
Imagine you are Scotty, the Chief Engineer aboard the Starship Enterprise, a vessel where every component has been meticulously designed, rigorously tested, and fine-tuned to perform flawlessly at warp speed.
Now imagine stepping away for well-earned shore leave. While you are gone, Captain Kirk, ever eager to push the limits, decides to “upgrade” the warp drive by installing new components he picked up from a Pakled freighter. The Pakleds, well-meaning but not exactly known for their technical expertise, had cobbled together parts from across the galaxy with little understanding of how they truly worked.
At first, everything seems fine. The Enterprise can even outrun a Klingon bird of prey in a straight chase. But without proper schematics, thorough testing, and trusted engineering standards, cracks start to appear. Systems that were once seamless begin to behave unpredictably. Power fluctuations ripple through the ship. Critical subsystems falter under stress. What looked like a quick improvement turns into a growing liability, putting the entire crew at risk when it matters most.
This is exactly the risk organizations take when they rely on community-maintained software catalogs as their primary source for application management. What seems like a shortcut to speed and convenience can quickly undermine the stability, security, and reliability of the entire enterprise.
Trust Is Earned Through Process and Validation, Not Popularity
Consider how we’ve come to trust Microsoft’s update ecosystem. From the early days of Windows Update and WSUS through today’s more sophisticated Configuration Manager and Azure Update Manager solutions, Microsoft has built credibility with us – despite occasional missteps like the circular dependency nightmare of the 2019 Servicing Stack Updates.
This trust stems from Microsoft’s substantial investment in engineering teams who systematically validate updates across thousands of hardware and software configurations.
What’s noteworthy isn’t that Microsoft’s update process is flawless (it clearly isn’t), but rather that organizations still trust it enough to deploy updates enterprise-wide. This trust has been earned through transparency, consistent remediation of issues, and the establishment of multi-stage validation processes that catch most problems before they reach production environments. We trust that when an update appears in the Microsoft Update catalog, it has been through rigorous testing for stability, security, and compatibility.
This level of assurance is not just a nice-to-have, it’s a necessity that allows enterprises to safely automate large-scale deployments without second-guessing the behavior and outcome of every update.
Despite Microsoft’s extensive resources, occasional issues still arise with their updates (another hat tilt to SSU’s). This highlights a crucial point – if even Microsoft, with its vast engineering teams and testing infrastructure, can face challenges with updates they directly produce and control, imagine the vastly higher risks from community repositories with volunteer maintainers and no formal validation processes.
Professional third-party application curation demands even greater care and elevates validation and testing to a specialized discipline. A well-managed software catalog enables enterprise-grade verification across the complex ecosystem of third-party applications, delivering the stability and security that community repositories simply cannot match.
The Temptation Of Easy Wins
You’re stretched thin, juggling too many responsibilities while leadership keeps piling on more demands. Then it happens – that persistent marketing cookie that’s been lurking in your browser cache finally catches you at your most vulnerable moment. Suddenly, those bold promises about a new patching solution with access to a gazillion apps sound like salvation rather than a sales pitch.
It’s a familiar scenario. Both vendors and community solutions that rely heavily on crowdsourced repositories dangle the irresistible carrot of “massive software catalogs” with tens of thousands of applications available at your fingertips. The numbers are impressive, the interface can look slick, and the convenience factor is undeniable.
No wonder so many experienced IT professionals take the bait when it comes to decision making for a patching solution. When you’re drowning in work, the promise of simplifying just one aspect of your job is almost impossible to resist.
Beneath the Surface: What You’re Really Getting
When you adopt a solution that relies on community repositories as your primary patching solution, you’re not just accepting convenience, you’re entering into a trade-off that deserves careful consideration. Technology giants have grappled with this problem for years. Microsoft’s efforts with MSIX, and their newer Enterprise Application Management initiative reflect just how hard it is to solve third-party application management at scale.
A critical question often overlooked is this – “Who is actually maintaining these packages?”
While community repositories can provide access to a wide range of applications, it’s important to understand their limitations in the context of the enterprise:-
- Varying Maintenance Models
Many packages are maintained by volunteers and individuals who donate their spare time. While these contributors are often passionate and skilled, they typically lack the resources, testing environments, or enterprise experience to maintain production-grade standards consistently across thousands of applications. - Inconsistent Quality Assurance
Without formalized QA processes, quality can vary dramatically between packages. Some may be meticulously maintained, while others might receive minimal attention or testing. - Limited Enterprise Accountability
Community repositories generally operate without service-level agreements, formal support channels, or guaranteed response times for critical issues – elements that enterprise environments depend on for operational stability. - Supplementary Role
Community repositories can serve as valuable supplementary sources for non-critical applications or specialized tools, but relying on them as your primary patching mechanism for mission-critical software introduces unnecessary risk. - Ticking a Box
It’s relatively easy to tick a box in an automation pipeline and mark an update as “successful” when it installs without obvious errors, but this surface-level validation often fails to consider crucial enterprise concerns. Were major version upgrades honoured appropriately? Were different product variants considered? Were dependencies installed? Did the app need to be closed for the updated to install successfully?
Organizations must evaluate whether “community-maintained” meets their requirements for accountability, consistency, and enterprise readiness. There’s a significant difference between leveraging community resources as one component of a patching strategy versus making them the foundation of your security posture.one component of a patching strategy versus making them the foundation of your security posture.
When Minutes Matter, Days Are Lost
Security updates are a race against time. Every minute between a vendor’s patch release and your organization’s deployment represents a widening vulnerability window, making timely and informed decision making critical.
Specifically, but not exclusively, community repositories can lag severely behind vendor new version releases. Failing to push out third-party software updates quickly can lead to difficult conversations with your security team, especially when they trace a breach back to a known vulnerability that remained unpatched because you relied on an unpredictable update source.
Even worse, if a vendor releases an update that breaks key functionality, will anyone quickly identify and immediately pull that version from the community repository to prevent it from spreading across your organization?
Inherent Risks in Crowdsourced Repositories
Community repositories, like WinGet, can face inherent risks that professional curation directly addresses. Consider one real-world case of EarTrumpet. In 2021, developers discovered their manifest had been “incorrectly altered” without their knowledge, causing development binaries to be distributed to all WinGet users for over six weeks. When the issue was reported, the developer noted they “legally owned the manifest” yet had no control over changes made to it.
https://github.com/microsoft/winget-pkgs/issues/7836
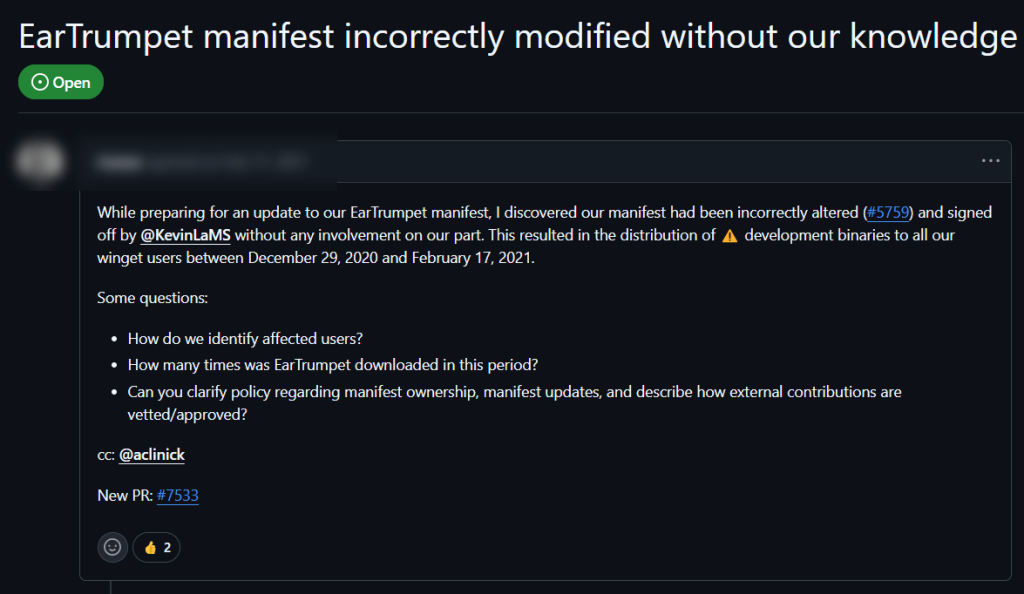
This incident outlines one of the fundamental weakness in crowdsourced models. Even with WinGet’s improved security protocols and validation process today, including virus scanning and human review, the underlying challenges persist. Updates remain, primarily, community maintained – meaning security patches depend entirely on volunteers or publishers themselves. This creates inconsistent response times and unclear accountability when issues arise.
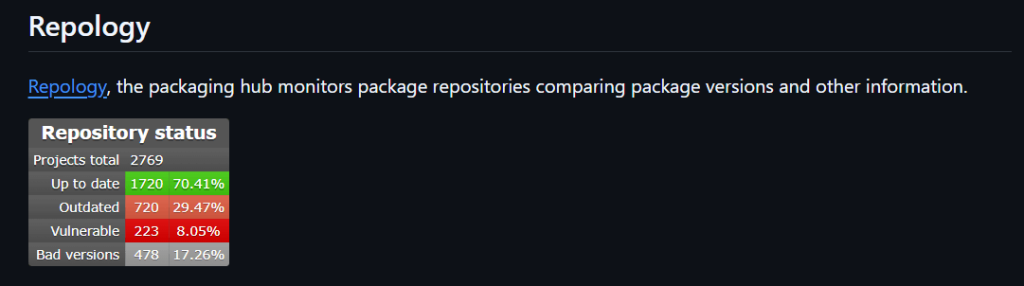
Its also note worthy to mention https://repology.org at this point. Repology, monitor several package repositories, including WinGet, evaluating package versions and identifying potentially vulnerable software. Microsoft has a “Repology” badge in the WinGet repository README, which publicly displays metrics including “vulnerable” packages associated with known CVEs.
https://repology.org/repository/winget
WinGet intentionally supports multiple versions of the same software that might be installed side-by-side. This is particularly important for development tools like Python, .NET runtimes, and Java SDKs where developers often need to maintain multiple versions of an app simultaneously.
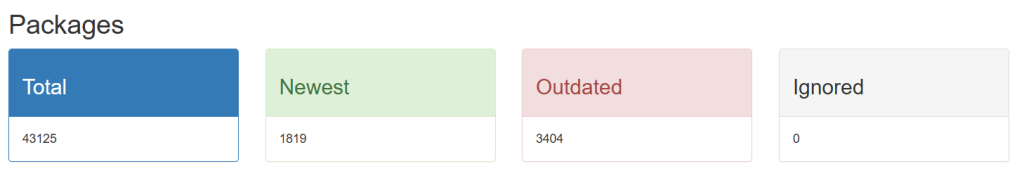
Crowdsourced package managers can facilitate the deployment newer versions alongside existing ones rather than replacing them entirely. This “side-by-side” installation approach creates invisible security gaps. It means that even after upgrading to the latest version, vulnerable binaries from previous installations may remain on your system. While multiple versions are sometimes necessary in development environments, they require careful management and scrutiny in a production setting.
Java is a perfect example of this problem. When newer versions are installed, older vulnerable Java runtimes often remain on disk, potentially exposing systems to known exploits. Organizations relying on community-maintained repositories must implement additional security processes to verify that outdated components are completely removed and not just supplemented with newer versions.
The Unseen Testing Gap
Another significant challenge with crowdsourced packages is what you cannot see, the testing gap.
A new update might pass a virus scan and install on a test machine without throwing an obvious error. Great – lets install it. But wait, those are only the first steps. In a real enterprise, there are other critical phases in the quality assurance cycle and questions to answer:-
- Did the application install silently, without popping up any prompts to the user?
- Was the exit code captured correctly, and was it handled the right way?
- Did the new version properly upgrade the old one, or did it install side-by-side (which some vendors allow)?
- Was any special scripting needed to make the upgrade succeed?
- Does the package properly patch minor versions without jumping devices up to an unintended major version? This is something that could be disastrous for sensitive software like VPN clients.
- Are updates classified correctly? Are updates that address specific CVEs classified as Critical for example?
It is not guaranteed that applications in community repositories are tested for these things. Real regression testing is crucial for any update released to a software catalog. Without any of the above validation, using crowdsourced updates is a gamble. Sometimes it works just enough to give a false sense of security. Sometimes it quietly cripples your environment and by the time you notice, the damage is already done.
We Are Doing It Ourselves: A Free Lunch
Some organizations don’t even opt for a third-party solution at all and rely solely on harvesting community software catalogs and scripting there way to compliance.
You should not underestimate the operational cost of manually maintaining third-party applications. The monitoring process alone is challenging and time-consuming. Simply becoming aware that a vendor has released an update requires constant vigilance across multiple channels. Once identified, enterprise environments typically require around 5 hours of work per application to properly handle an update. This includes downloading the installer, testing it thoroughly in isolated environments, packaging it correctly for deployment, and finally pushing it out to endpoints. Each step introduces potential complications and delays.
If you manage a conservative 100 applications, and each vendor releases just 3 updates per year, the math quickly adds up:
5 hours × 100 applications × 3 updates per year = 1,500 hours annually.
Without professional patching solutions, managing third-party updates can consume thousands of hours each year, not including the additional time needed to monitor vendors, manage exceptions, troubleshoot failures, and respond to unexpected issues. And the more applications you support, the larger this operational burden becomes. This is precisely why organizations turn to professional solutions that dramatically reduce this time investment.
See how much time you can save with the Patch My PC Return on Investment Tool!
Feature Benefits and ROI – Patch My PC
Compliance: The Invisible Minefield
Compliance frameworks like SOC 2, ISO 27001, HIPAA, PCI DSS, and Cyber Essentials impose strict requirements for controlling, validating, and documenting the sources of third-party software.
Leveraging community repositories alone will not provide the level of transparency or assurance needed to meet these standards.
If your organization is audited, you could be expected to demonstrate:-
- Who packaged each critical application
- What testing was performed before deployment
- When vulnerabilities were identified and how they were addressed
Using a professionally curated software catalog does not automatically fulfil all compliance requirements, but it significantly strengthens your ability to answer these questions. A curated software catalog enables validation of update behaviors through thorough assessment, testing, and documentation, offering a level of assurance and traceability that community repositories typically cannot match. In regulated environments, these are not optional questions; they are basic expectations. match. In regulated environments, these are not optional questions – they are basic expectations.
- SOC 2 Trust Services Criteria
CC3.4 – OSO Principle 9: The entity identifies and assesses changes that could significantly impact the system of internal control
Requires organizations to manage risks from vendors and suppliers
https://www.aicpa.org/resources/article/trust-services-criteria - ISO/IEC 27001/2022
Annex A.15.1: Information Security in Supplier Relationships – Mandates control over third-party provided services and software
ISO/IEC 27001:2022 – Information security management systems - HIPAA Security Rule
164.308: Requires the implementation of security measures to reduce risks and vulnerabilities to a reasonable level. Requires covered entities and business associates to implement security measures to reduce risks and vulnerabilities to a reasonable and appropriate level
https://www.hhs.gov/hipaa/for-professionals/security/guidance/index.html - PCI DSS 4.0.1 Requirements
6.3.2 and 12.8: Requires documentation of software vendor relationships and patch management processes
https://docs-prv.pcisecuritystandards.org/PCI%20DSS/Standard/PCI-DSS-v4_0_1.pdf - Cyber Essentials Technical Requirements (2022 update)
Mandates the use of only licensed, supported software from trusted sources
https://www.ncsc.gov.uk/cyberessentials/overview
Professionally Curated Catalogs
Professional curation offers a fundamentally different experience. Instead of relying on volunteerism and luck, a curated software catalog, such as that from Patch My PC, delivers key benefits like:-
- Quality Over Quantity
- Unlike a company that prioritizes inflated software catalog size for marketing purposes, a better approach centers on delivering enterprise-ready applications that meet rigorous quality standards. A carefully vetted software catalog of thoroughly tested applications provides significantly more value than a huge repository of uncertain quality.
- Continuous Monitoring
- Professional teams track vendor updates across multiple platforms in real-time, ensuring nothing slips through the cracks. Package integrity is verified, vendor sources are trusted, and updates are proactively managed.
- Comprehensive Testing
- Every package is tested across diverse environments, operating systems, and enterprise security tools, dramatically reducing deployment risks.
- Hash verification ensures that binaries are always sourced directly from the vendor, never from third-party mirrors.
- Silent installation parameters are validated, upgrade paths are tested, and known conflicts are carefully assessed.
- Enterprise-Tailored Configurations
- Deployments undergo full validation, with detailed logging enabled for audit and troubleshooting purposes.
- Common blocking processes are automatically handled to ensure successful installations.
- Where appropriate, automatic updates are disabled to allow organizations to maintain complete control over the update cadence.
- Pre/ Post-scripts can be leveraged to maintain customizations and prepare devices before and after deployments, ensuring consistent and predictable behavior across enterprise environments.
- The curated software catalog and customization capabilities offers seamless integration across multiple platforms, including Configuration Manager, WSUS, and Intune.
- Deployment of third-party updates using modern strategies like Update Rings across your enterprise and optionally leverage your existing Microsoft Windows Autopatch Entra ID groups you already use for first-party patching.
- Rapid Security Responses
- Vulnerability patches released by vendors are assessed, packaged, and published to the software catalog immediately, often the same day, not weeks later, enabling organizations to drastically reduce vulnerability windows across their environment.
- Enterprise Support
- Enterprise environments demand more than just software updates, they require expertise, accountability, and rapid problem resolution. Organizations cannot afford to rely on vendors who treat patch management as a secondary product or a side offering.
- Comprehensive solutions come from teams who live and breathe enterprise IT. Teams that understand the complexity of large-scale environments offer you better reliability, respond faster to issues, and innovate with the real-world challenges of security, deployment, and compliance in mind.
- Choosing a partner dedicated to patch management, who doesn’t rely on crowdsourced package managers as their primary software catalog, ensures a higher standard of testing, better support experiences, and a stronger foundation for long-term stability.
- Customer Driven Innovation
- True innovation does not come from rigid product roadmaps. It comes from listening directly to customer needs and evolving products and features to meet real-world challenges.
- The most effective patch management providers continuously adapt based on customer feedback, delivering features that create tangible business value instead of chasing technical trends or vanity features.
Professional curation is not about chasing software catalog size for the sake of marketing numbers. Patch My PC continues to add 50-100 new applications to our software catalog each month, but every addition is based on real-world requests from enterprise organizations. We prioritize meaningful expansion driven by customer needs, ensuring that every new application meets strict standards for quality, security, and enterprise deployment readiness. We are not just throwing in different apps and versions to inflate the software catalog artificially.
Expertise That Can’t Be Automated
While automation plays a vital role in modern patch management, there’s an irreplaceable value in human expertise and experience. At Patch My PC, our software catalog team represents a collective repository of tribal knowledge built through years of hands-on experience with thousands of applications across diverse enterprise environments.
This accumulated wisdom creates value that no algorithm or community repository can match, with key benefits like:-
Institutional Memory
Our team maintains detailed knowledge of application behaviors across versions – remembering that Adobe Reader 10.2 had a critical silent install parameter change, or that a certain VPN client’s 2023 Q2 update caused authentication issues in specific configurations. This historical perspective gives our team a better understanding of what to look for in new releases which helps to prevent organizations from repeating past deployment pitfalls.
Vendor Relationship Intelligence
Through years of working with software vendors, our team understands the nuances of different vendors’ release patterns, documentation practices, and common deployment challenges. We know which vendors frequently change their installation frameworks, and which ones require special handling for enterprise environments. We also regularly work with vendors to help them improve their installers so they can be deployed successfully across the Enterprise.
Pattern Recognition
Human experts excel at spotting subtle patterns across seemingly unrelated applications. Our software catalog team can identify potential compatibility issues between applications that automated testing might miss, applying insights from one application family to anticipate problems in another.
Judgement Calls
Not every decision in patch management has a clear right answer. Captain Kirk never solely relied on Data (pun intended), he relied on collective knowledge (not from the Borg) to make clear decisions. Some updates require weighing security improvements against potential business disruption. Our dedicated software catalog team makes these impact analysis judgment calls based on years of experience and relevant data, helping many organizations navigate these complex trade-offs with confidence.
Continuous Knowledge Transfer
Our team don’t just package applications, they document their findings, create knowledge bases, and build processes that improve how updates are handled in the future. This institutional knowledge becomes part of our service, benefiting all customers.
While automation and AI will continue to advance, the human element, real professionals who understand not just the technical aspects but the business implications of patch management, remains the cornerstone of truly enterprise-grade solutions.
Conclusion: Rethink the Real Cost of Convenience
The market is seeing an increase of products promising easy third-party application management, leveraging community software catalogs as their primary update source. Even Microsoft’s own Enterprise Application Management solution struggles in this space – showing that this technology area is anything but easy to tame.
The real question isn’t whether you can afford a professional solution. It’s whether you can afford the risks of continuing without one. Remember, “Crowdsourcing gets you fast. Curation gets you safe”.
Ready to transform third-party patching in your organisation with Patch My PC? Book a Demo.
