A few days ago, I noticed someone facing an incredibly frustrating problem on their Windows device. They kept encountering the User Account Control error message that mentioned, “This App has been blocked by your system administrator.”
Every time they attempted to run an application as an administrator, the error seemed to appear out of nowhere, and no matter what they tried, the message would still appear. To make matters worse, even attempting to right-click and select “Run as administrator” to run the app with administrator privileges would result in the same block.
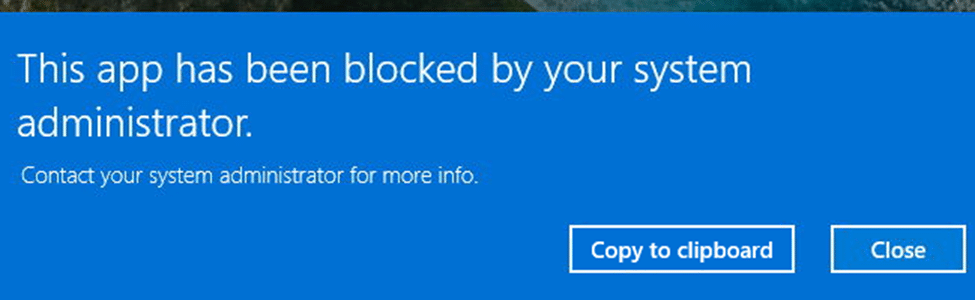
We were expecting the error: This App has been blocked error was caused by some weirdly configured UAC behavior: User Account Control Behavior Of The Elevation Prompt For Standard Users but after expecting that setting, it became clear we needed to dig further.
6 Hidden Policies That Could Be Blocking Your Apps in Windows
If you’ve ever encountered the “This App Has Been Blocked by Your System Administrator” error message, you’re not alone. It’s frustrating, and tracking down the cause can be difficult. After a deep dive into one such case, here’s what we uncovered: six potential hidden culprits, but none of them were causing the issue of obtaining administrator privileges.
1. AppLocker:
- AppLocker is often the first suspect in blocking apps. However, in this instance, no AppLocker policies were set, so we explored other possibilities.
2. Windows Defender Application Control (WDAC): Clean Slate
- WDAC / Appcontrol for Business can impose strict rules on app execution, but a thorough check revealed no active WDAC policies contributing to this block.
3. Security Baselines: Checked and Cleared
- We carefully reviewed all security baselines for any restrictive policies. After double-checking, there was no sign of any that could cause the block. Please Note: If you are using the CIS Baseline, please check out this policy: (L2) Ensure ‘Disable all apps from Microsoft Store’ is set to ‘Disabled”
4. Microsoft Defender for Endpoint: Only Monitoring
- While Microsoft Defender for Endpoint was onboarded, it was set to monitor-only mode. No policies were being enforced that could block applications from running.
5. Conditional Access & SmartScreen: Not the Issue
- Neither Conditional Access policies nor SmartScreen settings were configured in a way that would lead to the issue. Both were ruled out as potential blockers.
6. Shared Device Mode via Intune: The Hidden Player
- The real culprit turned out to be Shared Device Mode, which was quietly set through Intune. This mode is designed for shared environments (like kiosks) and restricts user permissions. In this case, it was automatically denying any attempt to run apps with admin privileges.
Everything was checked and double-checked, yet the error persisted. No matter what was attempted, any app that required admin privileges seemed completely blocked and showed them the same error message. At this point, it was starting to look like a ghost policy or an invisible setting was at work.
That’s when I started digging deeper into lesser-known configurations, and I realized there was one potential culprit still lurking in the shadows: Shared Device Mode configured through Intune.
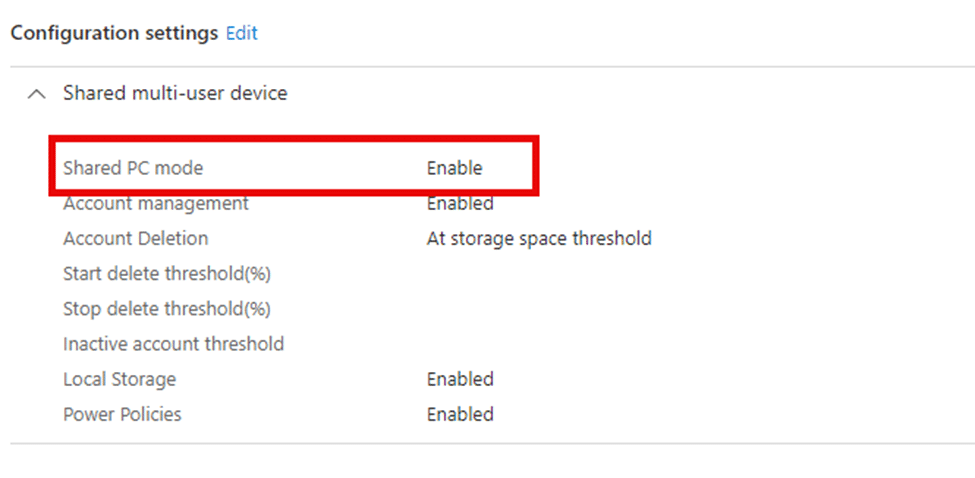
This Shared PC mode, often used for environments like kiosks or multi-user machines, can contain settings that are easily overlooked but can significantly impact user permissions and app functionality. Let me show you why!
The Missing Piece: Shared Device Policy
After exhausting the other five options, I focused on a setting that often flies under the radar—Shared Device Mode, configured via Intune. Shared Device Mode, designed for multi-user scenarios (think: shared PCs in libraries or kiosks), contains some very restrictive default configurations that can catch you off guard if not properly understood.
One particular setting stood out: the “ConsentPromptBehaviorUser” policy within this Shared Device Mode. We can spot this policy and its corresponding User Account Control settings when opening the registry editor and looking at the Windows Registry.
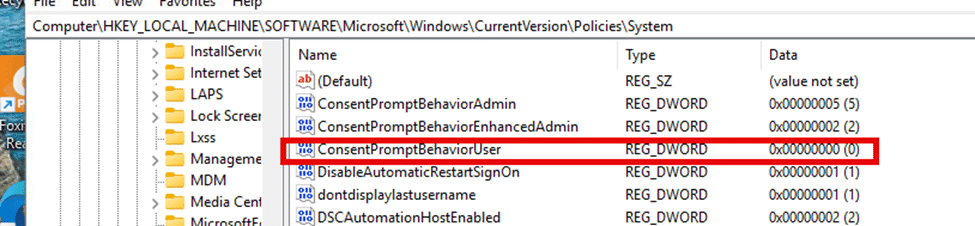
This policy, often deployed via EnableSharedPCMode, modifies the behavior of UAC (User Account Control) security settings and prompts. Specifically, it automatically denies elevation requests for standard users, essentially stripping them of the ability to right-click and “Run as administrator.”
In environments where Admin Approval Mode is enabled, elevation requests for administrators must be explicitly approved by an admin. However, in Shared Device Mode, Admin Approval Mode is bypassed for standard users, preventing any elevation attempts from succeeding, even if someone with administrator credentials attempts to approve the action. This leads to scenarios where users are completely blocked from running certain apps unless the Shared PC Mode is disabled or adjusted.
Shared PC Mode
The setting “ConsentPromptBehaviorUser” is enforced as part of the Shared PC policy and is configured to automatically deny elevation requests for standard users.
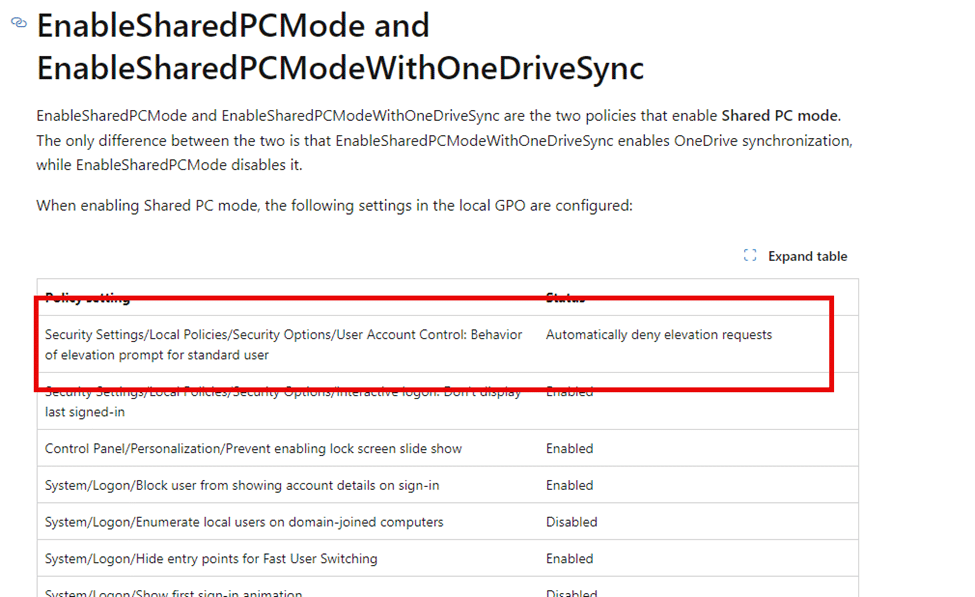
So, even if all other policies look clean, this one can still block users from running apps as an admin:
- EnableSharedPCMode: Automatically applies a GPO that denies elevation requests for standard users.
- ConsentPromptBehaviorUser: Ensures that no user can bypass admin controls by launching applications with elevated privileges.
Once Shared PC Mode is enabled, this setting kicks in regardless of whether you’ve set up other policies to manage UAC behavior. In effect, the right-click “Run as administrator” function is completely broken, as the elevation request is automatically denied without user interaction. With the elevation request automatically denied, we will get the famous error message: This app has been blocked by your system administrator.

Conclusion
In this case, the culprit wasn’t AppLocker, WDAC, or SmartScreen; it was Intune’s Shared Device Mode quietly enforcing restrictions in the background. If devices are set up for multi-user use, it’s essential to understand how this mode impacts administrative privileges and to adjust policies accordingly. Misconfigured restrictions can block apps and cause confusion for both users and admins.
Patch My PC won’t change how Intune enforces policies, but we ensure your third-party apps are deployed and updated reliably, so policy issues aren’t compounded by outdated software. Book a demo to see how we can help keep app management off the problem list.