Third-Party Patch Management for Microsoft Intune How-to Guide
Our most common question since releasing automated Win32 application creation for Microsoft Intune is, “How can I automate third-party patch management in Intune for devices managed by Intune standalone?” When managing devices using only Intune, it can be challenging to know how to update third-party products like Adobe Reader, Oracle Java, Google Chrome, 7-Zip, etc.
Today, we’re excited to announce the availability of third-party patching for Microsoft Intune and explain some of the challenges we had while developing our solution.
- The Challenges for Third-Party Patching in Microsoft Intune
- There is No WSUS in Windows Update for Business (WUfB)
- Evaluating the Options in Microsoft Intune for Third-Party Updates
- Creating Third-Party Patches Using Intune Win32 Applications
- How Third-Party Updates will Work within Patch My PC and Intune
- Power BI Reports for Microsoft Intune Third-Party Patching Compliance
Watch the Short Overview Video:
You can watch the short 7-minute video that reviews the new feature for third-party patching in Microsoft Intune.
The Challenges We Encountered Developing Third-Party Patch Management in Microsoft Intune
The biggest challenges we faced when coming up with an agentless way to patch third-party applications was the lack of inventory and update flexibility when comparing Microsoft Intune to Configuration Manager (SCCM). We had to rethink the traditional approach to how updates had always worked.
With our patch-management product for SCCM, we were able to use WSUS which has been evolving for over 20 years. WSUS allowed us to be intentional when creating detection rules and deployments of third-party updates.
Here’s an example of a third-party update and the flexibility we have in WSUS to create Update Applicability Rules.
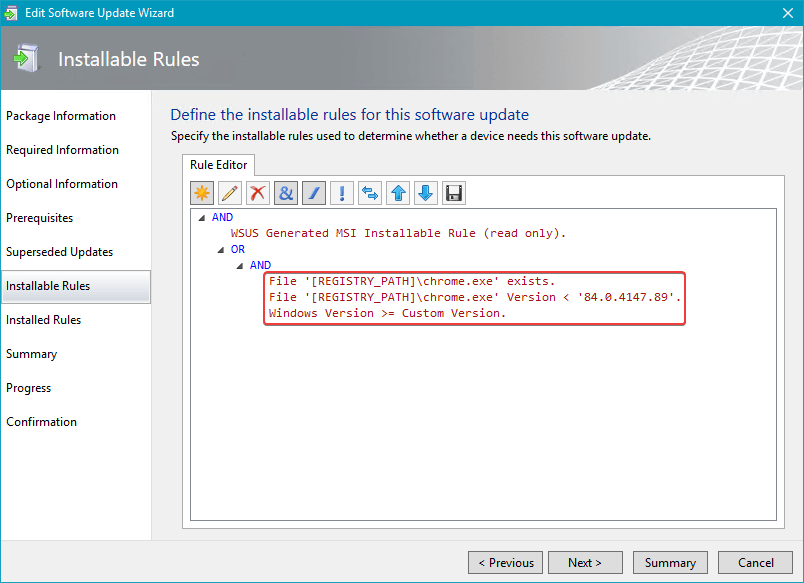
There is No WSUS in Windows Update for Business (WUfB)
Devices managed by standalone Intune will scan directly against WUfB. Since WUfB is not extensible like WSUS for publishing third-party updates, we were unable to use the existing catalog and publishing mechanisms we have been using for Microsoft SCCM and WSUS.
With WUfB, the options are designed to be simplified. Here’s an example of some of the options you receive with WUfB:
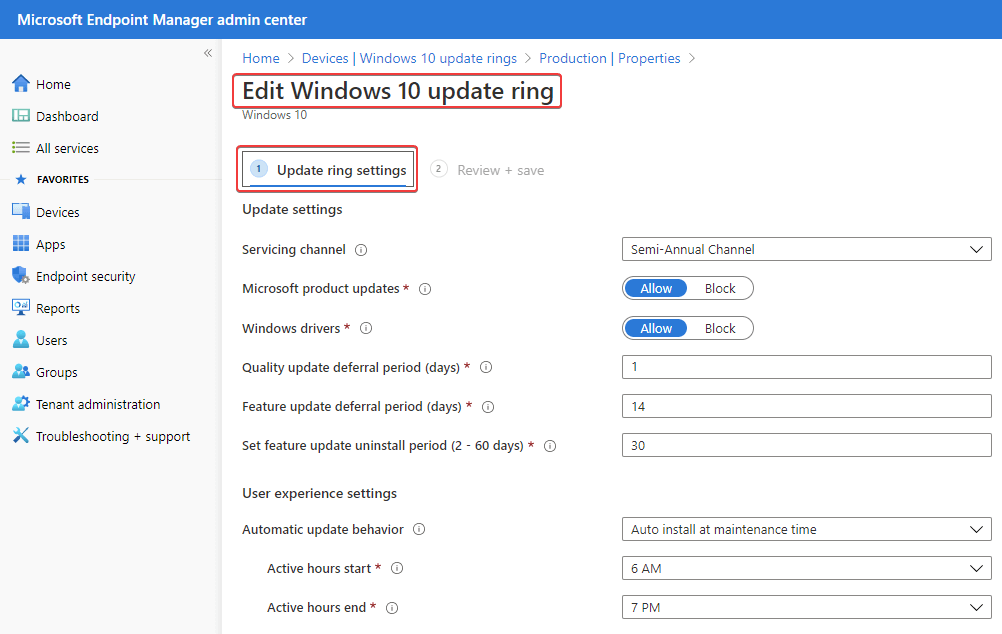
There isn’t an option for third-party patching or the ability for vendors like us to publish third-party updates to WUfB since it’s primarily Windows Update with additional criteria for targeting for businesses.
Evaluating the Options in Microsoft Intune for Third-Party Updates
Since our options for patching in Intune were pretty limited compared to WSUS/SCCM, we had to evaluate what options were currently available in Microsoft Intune. The good news is third-party patching is ultimately just updating binaries on a device using an installer file (MSI, EXE, or MSP).
At Microsoft Ignite 2018, Brad Anderson did announce a new feature in Microsoft Intune for Win32 application management. The Win32 application management feature added the ability to deploy EXE-based installers and gave more options for deployment MSI-based installers.
We have been using the Win32 application feature in Intune since February 2020, when we released our feature to automatically create applications for Microsoft Intune. This feature allows us to automatically create applications in Intune that you can deploy as required to users or make available in company portal.
While this was a great start, this only helped our customers to deploy third-party applications in Intune. Still, it didn’t address how to patch and report on existing third-party applications installs on managed devices.
Creating Third-Party Patches Using Intune Win32 Applications
We wanted to avoid installing any additional agents for third-party patching in Intune, so we had to develop a solution to make Win32 applications function more like a software update. The main challenge here was ensuring we have the ability only to install the Win32 application when there’s only an outdated version of the product already installed.
Intune already offered an option for application requirements that need to be met for an application to be considered applicable.
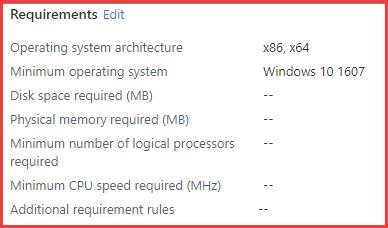
We were able to create a check within the requirement rules and make them function like installable rules in the traditional update model within WSUS.
How Third-Party Updates will Work within Patch My PC and Intune
The way we are implementing third-party patching in Microsoft Intune is to have two separate Win32 applications for each product. One of the Win32 applications will be designed for initial deployments. The update version of the Win32 application will be designed only to be required when an outdated version is detected.
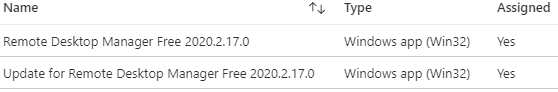
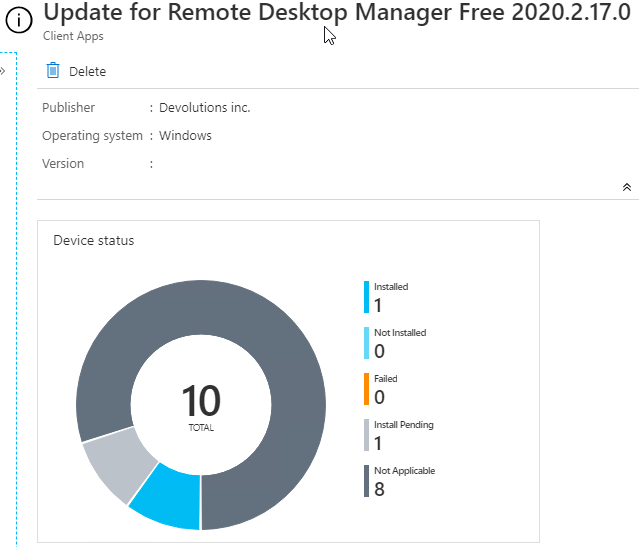
If you review the update version of the Win32 application, you will be able to see the compliance statistics. When an update is deployed as required, if there isn’t an older version installed, the Win32 application will show as Not Applicable.
In the device or user install status blade, you will see PowerShell script requirement rule is not met in the Status Details column.
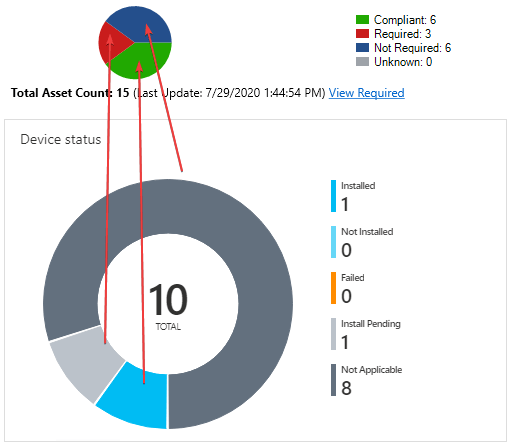
By configuring the Win32 applications with requirements, we were able to create a third-party software update experience very similar to SCCM. Here’s an example of how a Win32 application update will report compliance states and how it compares to software updates in SCCM.
Power BI Reports for Microsoft Intune Third-Party Patching Compliance
Our Power BI dashboards can be used to monitor the compliance and deployment of third-party updates and applications in Microsoft Intune.
Here’s an example of our the compliance dashboard looks.
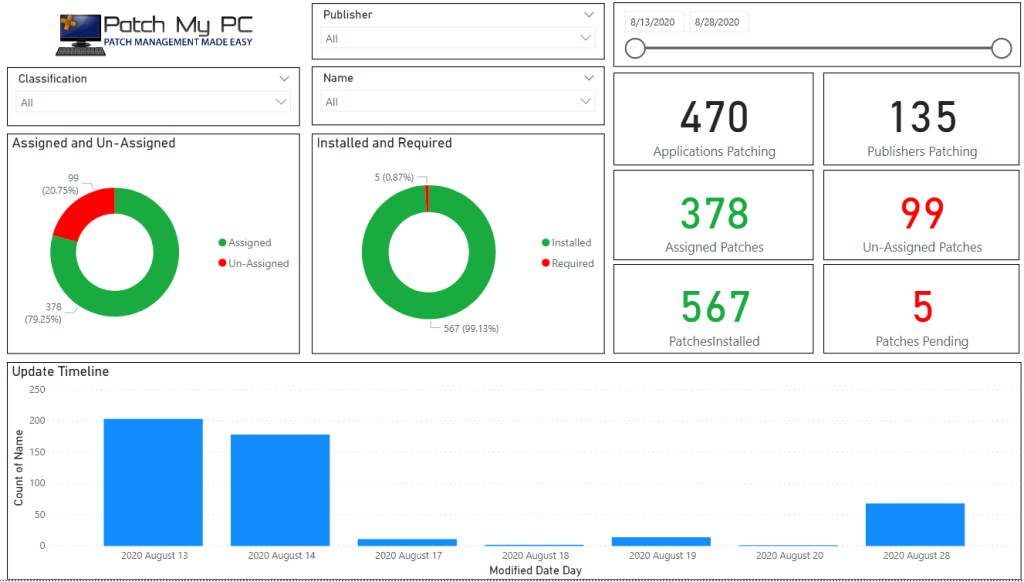
For setup instructions of the Power BI report, please see: Power BI Reports for Microsoft Intune Third-Party Update and Application Deployments
