Have you ever wondered what keeps the Intune Management Extension (IME) secure from accidental or unauthorized uninstallation? If you thought certificates were just about enrollment and secure communication, think again! In this blog, we will uncover a hidden layer of protection that ensures only authorized devices can uninstall the IME, keeping your devices securely managed. Let’s explore the IME’s uninstallation protection mechanism, breaking down how certificates validate device integrity and tenant flighting ensures controlled feature access.
Introduction
In my previous blog, we explored the Intune Management Extension (IME) Cert Checker in depth, uncovering its key role in ensuring certificates are in place to keep devices communicating securely with Intune. While investigating that process, I stumbled upon something unexpected, something that adds a whole new twist to the story. So, what’s going on?
It turns out that certificates aren’t just for keeping devices enrolled; they also play a critical part in uninstalling the Intune Management Extension itself! Let’s zoom in on how this works.
Why Uninstallation Protection Matters
Before we dive into the technical flow, let’s consider why controlling IME uninstallation is so important. If the IME were removed unintentionally or without proper authorization, devices could lose their management capabilities, leaving them non-compliant and potentially vulnerable. This could disrupt device configurations, jeopardize security baselines, or even expose sensitive data. That’s why Microsoft implemented a robust mechanism to ensure only authorized removals occur.
How the IME Picks Up the Uninstall Policy
Behind the scenes, the IME relies on several core components to manage uninstallation policies. When the EmsAgentService starts, it registers the SideCarUninstallationPlugin with the PolicyProcessor, which is responsible for managing policies on the device.
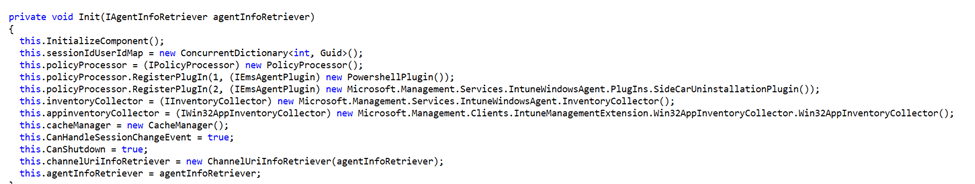
The ChannelUriInfoRetriever component then retrieves all necessary policies from Intune, including the policy related to uninstallation. This information is essential to determining whether the device is authorized to uninstall the IME.
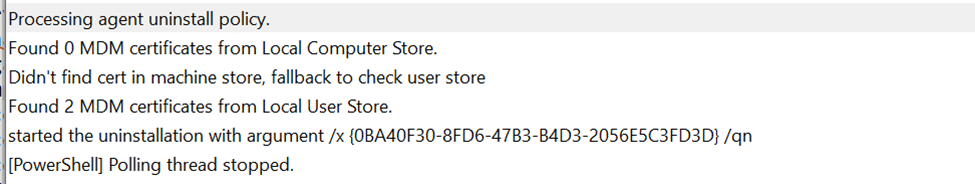
The Uninstallation Plugin: Certificates Play a Bigger Role Than You Think
Here’s where things get interesting. Certificates aren’t just involved in keeping devices enrolled; they also play a key role in uninstalling the Intune Management Extension (IME). Before any uninstallation happens, the SideCarUninstallationPlugin ensures that:
The device has a valid certificate.
The tenant is not flighted to prevent uninstallation.
This dual-layer check ensures that only properly authorized devices and tenants can trigger the uninstallation process, preventing unintended or unauthorized removal of the IME.
Tenant Flighting for Uninstallation Protection
Tenant flighting adds an extra layer of security by controlling which tenants are allowed to uninstall the IME. Inside the SideCarUninstallationPlugin code, the tenant flighting mechanism checks whether uninstallation is permitted.
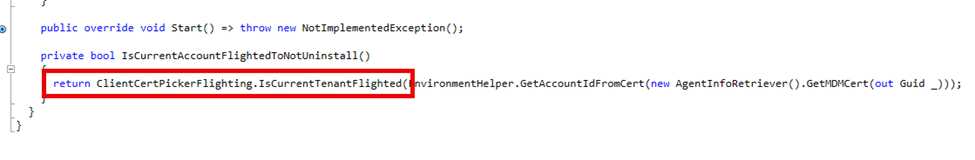
If the tenant is configured to block uninstallation, the process halts, ensuring that the IME remains active on the device.
This mechanism plays a critical role in maintaining device compliance and security. By restricting uninstallation to specific scenarios, Microsoft ensures that only devices managed under the correct policies can execute this operation.
Valid Certificates and Controlled Uninstallation Protection
Uninstallation can only proceed if the tenant allows it and the device has a valid certificate. This process involves the same certificate validation steps used during regular device operations, ensuring secure communication and compliance. Certificates act as a gatekeeper, verifying device identity and authorization before allowing the uninstallation process to continue.
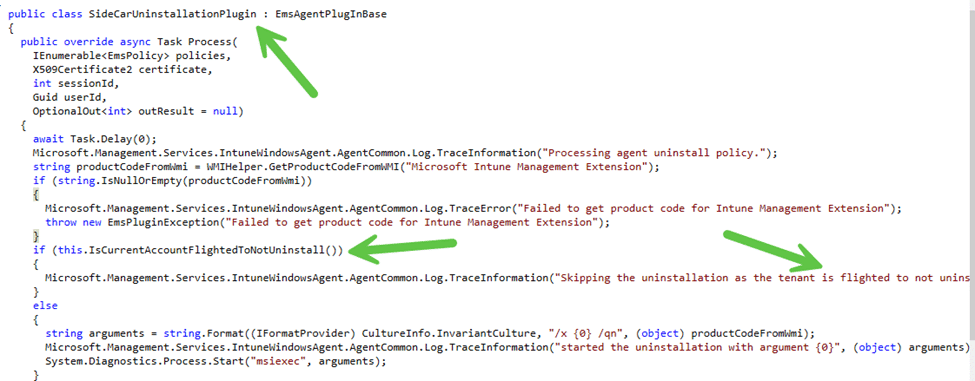
By requiring valid certificates, the IME ensures that only authorized devices can proceed with uninstallation. This safeguards against accidental or unauthorized removal, reinforcing the device’s compliance and keeping management intact without unnecessary risks.
The Flow
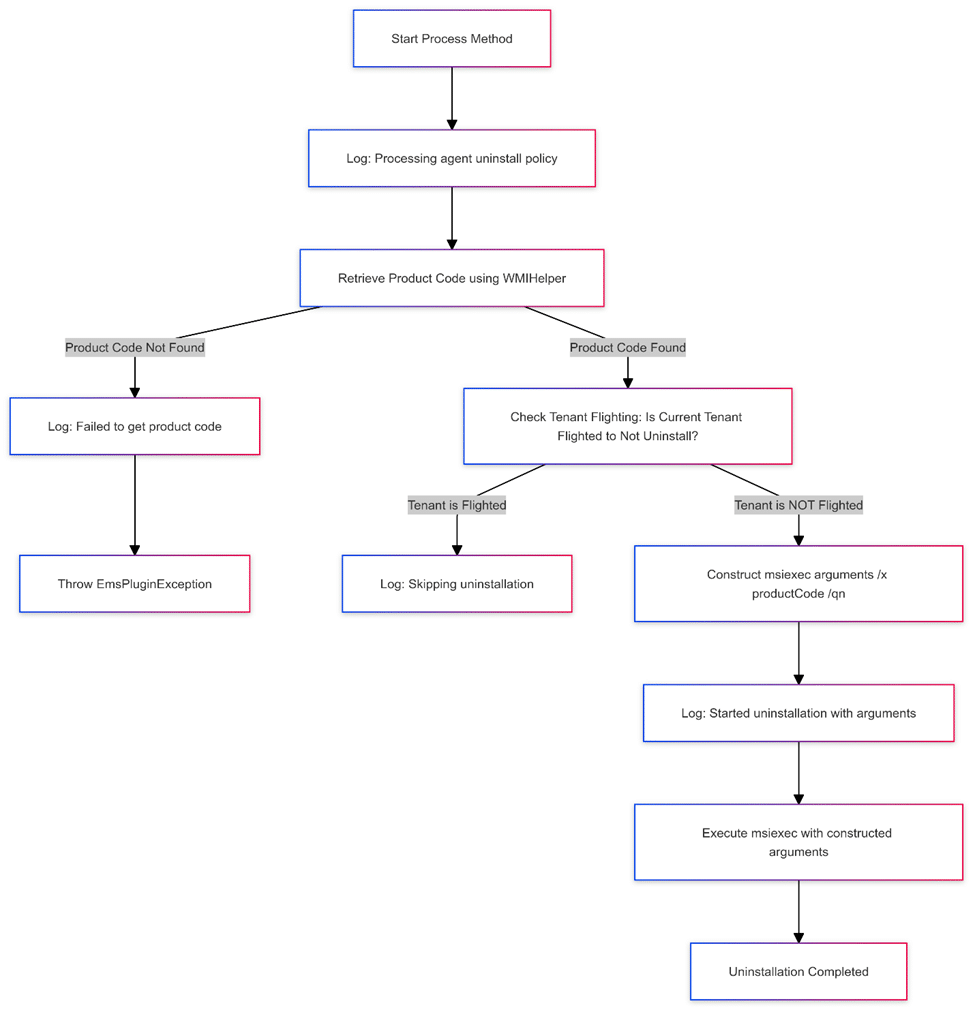
To summarize the uninstall protection process:
The EmsAgentService starts and registers the SideCarUninstallationPlugin.
The PolicyProcessor manages the uninstallation policy retrieved by the ChannelUriInfoRetriever.
The system checks tenant flighting to determine if uninstallation is allowed.
Certificate validation ensures the device’s identity and authorization.
Only when all checks pass does the uninstallation proceed.
Conclusion
The IME uses a tightly controlled process to ensure that uninstallation only happens when it’s fully authorized. The interaction between the SideCarUninstallationPlugin, PolicyProcessor, and Cert Checker creates a secure environment where uninstallation is only possible when all the checks align. This mechanism not only protects devices from accidental or unauthorized uninstallation but also reinforces overall compliance and security within the Intune ecosystem.
