thi there is also the time and money that must be spent on improving cybersecurity measures to prevent future breaches. This includes the development and implementation of stronger security protocols, the acquisition of advanced security tools, and ongoing security monitoring.
All of this is to say that the effects of a zero-day attack can extend well beyond the initial incident and cause an incredible amount of damage to both the company and the customers.
How Do You Identify Zero-Day Attacks?
After all this, you may be wondering how to identify if your organization has been compromised in such attacks. This is where antivirus software and network and endpoint monitoring come in.
Utilizing network monitoring tools to scrutinize network traffic for unusual or suspicious patterns, such as unexpected data flows, unusual connection attempts, or spikes in traffic to certain ports, is the best way to catch a zero-day attack in the works.
Another option would be bringing on a User and Entity Behavior Analytics (UEBA)solution. These solutions analyze user and entity behaviors across an organization’s network to identify deviations from normal patterns, which can help detect unauthorized access or unusual activities.
Lastly, if you feel that someone is trying to use a zero-day exploit against you or your organization, you can execute suspicious file code in an isolated, sandbox environment; that will allow you to observe the code’s behavior without risking the production network. Zero-day malware may exhibit unusual behaviors in these sandboxes, so it’s a good way to root them out.
How do You Protect Yourself Against Zero-Day Attacks?

It’s clear by now that zero-day attacks are no joke; these are incredibly dangerous zero-day exploits that can have widespread, long-term effects on all sectors. So what else can we do to protect organizations against zero-day attacks?
Beyond having a proficient antivirus software and endpoint security solution deployed, proper employee training on these products and other related skills, such as log reading, will ensure that abnormalities are found as quickly as possible. This will play into having a strong incident response plan (IRP), which is the plan companies put in place for identifying and responding to security incidents, including potential zero-day attacks. By having a strong, well-maintained plan and incident response team, if your company does come under attack your company can properly conduct post-incident analysis to determine the attack vector, identify indicators of compromise (IoCs), and understand how the attack occurred. All of these preventative efforts will minimize the damage done by zero-day vulnerabilities in your environment.
There is also the option to collaborate with other organizations, security researchers, industry groups, and government agencies to share threat intelligence and information about zero-day attacks and newfound vulnerabilities. You can also participate in cybersecurity forums and communities where security vendors, researchers, and experts share information about newly discovered vulnerabilities and attack techniques. Subscribing to threat intelligence feeds and services that provide information about emerging threats and zero-day vulnerabilities. Staying informed about potential risks will significantly reduce the chance of being blindsided by an attack.
Lastly, and most importantly (in my opinion, anyway), is keeping software up to date with patch management. Keeping software up to date ensures that known vulnerabilities are patched promptly, reducing the attack surface and the likelihood of exploitation of zero-day vulnerabilities. If you want to make sure all of the third-party applications in your environment are up to date, Patch My PC has you covered. Schedule a live demo with us today to see how we make you an app patching pro!
