Latest Trends
While estimating the exact number of annual malware attacks might be difficult due to under-reporting, according to the US-based Internet Crime Complaint Center, cyber crimes caused 12.5 billion dollars of damage in 2023. With various tools and tricks at bad actors’ fingertips, it is crucial to learn the difference between different malware types and malicious software viruses, study examples of them, and prepare solutions for protecting yourself.
What’s the Difference?
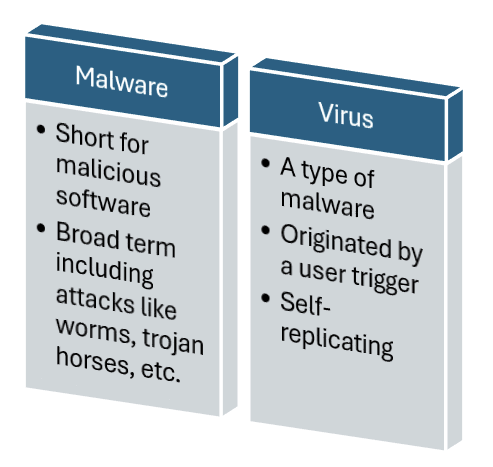
Malware is a broad term that refers to any malicious software.
Viruses are a smaller subset of malware; this name is used for any self-replicating, user-triggered attack.
Types of Malware
Malware comes in many different shapes and sizes, from viruses to worms to Trojan horses. It is also important to remember that any particular malicious program can fall into multiple categories. For example, a backdoor can be set up via a worm. If that sounds like a bunch of mumbo jumbo, don’t worry! Let’s look at a few particulars of each so this becomes a bit clearer.
Viruses
One of the cornerstones of a virus’s definability is its ability to self-replicate. But how could harmful software do this practically, self-replicating itself across an environment until security is compromised? Let’s take a closer look.
A computer virus typically consists of three parts:
- the infection mechanism (how it spreads)
- the payload (its intended action)
- the trigger (what activates the payload).
To me, these concepts are easiest explained in reverse order. A trigger, for example, can be something straightforward like meeting a specific date on the calendar before activating a payload. A simple instance of what a payload might do is deleting files across an infected computer. Then comes the infection mechanism, the most complex and vital of the three pieces.
One of the most straightforward examples of an infection mechanism I’ve seen is using Microsoft Word documents. Word can create and run macro programs, turning multi-step operations into simple button clicks. Say you create a document once a week that includes a table. It would be great to have a pre-formatted, pre-titled table populated each week without resizing it. This action could be turned into a macro where you lay out the steps once, and the entire process is repeated with a simple button trigger each time you need a new table. Do you see where we’re headed? Viruses can be built upon these Microsoft Word macros, specifically by creating a file that runs a macro when opened and transmitting those harmful files to unknowing users.
Safety Tip!
Since many forms of viruses can infect your computer when you open a document from an untrusted source, always verify email attachments by double-checking the sender’s email address for misspellings.
Trojan Horses
This malicious code disguises itself as a standard application or process that someone might use daily. For example, let’s say Kevin is reading an article online. After reading the article’s end, he scrolled and saw links to new articles. Here’s where some social engineering and the Trojan horse come in:
One of the articles shows an image of someone grasping their lower back, and the headline reads. “3 Reasons Your Lower Back Hurts”.

Coincidentally, Kevin also has lower back pain and thinks this article would be worth reading. He clicks on the article. Then, out of nowhere, his browser rushes to a new website he is not familiar with. A download appears in the top right corner of his screen.
“That’s weird. I’ve never had to download anything on this news site before…” Kevin thinks to himself. Boom, his computer is compromised by one click on that download link.
Taking a step back with the ideas of best safety practices in mind, it is easy to see where the misstep occurred. Normally the way Kevin operates while reading articles is to read, scroll, click, read, scroll, click, sip coffee, read, scroll. So, when an article that plays to his own problems comes up, click it is! The Trojan horse in this situation is the fake lower back pain article, with the goal of the bad actors being to get that download on someone else’s computer.
Safety Tip!
In the future, Kevin, be safer when doing your morning reading. Even tricks like hovering over the article so he could see the URL of where it was taking him might have helped avoid this situation altogether.
Worms
The line between viruses and computer worms is thin, but on a basic level, viruses usually self-replicate through mechanisms related to an infected application, whereas worms self-replicate using a computer network. Often, once a worm has duplicated itself across a network, the volume of normal tasks an affected organization can do drastically decreases as the worm’s activity consumes bandwidth.
While the average computer user may know some tips and behind-the-scenes tricks for handling the applications on their computer, computer networking is a highly technical field, so concepts like packets or protocols are not as broadly discussed. Spotting a bunch of pop-up windows on your computer after an application gets infected is a lot easier than knowing if your less-than-optimal internet download speeds are due to a cyber attack or simply more people showing up to the office on that day.
Safety Tip!
The critical factor for protecting yourself from computer worms is ensuring that your computer stays updated with the latest patches/updates.
Ways to Stay Safe
Malware protection takes various forms, from antivirus software to security training to ensuring your computer applications are patched regularly. Often, each solution has its own hurdles to entry: complicated setup processes or little support once you purchase a security solution are far too common.
Patch My PC is different.
When a vulnerability is revealed for applications in the Patch My PC catalog, customers can save crucial time by automating the packaging of third-party applications and updates in Intune. Your team can eliminate thousands of hours of packaging time per year while being able to configure environment-specific customizations to control your application settings. Does it sound like another implementation hurdle?
Our Customer Engineering team is far above the industry average in terms of the caliber of support we provide, both pre- and post-purchase. Check out some customer testimonials for more information on us, or sign up for a one-on-one demo today to learn how thousands of enterprise companies are staying safe with Patch My PC.