Introduction to Windows Enrollment Attestation
In today’s world of escalating cyber threats, ensuring the security of devices within an organization is paramount. One critical technology that bolsters device security is TPM (Trusted Platform Module) attestation. But what exactly is Windows Enrollment Attestation AKA TPM Device attestation?
TPM attestation verifies the integrity and trustworthiness of a device’s hardware and software. It uses a dedicated TPM chip, which securely stores cryptographic keys, to attest that the device is in a known good state. This process is essential for ensuring that devices have not been tampered with and are running trusted software, and it plays a crucial role in enforcing security policies.
New Report Options in Intune
Microsoft Intune has introduced a new report option called Device Attestation that leverages TPM/ MDM attestation to enhance device security.
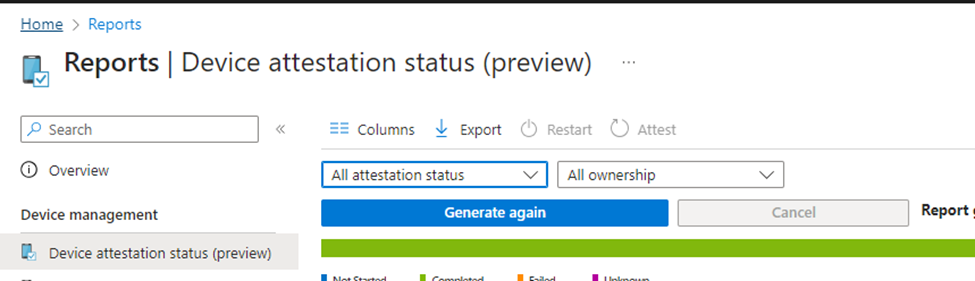
This new Intune/Windows feature allows IT administrators to generate comprehensive attestation reports, providing insights into the security posture of managed devices.
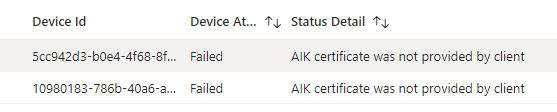
These reports are crucial for organizations looking to ensure that only devices meeting strict security criteria are allowed access to corporate resources. The Device attestation status reports in Intune help administrators identify devices that have successfully completed attestation and those that have not, enabling them to take security measures. This attestation report helps prevent potential security threats.
How Device Attestation Reports Work on the Device
Performing Windows Enrollment Attestation and generating the corresponding report in Intune involves several steps that are seamlessly integrated into the device management workflow. Here’s a detailed look at how this process works when users enroll devices into Intune:
1. Device Enrollment and Initialization
When a device is enrolled in device management (Intune), the enrollment process begins with the device requesting a security token from the Intune service. This token is essential for authenticating the device using multifactor authentication and initiating the attestation process.
2. Storing Keys in TPM
Once the device receives the security token, it retrieves the Intune Device Certificate. The critical step here is to store the certificate’s enrollment keys, including the private key, in the TPM chip. This step, referred to as UseTPMForEnrollmentKey, ensures that the keys are securely stored, protecting them from potential tampering.
3. Initiating Attestation via Microsoft Graph
Intune uses the Microsoft Graph API to initiate the TPM attestation from the MDM server. The specific API call, InitiateMobileDeviceManagementKeyRecovery, triggers the MDM Key Recovery and TPM attestation processes. This remote command is sent to the device, instructing it to perform the necessary attestation steps.
4. Device Recovery and Attestation
Upon receiving the command, the device executes the recovery process. If the Intune Device Certificate is not already in the TPM, the device recovers it to the TPM. Following this, the device performs the MDMClientCertAttestation with Intune, completing the attestation process.
5. Generating and Viewing Attestation Reports
After the device attestation is performed, the results are compiled into a comprehensive report. IT administrators can view these reports within the Intune portal, providing them with a detailed overview of the attestation status for all managed devices. The reports highlight which devices have successfully completed attestation and which have not, allowing administrators to enforce compliance policies effectively.
Visual Representation of the Windows Enrollment Attestation Flow
For a clearer understanding, here is a visual representation of the TPM attestation process in Intune:
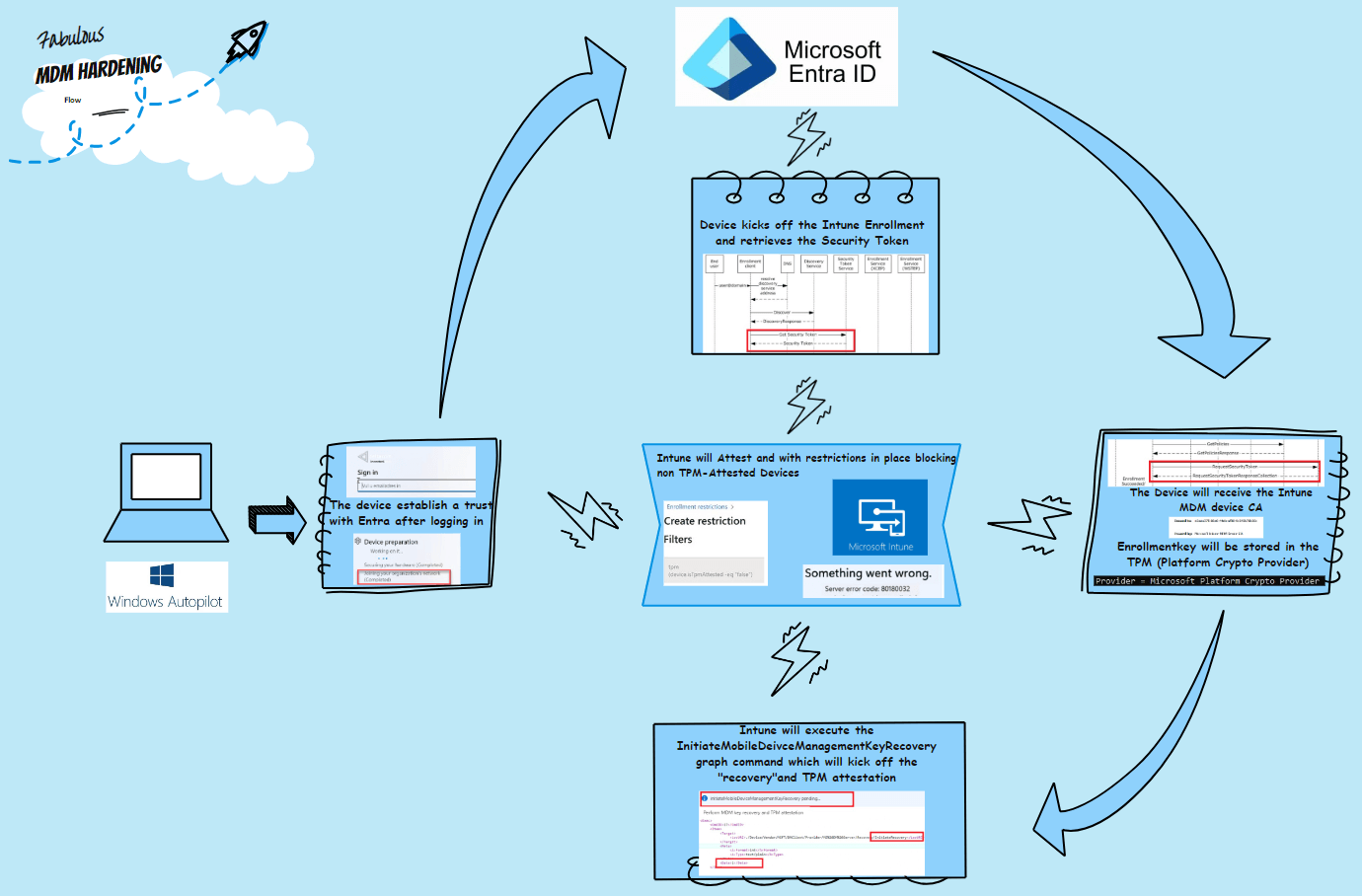
Step-by-Step Breakdown:
- Device Enrollment: The device requests a security token and starts the enrollment process.
- Key Storage in TPM: Enrollment keys of the certificate are securely stored in the TPM.
- Initiating Attestation: Intune uses Microsoft Graph to send the InitiateMobileDeviceManagementKeyRecovery command.
- Device Recovery and Attestation: The device performs recovery and attestation, ensuring the certificate is in the TPM.
- The Platform Restriction Filter: This would restrict access by preventing unattested devices from getting enrolled.
- Report Generation: Intune generates attestation reports, viewable by IT administrators.
Let’s see how creating a new platform enrollment restriction could secure enrollment even more.
Securing Windows Enrollment with IsTpmAttested
With the MDM Certificate hardened and attested, ensuring that only devices that successfully performed TPM attestation can enroll in Intune is essential. To achieve this, you can create a Windows device platform restriction policy within Intune to block non-attested devices from enrolling.
Creating the Restriction Policy
To enforce this policy, follow these steps:
- Create a New Filter:
(device.IsTpmAttested -eq “False”)
This filter checks whether the device has successfully performed TPM attestation.
Assign the Policy: Assign the new device restriction policy to all users and include the filter.
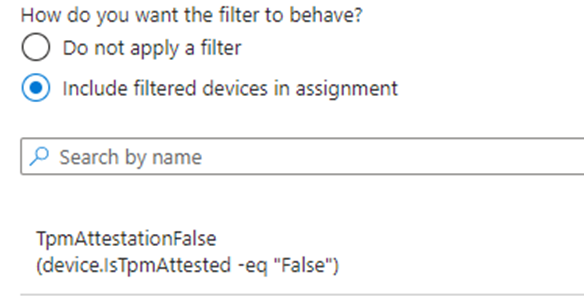
This filter checks whether the device has successfully performed TPM attestation.
Enforcing the Policy
With this filter in place, devices that did not successfully perform TPM attestation will be blocked from enrolling. When the device is blocked from enrollment, the error 80180032 will appear. This additional security measure ensures that only trusted devices are managed by Intune, which is especially important for organizations with a bring-your-own-device (BYOD) policy.
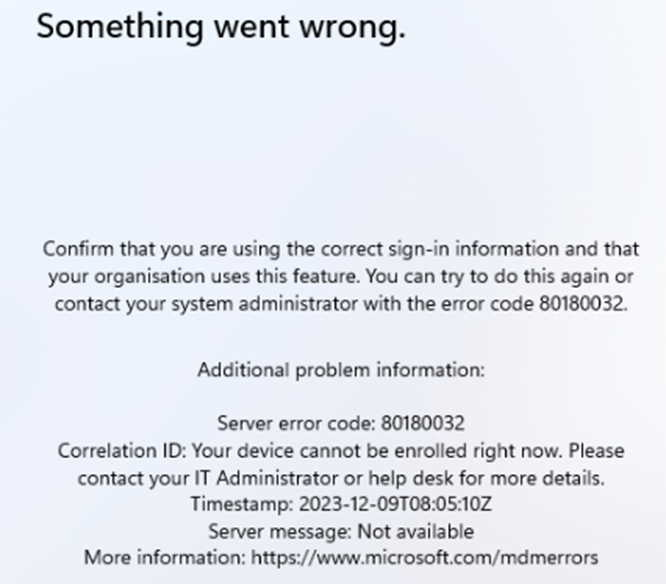
If an enrollment attempt fails due to this policy, the device will display an error message indicating that it cannot be enrolled. For instance, a virtual machine that cannot perform TPM attestation will show an error code 80180032, signaling that enrollment is blocked.
Benefits of this Policy for Security Measures
Implementing this device platform restriction policy enhances the security of your MDM environment by ensuring that only devices meeting strict security criteria are enrolled. It helps prevent potential security breaches caused by non-attested devices and restricts access to unnecessary features.
Conclusion
Windows Enrollment Attestation is a powerful mechanism for ensuring the integrity and security of devices within an organization. With Intune’s new attestation report feature, administrators now have a robust tool to verify device security and enforce compliance policies. By following the steps outlined in this blog, organizations can significantly enhance their device security posture, ensuring that only trusted and attested devices are allowed access to corporate resources.
Stay ahead in the security game by leveraging TPM attestation and Intune’s comprehensive reporting capabilities. These cutting-edge technologies will secure your digital environment and protect your organization from potential threats.
