It’s well known that Microsoft Entra ID supports a maximum of 200 BitLocker recovery keys per device. Once this limit is reached, new recovery keys cannot be escrowed to Entra.
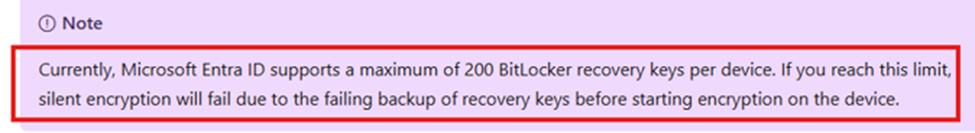
Silent encryption will fail if the BitLocker policy enforces key escrow before enabling encryption. Since BitLocker requires a successful backup of the recovery key before proceeding, encryption does not start, leaving the device unencrypted until we remove the device object from Entra…. which is a horrible fix.
This blog will show you what is coming and how Microsoft is going to fix this weird BitLocker issue!
The Old Way: A Broken Process
When looking back at the old days, the moment your device hit the 200-BitLocker Recovery key limit, your options were pretty limited.
The only way to fix it was to:
- Delete the entire device record from Entra, wipe out all recovery keys, and force a full, clean install of the device.
- Disable silent encryption. The moment you turn on encryption, you need to manually extract/save the recovery key to a nice PDF.
Neither option was practical or scalable. The fact that this issue existed for over five years without a proper solution made it even worse.
But then, while analyzing changes in a recent Windows Insider Preview build, we stumbled upon something interesting. As shown below, we noticed something called: Cleanup AAD Stale RPs for Max Limit.

We had to look closer; this felt like the fix we were all waiting for!
How We Discovered the Bitlocker Recovery Key Fix
I started looking at multiple DLL files when I spotted that new feature. It was obvious that I first tried to open the fveapi.dll and the bdesvc.dll, but neither of them showed me traces of that new feature. When opening Procmon and manually escrowing the recovery key to Entra, I stumbled upon the file called fveskybackup.dll.

Inside this fveskybackup.dll, we indeed found new functions related to BitLocker recovery password cleanup. Using IDA Pro, we identified a key function:
Feature Flag: BitLocker Cleanup for AAD Stale Recovery Passwords
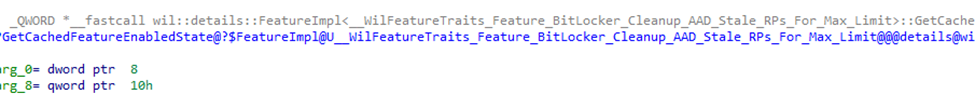
WilFeatureTraits_Feature_BitLocker_Cleanup_AAD_Stale_RPs_For_Max_Limit
This function retrieves the cached feature state and determines if the cleanup behavior should be enabled. In other words, Windows now has an internal feature flag that controls the automatic deletion of stale BitLocker recovery passwords in Entra when the 200-key limit is hit.
This confirms that Microsoft has built a toggleable mechanism for this feature, which explains why it wasn’t previously available.
How BitLocker Normally Uploads Recovery Keys to Entra
Before we discuss the new cleanup function, let’s first understand how BitLocker uploads recovery keys.
When BitLocker encryption is enabled with silent encryption, the recovery key is automatically backed up to Entra. Here’s what normally happens under the hood:
Pretty simple, right? If the policy enforces the key to be uploaded to Entra, FVESkyBackup start doing its job… but looking back at the escrow issue.
If the device has fewer than 200 recovery passwords stored, the upload succeeds.
If the device already has 200 recovery passwords stored, the upload fails—breaking silent encryption.
And that’s where everything went wrong in the past. But this new function changes that.
What We Found in fveskybackup.dll
Looking inside fveskybackup.dll, we discovered two critical functions:
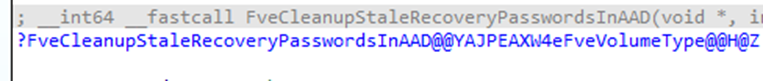
- FveCleanupStaleRecoveryPasswordsInAAD
- Identifies stale recovery passwords.
- Decides which ones should be deleted.
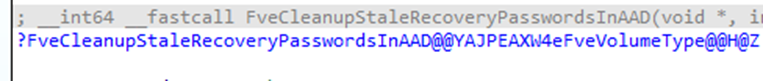
- FveDeleteRecoveryPasswordsFromCloudDomain
- Executes the deletion of stale recovery passwords in Entra.
- Removes 16 passwords per batch.
These discoveries suggested that Windows now automatically cleans up stale recovery keys when the upload fails. Before I started analyzing the code, I decided to test if my eyes weren’t playing jokes on me.
Rotating The Bitlocker Keys!
To see this Bitlocker Recovery Key Stale Cleanup feature in action, we wrote a PowerShell script that:
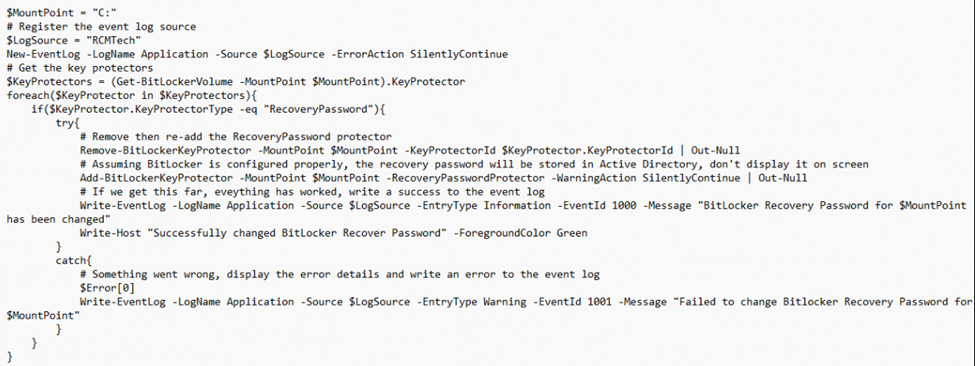
- Removed the BitLocker recovery Key.

- Uploaded the new Bitlocker Recovery key to Entra.
- Repeated this process until we hit the 200 Bitlocker Recovery keys.
While this script was running, we kept an eye out for the Recovery Keys in Intune. Within about 10 minutes, we had 200 Recovery Keys escrowed… nice right?
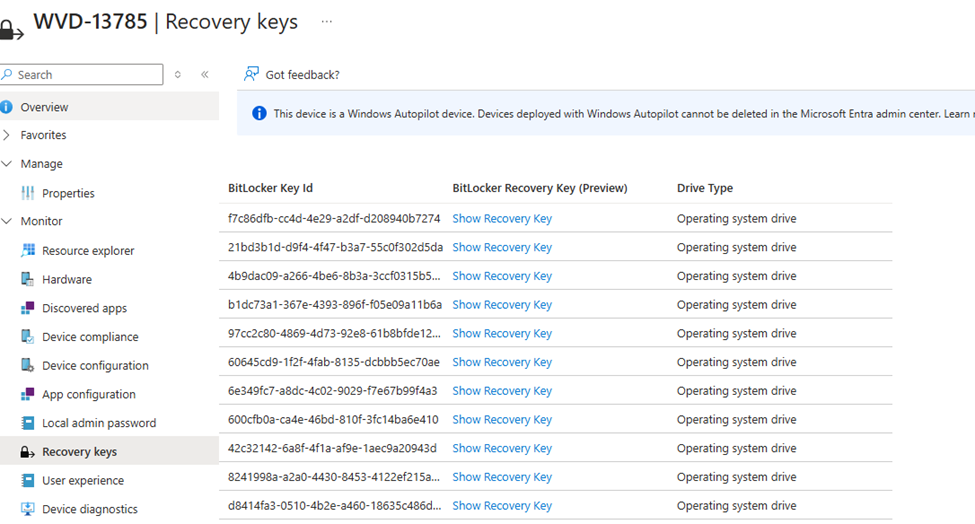
In older Windows builds, this would cause silent encryption to fail completely. But in this Insider Preview build, something different happened.
Stale Bitlocker Recovery Key Cleanup Kicking in
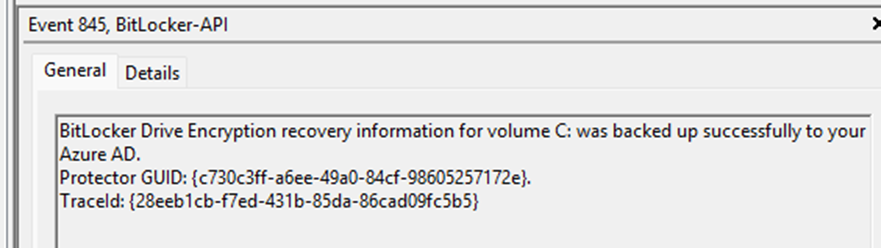
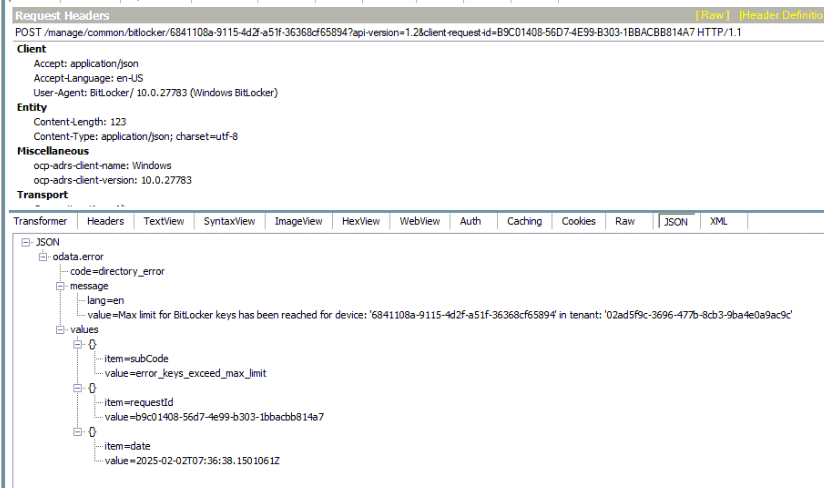
When Entra reached the maximum of 200 Bitlocker Recovery keys, something funny started happening. If the escrow hits the 200-key limit, it will fail to save BitLocker drive encryption information to your Azure Ad due to an error.
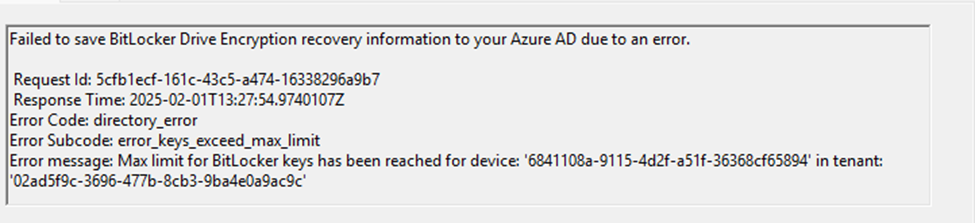
As shown above and below, the recovery key failed to be saved to Azure Ad because the maximum number of recovery passwords for this device has already been saved.
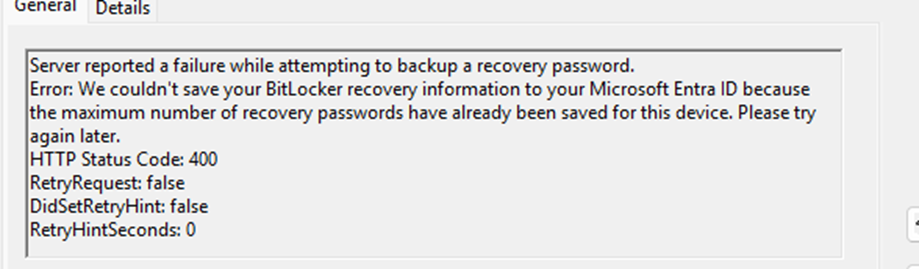
Exactly at this moment, some magic started to happen! The new Bitlocker Key cleanup function was automatically triggered when it reached the maximum number of saved recovery passwords (Bitlocker Recovery Keys). When this Stale Cleanup function is triggered, it will contact the service again, this time asking which stale Bitlocker Recovery keys exist.
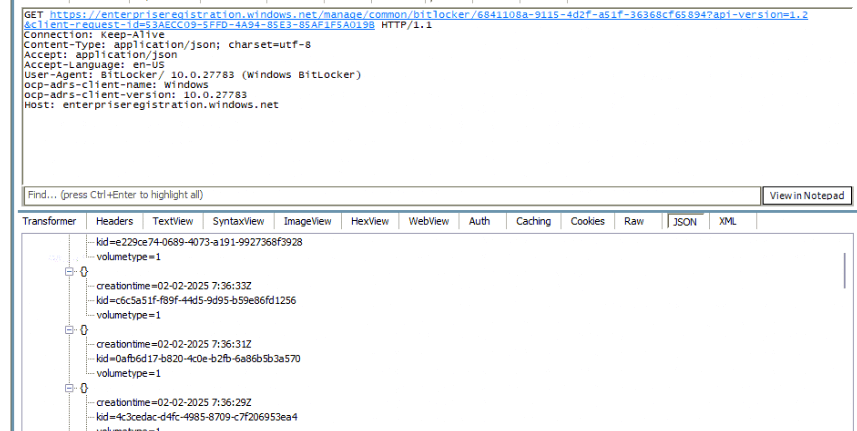
Once it determines which stale Bitlocker Recovery Keys are still lingering at the service, it will ask the service to start deleting old recovery passwords. From what I can tell, every time it cleans up state recovery passwords, it will clean up exactly 16 entries.
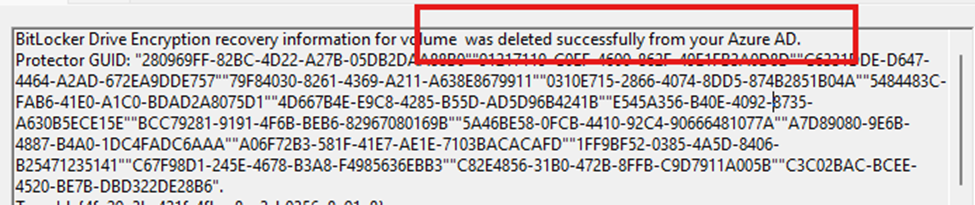
We can spot the same behavior when looking at Fiddler:
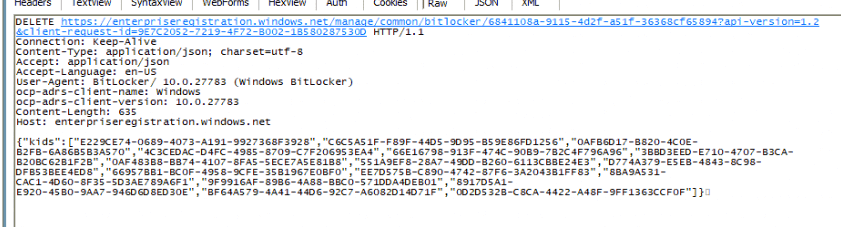
As shown above, it will send an HTTP DELETE request to the Microsoft Enterprise Registration endpoint (enterpriseregistration.windows.net), to remove stale BitLocker recovery passwords (KIDS) stored in Microsoft Entra ID.
Once enough stale Bitlocker recovery passwords were cleared, the new Bitlocker key upload process was retried, but this time, it succeeded.
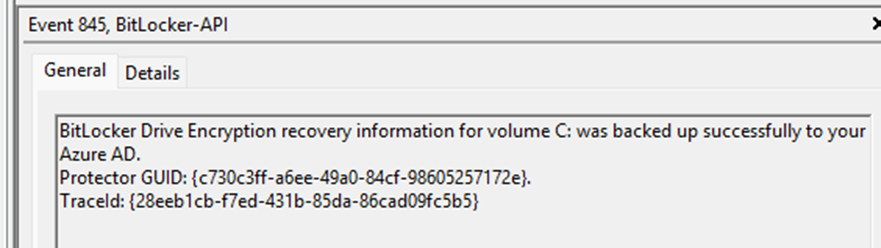
This confirmed that the cleanup process was now fully automated, and if we are even more patient, we will spot some automatic cleanup for the rest of the stale Bitlocker Recovery Keys. As shown below, the Bitlocker-Api Management event log showed me that it deleted all stale Bitlocker keys in a batch of 16.
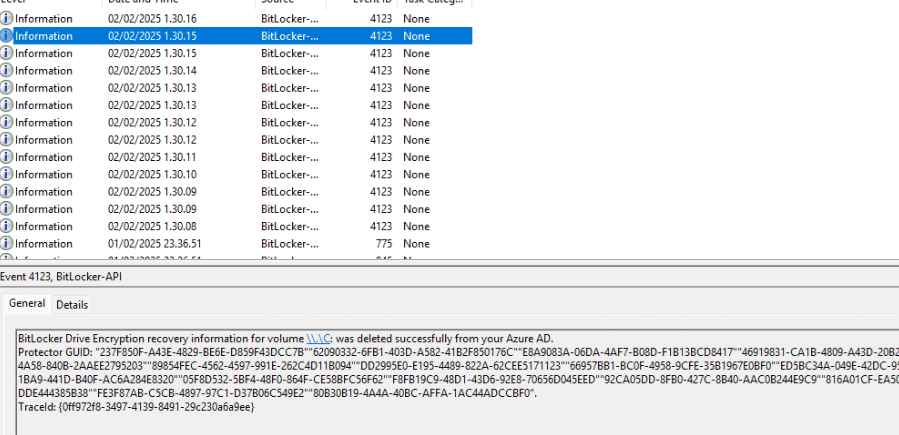
This is pretty amazing if you ask me, but I am not done yet!
Cleanup Stale Bitlocker Keys ETL trace
It was obvious that I also ensured I was running an ETL trace while trying to break the escrow again. As I mentioned in a previous blog, you need to know what to capture when you want to run an ETL trace.
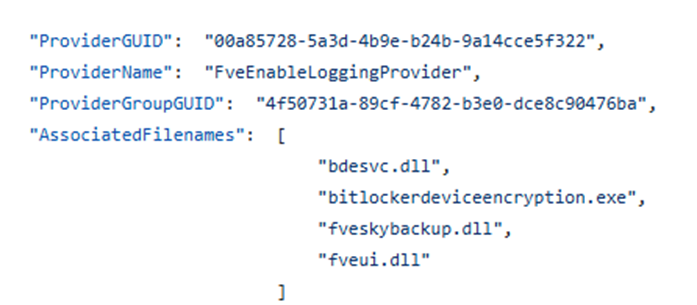
As shown above, I made sure to add the fveenableloggingprovider to the ETL trace, as that one contained the fveskybackup.dll.
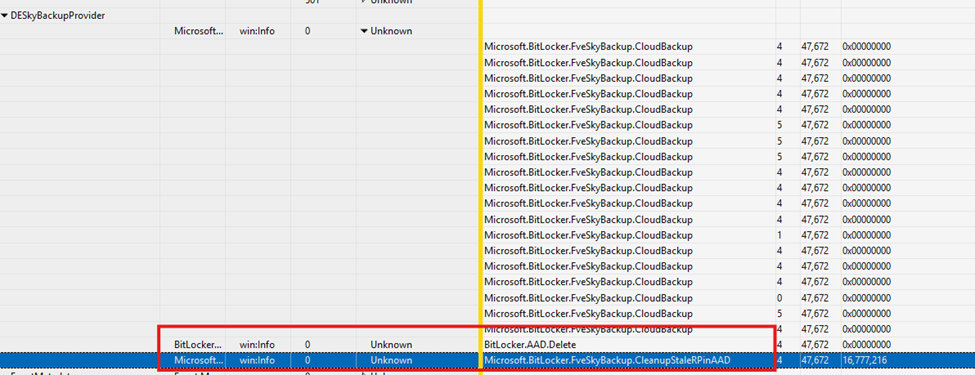
Looking at the flow, we indeed spot the same behavior. It will try to perform the FveSkybackup cloud backup. The moment it reaches the 200 limit, it will error out.
From there, the Cleanup Stale RP in AAD function will be launched! This feature will delete 16 stale BitLocker keys, and then the escrow can happen again!
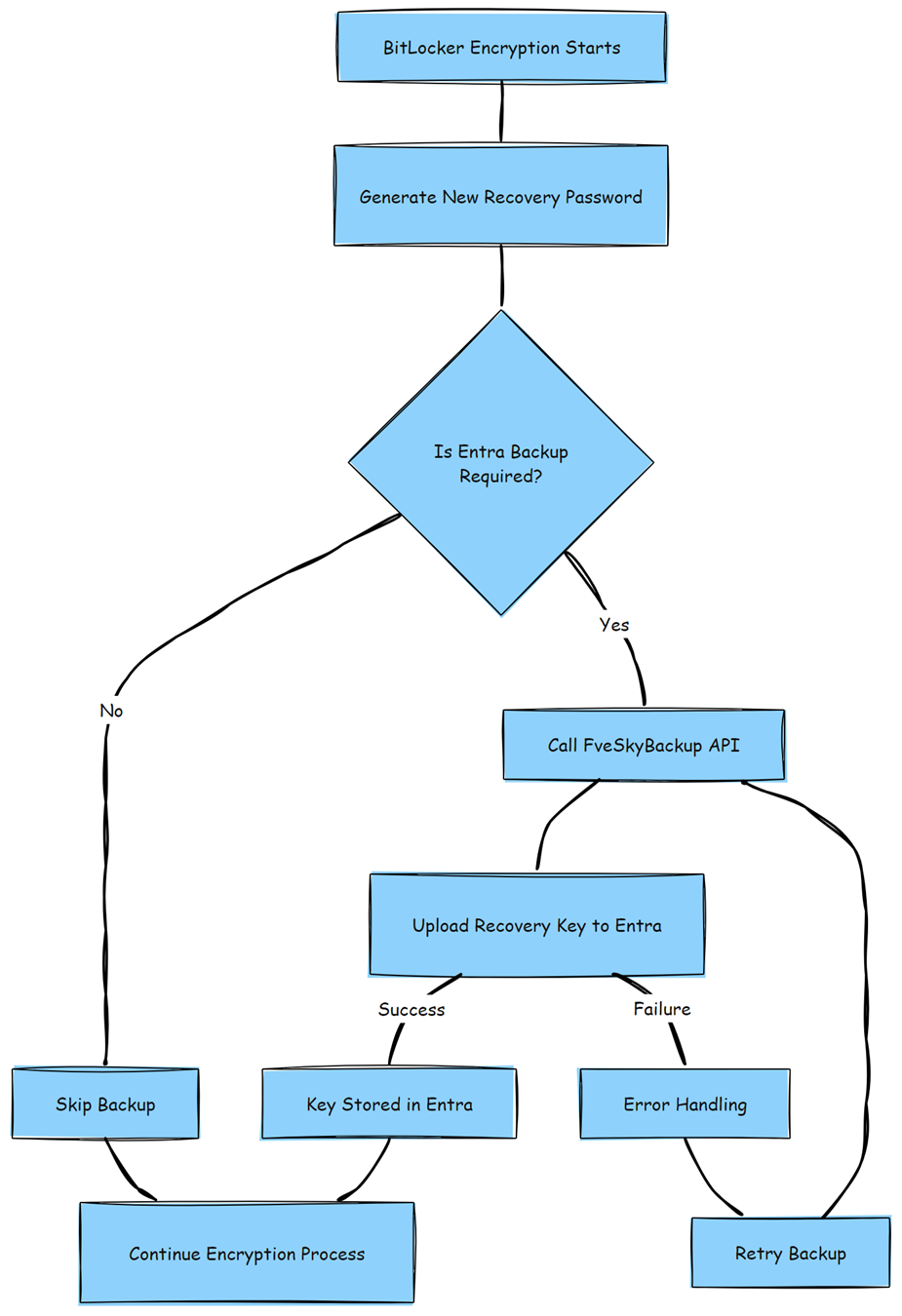
The Cleanup AAD Stale RP Mermaid Flow
With all this information gathered, I reopened the IDA Tool and started to work out the flow. As shown below, this is what will happen when this BitLocker_Cleanup_AAD_Stale_RPs_For_Max_Limit feature is enabled!!
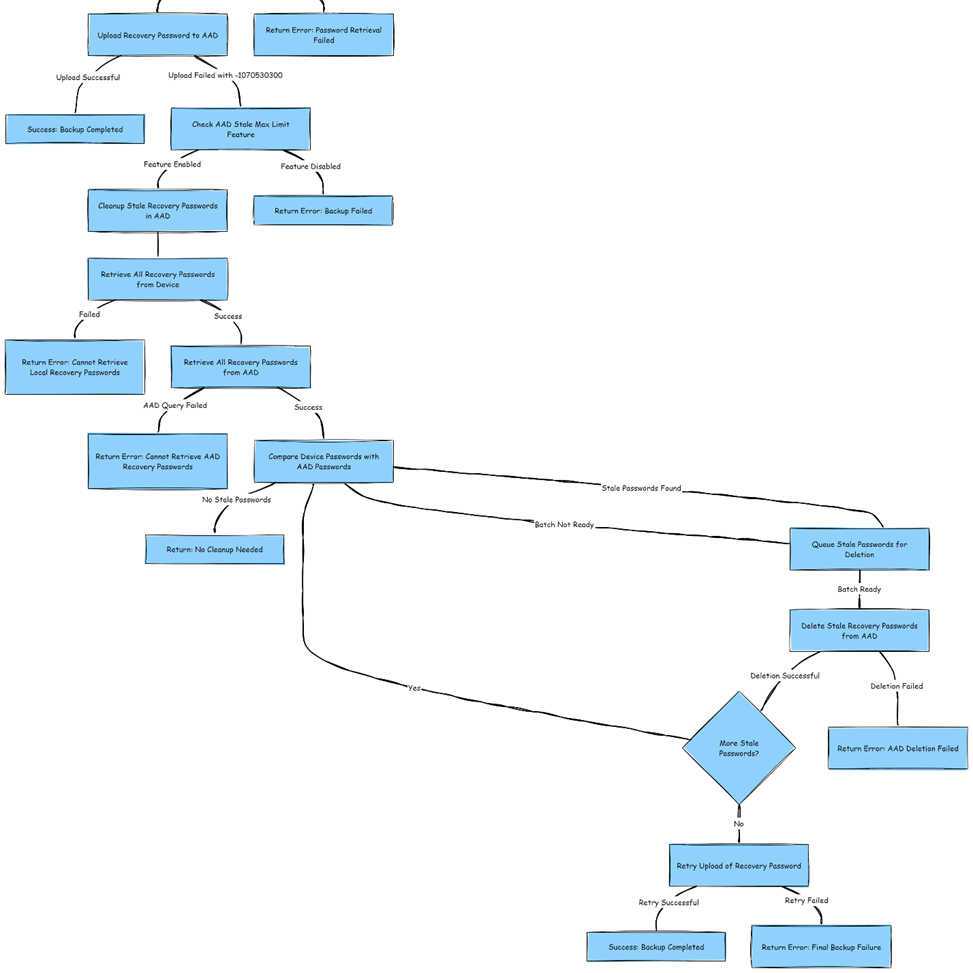
Summary of the Bitlocker Cleanup
- BitLocker tries to upload a new recovery key to Entra.
- If the 200-key limit is reached, the upload fails.
- If the cleanup feature is enabled, Windows retrieves and compares recovery passwords.
- Stale passwords are queued and deleted in batches (16 per batch).
- After deletion, the recovery key upload is retried.
- If successful, backup is completed. If not, an error is returned.
This means Windows now intelligently removes older recovery passwords when necessary, allowing silent encryption to continue working without manual intervention.
This got me wondering… what If I would use PowerShell to try to
Manually Retrieving and Deleting BitLocker Recovery Keys:
I was curious if we could somehow manually trigger the same cleanup process using PowerShell on the device itself. Why? well for starters, there is no Delete Graph command… which made me even more curious.
But then again, If Windows could delete stale Bitlocker recovery keys in Entra, could we do it, too? Time to find out.
Step 1: Retrieving BitLocker Recovery Keys
Our first attempt was simple: send a request to retrieve all BitLocker recovery keys stored in Entra ID for a test device.
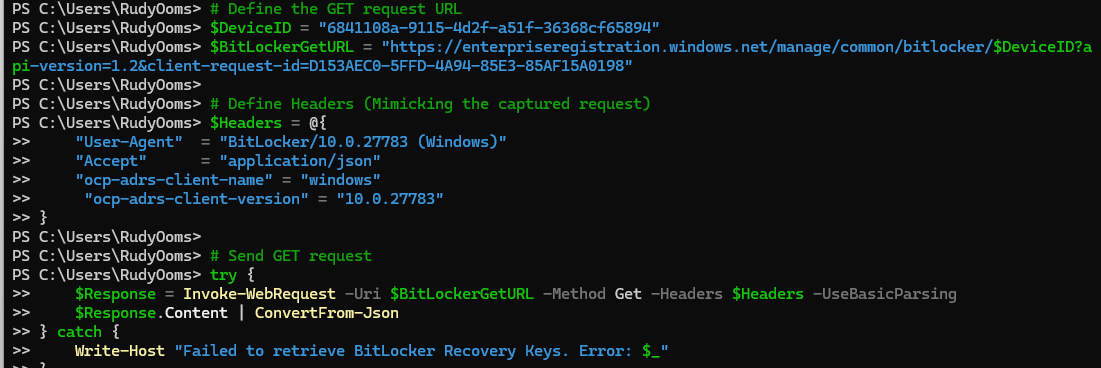
However, things didn’t go as planned. Instead of getting a list of keys, we ran into this error:
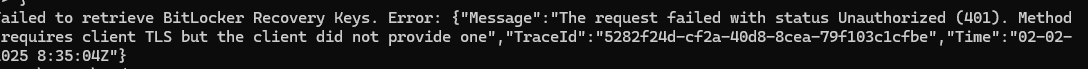
“The request failed with status Unauthorized (401). Method requires client TLS but the client did not provide one.”
This made it clear that Windows doesn’t just send a normal API request; it requires a specific client TLS certificate for authentication.
Step 2: Identifying the Missing Piece: The MS-Organization-Access Certificate
Digging deeper, we checked how Windows normally communicates with Entra ID for BitLocker operations. I guess that one is pretty obvious… The Entra certificate labeled “MS-Organization-Access” is used to authenticate these API requests.
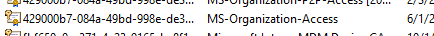
After locating this certificate in the local machine’s certificate store (using the thumbprint), we attached it to our request and tried again.
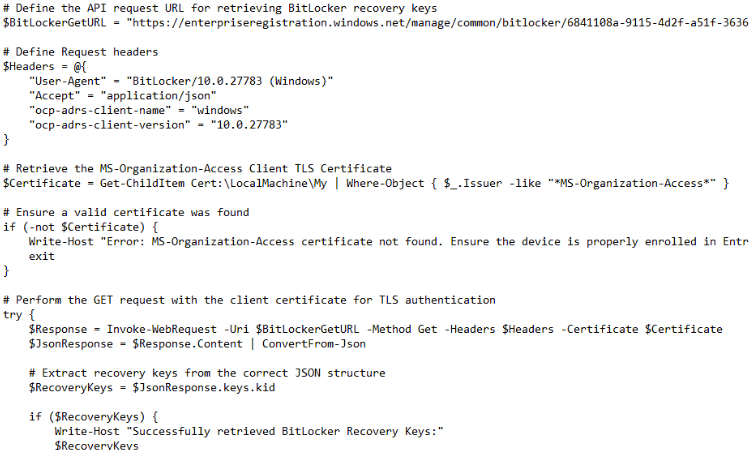
And it worked. This time, instead of a NOT AUTHORIZED error, we got back a full list of stored BitLocker recovery keys for the device, each with a unique identifier (kid).
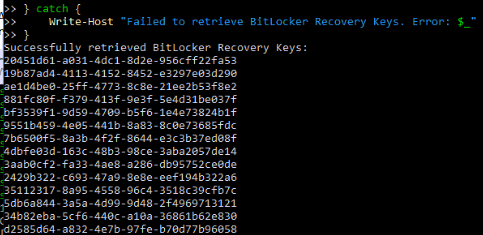
Step 3: Deleting Stale Bitlocker Recovery Keys
Now that we had successfully retrieved the stored stale Entra Bitlocker keys, the next logical step was to delete them all with a script. So, instead of a GET we added a DELETE.
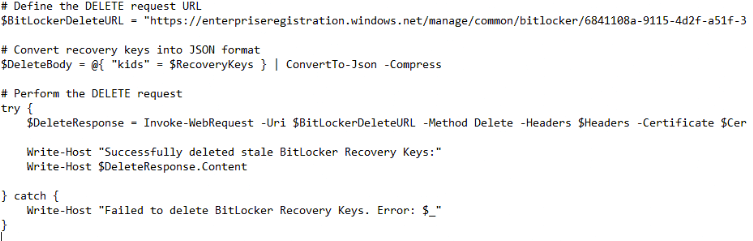
We formatted the request, as shown above, to remove all of them at once, but Windows had another restriction in place:
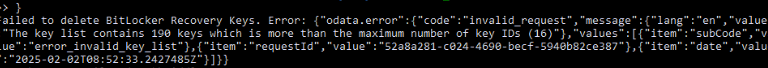
During this PowerShell web request to delete all of the stale Bitlocker Recovery keys, we also had Fiddler open and running. Looking at the response, it was pretty obvious that we were only allowed to delete 16 keys.
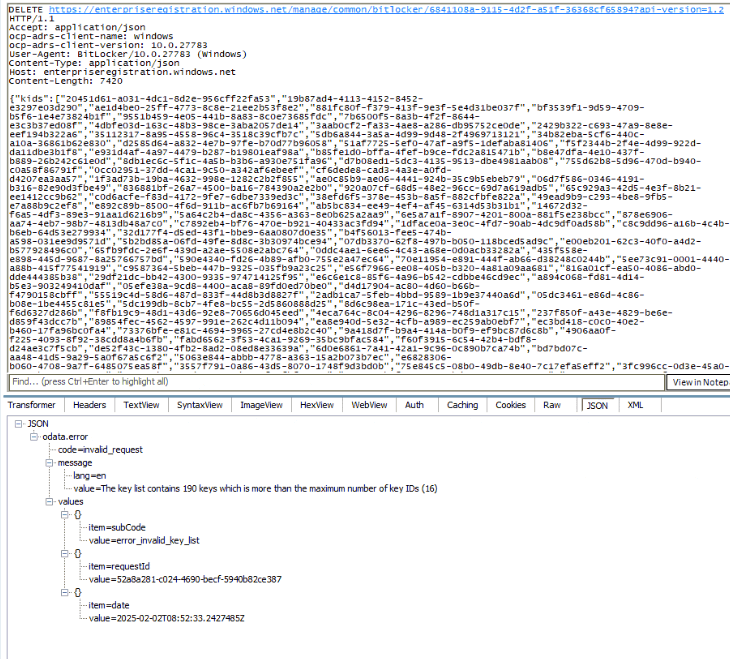
This aligned perfectly with the automatic cleanup function we discovered earlier, which also removes keys in batches of 16. So, if you want to delete them, you need to do it in batches of 16 from the device itself!
BitLocker Recovery Keys Deletion Script
Based on the blog and script above, Ben Whitmore created this awesome PowerShell script we could use to retrieve the Bitlocker keys from the Enterprise API with the use of the Entra Certificate. Once it has retrieved the Keys, it will (optional) delete the x oldest keys if the total count exceeds 200.
The best thing? You don’t need the latest insider preview to delete your device’s stale BitLocker Recovery Keys; you can use this script as Pro-Active remediation!!
Final Thoughts
For years, hitting the 200-key limit in Entra meant silent encryption would break, forcing admins to delete entire device records or disable automatic backups. It was a messy, inefficient process with no proper fix, until now.
With this new cleanup mechanism in the Insider Preview build, Windows can finally remove stale recovery passwords automatically instead of blocking new backups. If this feature makes it to general availability, it will eliminate the need for manual intervention and make BitLocker silent encryption far more reliable.
Key Takeaways
- Windows now has a built-in cleanup function for stale recovery keys in Entra.
- It deletes 16 recovery passwords per batch when the 200-key limit is reached.
- This feature is controlled via an internal feature flag (Feature_BitLocker_Cleanup_AAD_Stale_RPs_For_Max_Limit).
- If it reaches GA, IT admins will finally have an automated way to keep BitLocker working without manual cleanup.
I am very happy to see that, Microsoft fixed one of the biggest BitLocker headaches with this feature!
