Have you ever tried to deploy different Microsoft Edge extensions to different devices via GPO/Intune policies? If the answer is yes, you’ll know that Edge and Intune / GPO policies are not a match made in heaven. Let me explain how Edge Extension policies and the PSAppDeployToolkit are a match made in heaven.
Edge extension policies such as ExtensionInstallForceList create numbered lists in the registry containing URLs and related settings. As soon as you need to install different extension settings on different devices, you might have to replicate and and keep in sync the content of the extension policy lists in multiple policies. In larger environments where there can be multiple combinations of extensions needed on various devices, it starts to get unwieldy.
We created a simple solution to overcome this challenge with the PSAppDeployToolkit by enabling Edge Extensions to be deployed and managed like applications. Some of the benefits of managing Edge extensions like applications are that extensions can be:
- Managed individually and not part of an entire policy set of extensions
- Installed and uninstalled like applications
- Targeted to users or devices
- Added as dependencies of applications or an application deployment group can be added as a member of the extension deployment group
- Published in the same catalog as applications, e.g. Company Portal
Edge Policy Management Overview
Before we jump into the solution, it’s important to know that Extensions policies can be managed in different ways;
1. Intune / GPO Policy Management
- Policies apply to managed devices only.
- Policies apply to all Edge profiles on the device.
2. Edge Management Service (M365 Admin Center)
- Policies apply to managed and unmanaged devices.
- Policies follow the user irrespective of the device (corporate or personal)
- Policies only apply to the managed Edge profile, so users can circumvent corporate policies and install extensions in a separate Edge profile.
Neither solution solves the problem of deploying different extensions on different devices. Intune/GPO policy management has the advantage that it will apply to all profiles on the device. EMS has the advantage of controlling policies on unmanaged devices, which might be useful for scenarios such as MAM for Edge. For our purposes, we are focussed on the managed device scenario.
Why is this relevant? The solution we developed in PSADT is applicable to Intune/GPO management scenarios. It cannot be used in conjunction with extensions configured in EMS because EMS leverages the same ExtensionSettings registry key, which will, therefore, conflict.
Edge Extension Deployment with PSAppDeployToolkit
The Configure-EdgeExtension function that was released in PSAppDeployToolkit v3.10.1 leverages Edge ExtensionSettings, which is a JSON string specifying the extensions and their settings to be configured. By individually adding and removing extensions from this JSON construct we can manage extensions like applications.
The benefit of using ExtensionSettings is that it takes precedence over ExtensionInstallForcelist, ExtensionInstallAllowlist and ExtensionInstallBlocklist policies, so these settings can co-exist side-by side with the extensions deployed by policy. As an example, you can have a GPO or Intune policy that uses ExtensionInstallForceList to push mandatory extensions for all devices and alongside that you can push specific extensions to a subset of devices using ExtensionSettings. Using ExtensionSettings also offers more configuration options. Here is an example of the ExtensionSettings JSON used to install an extension:
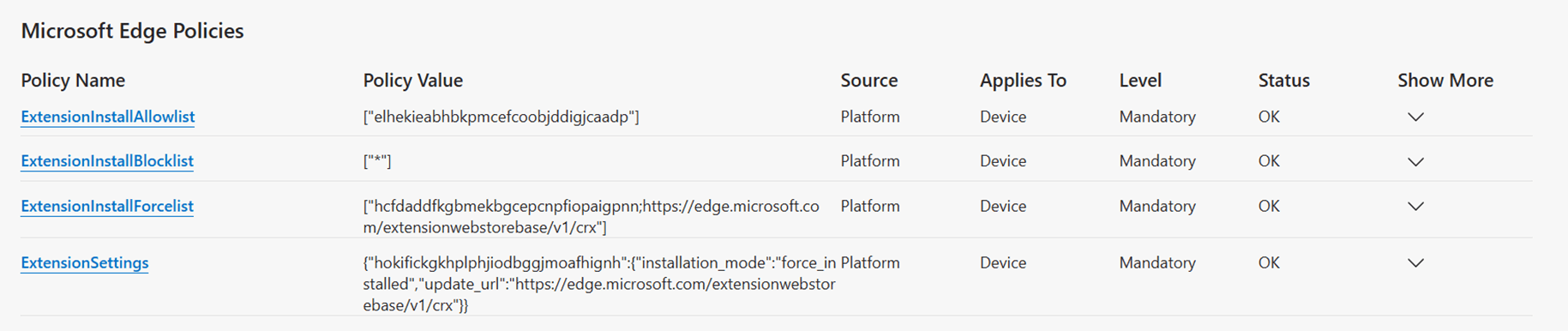
{"hokifickgkhplphjiodbggjmoafhignh":{"installation_mode":"force_installed","update_url":https://edge.microsoft.com/extensionwebstorebase/v1/crx}} You can see the policies applied to a device by opening Edge and navigating to edge://policy, then locate the policies related to extensions. The screenshot below shows an example of policies configured with the following:
- All extensions are blocked by default using “ExtensionInstallBlocklist”.
- One extension is allowed for users to install using “ExtensionInstallAllowlist.”
- One extension is force installed using “ExtensionInstallForcelist”
- One extension is force installed using “ExtensionSettings” (method used by PSAppDeployToolkit)
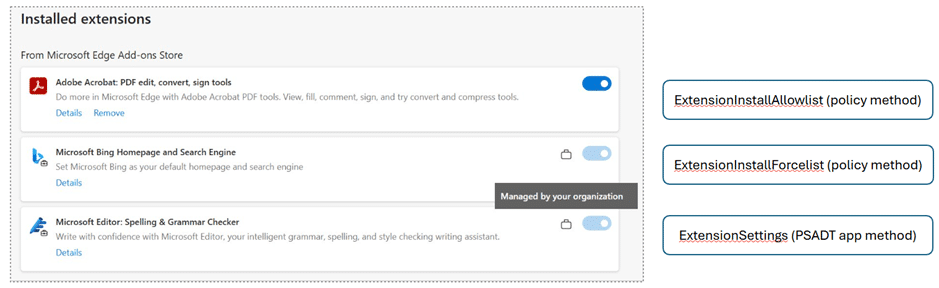
You can navigate to edge://extensions to see the extensions installed on a device. Extensions force-installed using either the policy or PSAppDeployToolkit’s method will appear as locked and “Managed by your organization”. The following screenshot shows what each method looks like:
Using Configure-EdgeExtension
You can deploy Edge extensions using PSAppDeployToolkit by doing the following.
- Download a copy of PSAppDeployToolkit. You can find the latest release here
- Extract the downloaded archive and copy the Toolkit folder into a new location. This is, essentially, creating a new deployment using a standard deployment template
- Open the `Deploy-Application.ps1` script and update the Initialization section with an `AppVendor`, `AppName` and `AppVersion`
- Add the following code to the relevant script sections, substituting with the correct `ExtensionID`
- The `UpdateURL` should contain the location where the extension should be installed from and should be set as follows:
- Microsoft Edge Add-ons store – `https://edge.microsoft.com/extensionwebstorebase/v1/crx`
- Chrome Web Store – `https://clients2.google.com/service/update2/crx`
- Other – Use the URL where Edge can download the packed extension (.crx file)
# Installation
Configure-EdgeExtension -Add -ExtensionID "hokifickgkhplphjiodbggjmoafhignh" -InstallationMode "force_installed" -UpdateUrl "https://edge.microsoft.com/extensionwebstorebase/v1/crx"
# Uninstallation
Configure-EdgeExtension -Remove -ExtensionID "hokifickgkhplphjiodbggjmoafhignh"
Once you’ve created your application in Intune, you’ll need to use a detection method to verify if the extension has been installed successfully. The following script will do this. You’ll need to configure the `$extensionID` variable:
$PSDefaultParameterValues['Out-File:Encoding'] = 'utf8'
$extensionID = ''
$regKeyEdgeExtensions = 'HKLM:\SOFTWARE\Policies\MicrosoftEdge'
$installedExtensions = Get-ItemProperty -Path $regKeyEdgeExtensions -ErrorAction SilentlyContinue | Select-Object -Property 'ExtensionSettings' -ExpandProperty 'ExtensionSettings' -ErrorAction SilentlyContinue | ConvertFrom-Json -ErrorAction SilentlyContinue
If ($installedExtensions.$($extensionID)) {
Write-Output 'Installed'
Exit 0
}
Else {
Exit 1
} One more thing …
Extension manifest v2 deprecation
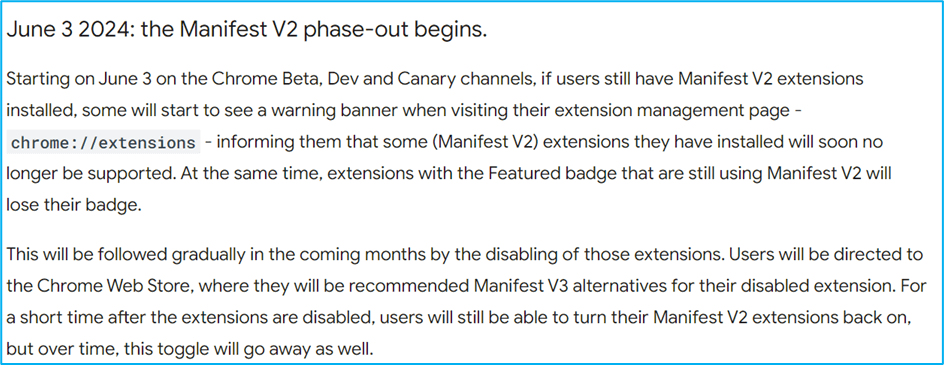
It’s important to note that in all Chromium-based browsers (including Microsoft Edge), Manifest v2 extensions will soon be disabled]. Below is an overview of the phase-out timeline published on the Chrome website:
At the time of publishing this post, Microsoft have not yet confirmed a timeline for Edge. The latest statement from Microsoft is that *”Manifest V2 extensions will continue to be supported through Enterprise policies at least until the date in the Chromium Manifest V2 support timeline” and “The Microsoft Edge team is currently in the process of updating this MV3 migration timeline”*.
Although is a little bit vague, it’s good to get ahead of this. You can get another year of support and ensure those extensions are exempt until June 2025 by configuring the ExtensionManifestV2Availability policy to either of the following values:
- 2 = Manifest v2 is enabled
- 3 = Manifest v2 is enabled for forced extensions only
The following script will report on all the extensions installed in the current user’s profile including the manifest version. With this, you can discover which extensions are still running manifest v2:
# Edge profile path
$edgeProfilePath = "$env:LOCALAPPDATAMicrosoftEdgeUser DataDefault"
Try {
# Edge extensions path
$edgeExtensions = Get-ChildItem -Path "$edgeProfilePathExtensions" -Directory
$edgeExtensionManifestDetails = @()
# Process each extension found
ForEach ($edgeExtension in $edgeExtensions) {
# Extension ID based on the directory name
$extensionId = $edgeExtension.Name
# Extension version based on the extension sub-directory name
$extensionVersions = Get-ChildItem -Path $edgeExtension.FullName -Directory
# Process each version found
ForEach ($extensionVersion in $extensionVersions) {
# Manifest file path
$edgeExtensionManifestPath = "$edgeProfilePathExtensions$($extensionId)$($extensionVersion)manifest.json"
# Get the extension manifest file content
$edgeExtensionManifest = Get-Content -Path $edgeExtensionManifestPath -Raw | ConvertFrom-Json
# Populate an object with the manifest details
$edgeExtensionManifestDetail = [PSCustomObject]@{
Name = $edgeExtensionManifest.name
Version = $edgeExtensionManifest.version
ManifestVersion = $edgeExtensionManifest.manifest_version
Description = $edgeExtensionManifest.description
UpdateURL = $edgeExtensionManifest.update_url
}
# Append the object to a list
$edgeExtensionManifestDetails += $edgeExtensionManifestDetail
}
}
}
Catch {
Write-Host "Failed to retrieve Edge extension manifest details: $_" -ForegroundColor Red
Break
}
# Output the details of each edge extension discovered
$edgeExtensionManifestDetails
To gather data on all extensions in your organization, consider using the Configure-EdgeExtensions function to bulk install all extensions identified from your organization’s policies on a test device, then run this script to get the manifest version details. Another approach could be to deploy this script as an Intune Remediation run in the user context and output the data to Log Analytics to get a view of all Extension manifest versions across your estate.
Conclusion
Having the ability to manage Edge Extensions like applications can simplify the job of an IT Admin and provide your customers with more flexibility. Edge Extension Manifest v2 deprecation is approaching, so don’t forget to take care of business and prevent broken extensions.
