Intune applications created by Patch My PC may give the error Failed to install in some scenarios if the code-signing certificate used to sign the PowerShell detection method script isn’t trusted on the client device.
Determine if You are Affected
If affected, you will see the error Failed to install in Company Portal if the application assignment is available. In some cases, the application may actually be installed successfully, as shown below.
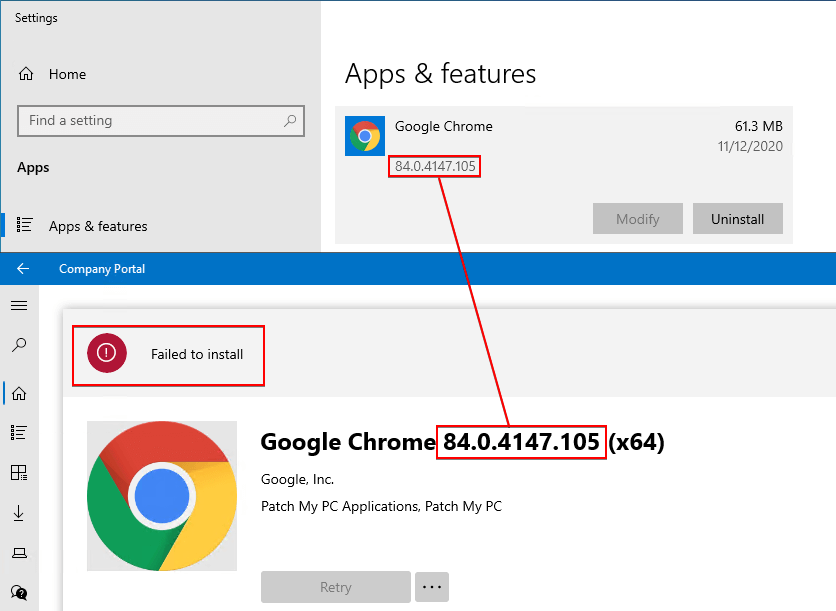
If you review the Intune Management Extention log file AgentExecutor.log, you will see errors similar to below:
Powershell script is failed to execute
write output done. output = , error = File C:\Program Files (x86)\Microsoft Intune Management ExtensionContentDetectionScripts.ps1 cannot be loaded. A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider. + CategoryInfo : SecurityError: (:) , ParentContainsErrorRecordException + FullyQualifiedErrorId : UnauthorizedAccess
This error results from having the option Digitally sign the detection method script and enforce signature checking on the application in Intune enabled and not deploying the certificate to the Trusted Root and Trusted Publishers certificate store on the client.
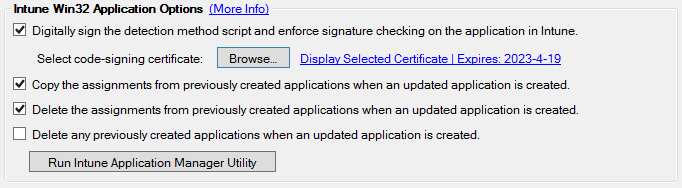
Resolution: Deploy the Code-Signing Certificate to Client Devices
You have two options to deploy the code signing certificate with Intune:
- Using a profile with custom settings in Intune and an OMA-URI to apply a setting from the RootCATrustedCertificates CSP.
- Using a PowerScript in Intune, which itself will be unsigned and contain the code signing certificate used to install it on target machines.
To read more about option 1, using a profile with custom settings in Intune, see this Microsoft TechCommunity article by Jason Sandys: Adding a Certificate to Trusted Publishers using Intune.
For options 2, using a PowerShell script deployed in Intune, contiune reading. Below is a step by step showing how an Intune Script can be created using the script attached here. Additionally, there are steps to help gather the required information.
Gathering Info
The script itself will need to be edited with your specific Thumbprint and Base64 encoded certificate string. The function contained within the script discusses how to gather these values, but I’ll also note them below. Also, if you are comfortable with Configuration Items within Configuration Manager, you can simply grab the script, adjust for your environment, and deploy away!
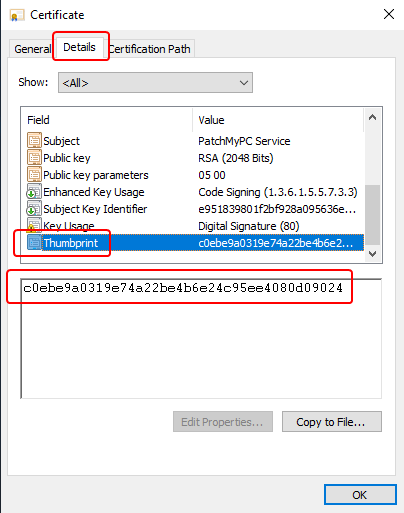
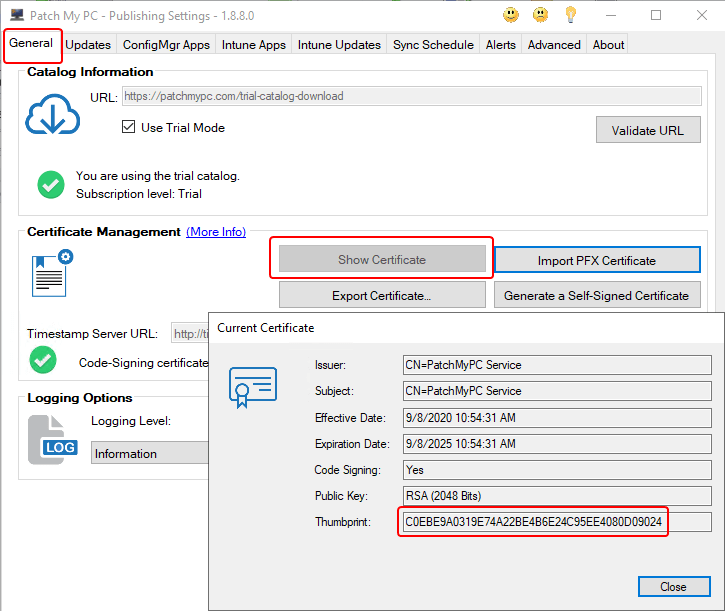
- Certificate Thumbprint:
- Base64 Encoded Certificate String: This can be acquired a handful of ways, but a simple way is to get a copy of the certificate as a file and run a PowerShell command similar to the below
- Set-Clipboard -Value (::ToBase64String((Get-Content -Path .ExportedCert.cer -Encoding Byte)))
Step 1: Create a New Script
Make a local copy of the script attached here and ensure you edit the script based on the information you gathered above. We will later upload this .ps1 file to Intune.
Navigate to Intune and locate the Scripts node under Devices.
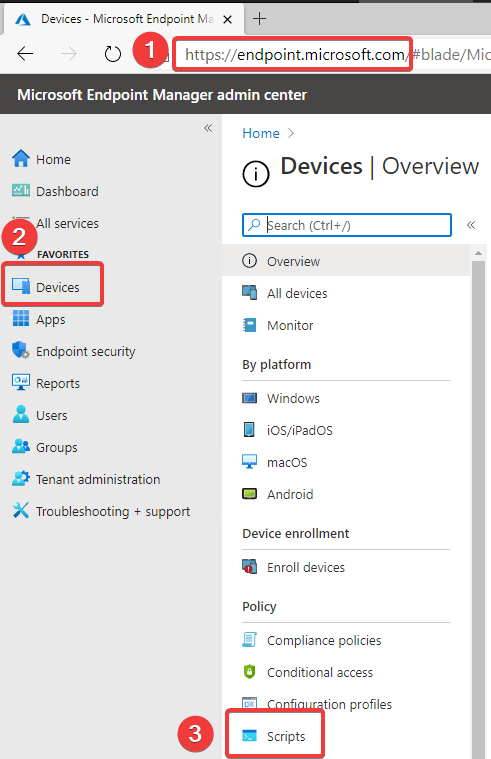
Within this node, you can create Add a new Windows 10 script.
Basic information can be input for the Name and Description.
We now will make sure our local copy of the script has been edited for our environment.
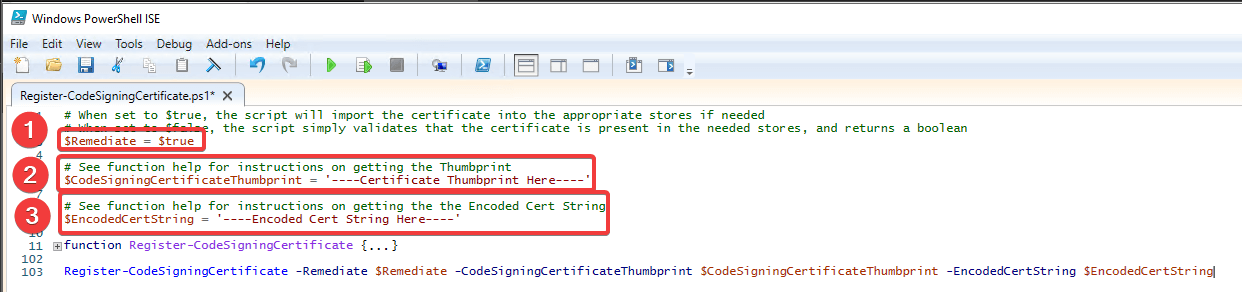
- Ensure $Remediate = $true
- Set $CodeSigningCertificateThumbprint to your thumbprint gathered earlier.
- Set $EncodedCertString to the Base64 string representation of your code signing certificate gathered earlier.
- Save the script!
With our script updated and saved we can:
- Upload it to Intune
- Ensure we set ‘Run script in 64 bit PowerShell Host’
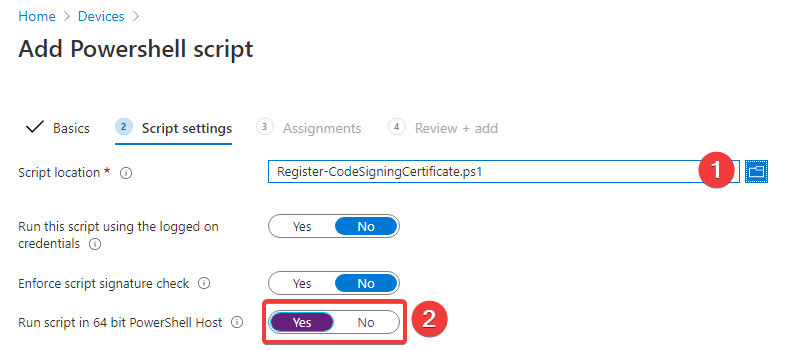
Note: It is important that you do not ‘Enforce script signature check’ on this script. We are deploying this script to ensure we can enforce signature checking on other scripts.
Step 2: Assign the Script
With all the above steps complete we can assign our script! The target of the assignment is up to you, but in our case, we will target all devices.