
This blog explores why Intune Platform enrollment restrictions don’t always block outdated Windows versions, when you configured an additional policy. Many assume assigning it to all users will prevent enrollment, but Windows Autopilot for Pre-Provisioned Deployments bypasses user-based restrictions entirely. We’ll break down why this happens and how to properly enforce OS version blocks in all enrollment scenarios.
Introduction to the Platform Enrollment Restrictions
Let’s say, you have configured an additional Device Platform Enrollment restriction policy in Intune to block outdated Windows versions from enrolling instead of using the Default one.
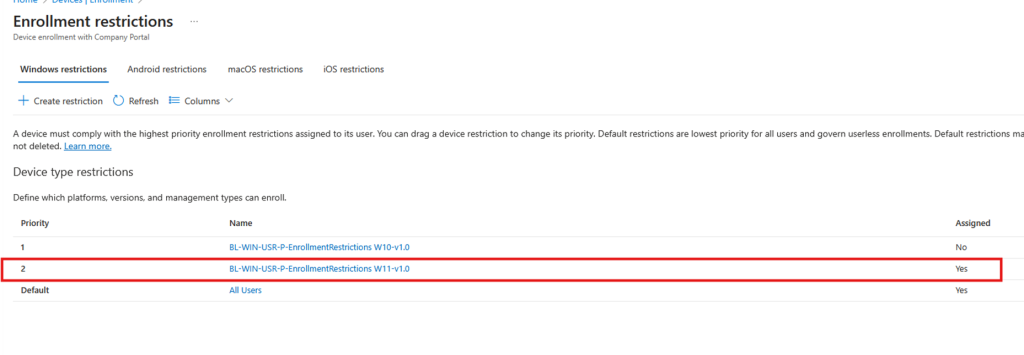
Once the additional platform restriction is created, you assigned it to all users, double-checked the settings, and expected everything to work as planned. As shown below, we configured the platform restriction to require a min Windows version of 10.0.0.22621.
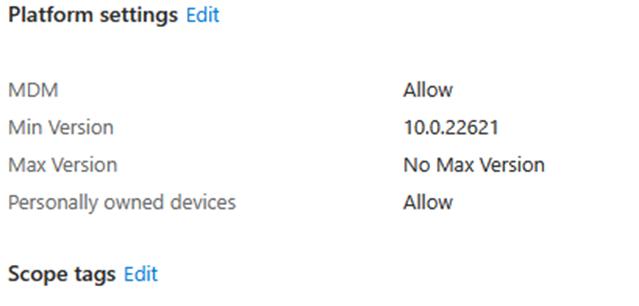
But somehow, devices with outdated Windows builds are still showing up in Intune? They’re fully enrolled and managed, even though they clearly don’t meet the OS version requirement. With it they should have been blocked, right?
You check the platform restriction policy again, and everything looks correct. So why isn’t Intune enforcing the restriction as expected?
The Assumption: Additional Enrollment Restrictions Apply Everywhere
When a user-driven Windows Autopilot enrollment happens, the assumption is that as soon as the user signs in and the device starts enrolling into Intune, the OS version Platform restrictions will be checked. If the device is running an unsupported build, enrollment will be blocked immediately.
But that’s not exactly how it works.
What Happens in a User-Driven Enrollment:
- The user reaches the Entra ID authentication screen and logs in.
- The device is Entra ID joined.
- Intune enrollment starts after the Entra join is complete.
- At this point, Intune checks the assigned platform enrollment restrictions for the user. If the OS version does not meet the requirement, the enrollment process stops, and the device is never fully enrolled in Intune, causing Windows Autopilot enrollment to fail.
That’s where enrollment restrictions come into play. They don’t apply at the Entra ID join stage but rather at the moment the device attempts to enroll in Intune after the join is complete.
But what if a device enrolls without a user signing in at all? That’s exactly what happens in Windows Autopilot for Pre-Provisioned Deployments, and that’s where things get interesting.
Windows Autopilot Enrollment: User-Driven vs. Pre-Provisioned Deployments
There are two ways a device can enroll in Intune via Windows Autopilot:
- User-Driven Enrollment – The user logs in, the device joins Entra ID, and when Intune enrollment starts, it checks if the OS version restriction applies to the user. If the version is below the minimum, the enrollment will be blocked.
- Windows Autopilot for Pre-Provisioned Deployments – The device enrolls into Entra ID and Intune before any user logs in, using TPM attestation and the Autopilot@ or “foo” user to authenticate itself to Intune.
Because Pre-Provisioned Deployments happen without a real user sign-in, Intune never checks user-based enrollment restrictions. The device authenticates at the hardware level, meaning any additional user-targeted platform restrictions are bypassed.
This is why outdated Windows versions are still enrolling, even though you configured an additional enrollment restriction. Since there is no user context at enrollment, the additional enrollment restriction isn’t evaluated, and Intune allows the process to be completed.
The Default Enrollment Restriction Policy: The Only Way to Block Pre-Provisioned Deployments
If you want to prevent outdated Windows versions from enrolling in all scenarios, including Windows Autopilot for Pre-Provisioned Deployments, you NEED to configure the default platform restriction policy instead.
Unlike additional policies that only apply when a user signs in, the default policy is enforced as soon as the device contacts Intune for enrollment!
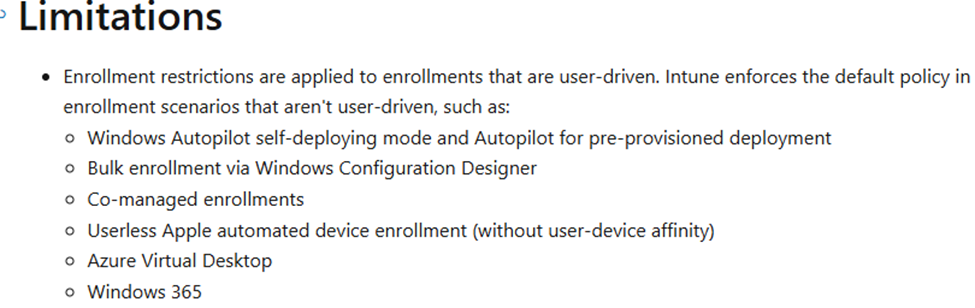
https://learn.microsoft.com/en-us/mem/intune/enrollment/enrollment-restrictions-set
As shown above, Intune enforces the default policy in enrollment scenarios that aren’t user-driven!
This means:
- It enforces OS version restrictions even when Windows Autopilot for Pre-Provisioned Deployments is used.
- Pre-Provisioned Deployments cannot bypass it. If an OS version is blocked in the default policy, the device is prevented from enrolling before the process even starts.
- User-driven enrollments still respect it, so the restriction applies regardless of whether a user is present or not.
If you only configure an additional user-based enrollment restriction and leave the default one untouched, Pre-Provisioned Deployments will ignore the restriction entirely. That’s why outdated devices are still enrolling.
How to Actually Block Old Windows Versions
If you want to ensure that outdated Windows versions never enroll, no matter the scenario, you must:
- Edit the default enrollment restriction policy in Intune.
- Set a minimum OS version for Windows under platform restrictions.
- Save the policy and ensure it applies to all devices.
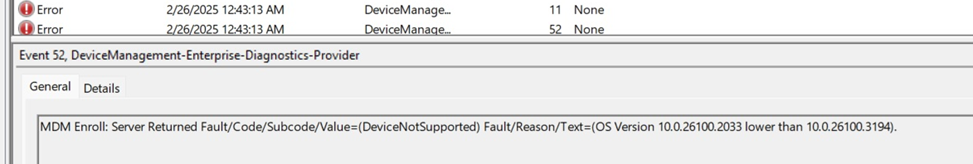
Once this is configured, Intune will enforce the OS version check in both Windows Autopilot user-driven enrollment and Windows Autopilot for Pre-Provisioned Deployments. With this restriction in place, the enrollment will be blocked!
Conclusion
If you assumed that assigning an additional enrollment restriction policy to all users would block outdated devices from enrolling, now you know why it didn’t work. Windows Autopilot for Pre-Provisioned Deployments completely ignores user-targeted platform device enrollment restrictions because there’s no user context at enrollment.
The only way to enforce OS version restrictions at all stages of enrollment, whether user-driven or pre-provisioned, is by modifying the default enrollment restriction policy. If it’s not set correctly, outdated devices will continue to slip through, regardless of additional restrictions.
