This blog focuses on the new Windows 11 25H2 feature “Remove Default Microsoft Store Packages.”
It’s a long-awaited setting that lets you remove a curated list of inbox Microsoft Store apps natively, no PowerShell scripts required. If you’ve wanted a cleaner Windows deployment, this new policy is worth a look.
Why We need the Remove Default Microsoft Store Packages policy
Since Windows 10, admins have asked for a supported method to remove built-in Microsoft Store apps. Sticky Notes, Solitaire, Quick Assist, Xbox, Clipchamp, most enterprises don’t want these showing up for users. The only real option until now was PowerShell. And that’s fragile. Remove the wrong app, and you can break OOBE, Autopilot, or even cause the Enrollment Status Page to hang.
What we needed was a native policy to handle app cleanup automatically during provisioning, no scripts, no timing issues. That’s exactly what Windows 11 25H2 delivers with the Remove Default Microsoft Store Packages feature.
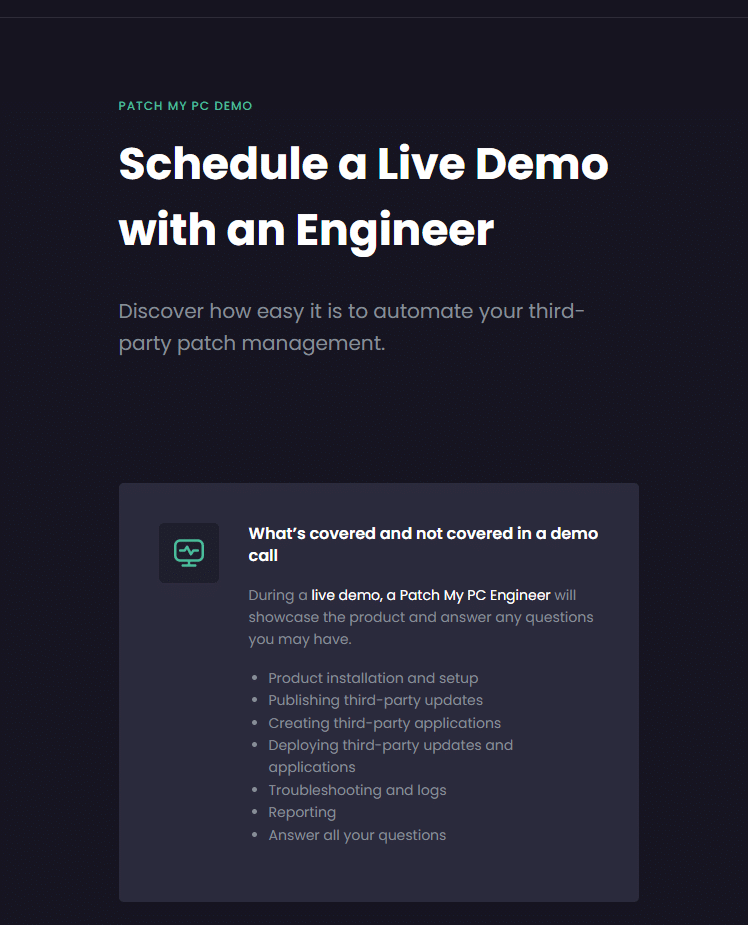
The New Policy: Remove Default Microsoft Store Packages
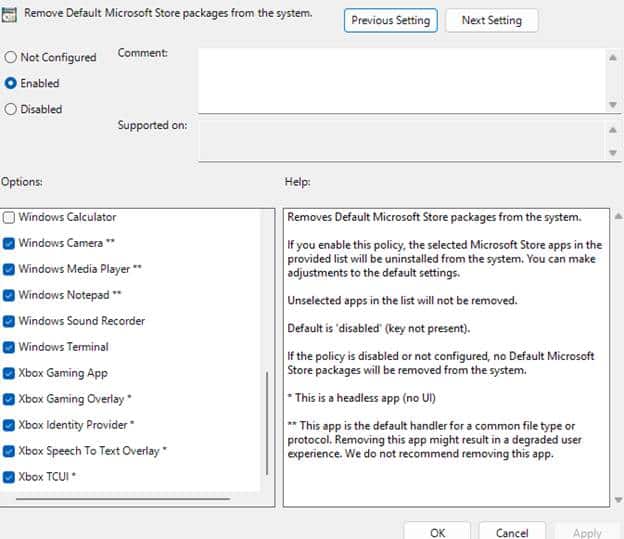
With one of the latest Windows 11 Insider Preview Dev builds (Windows 11 25h2), a new Group Policy setting showed up under: Computer Configuration > Administrative Templates > Windows Components > App Package Deployment
The setting is called Remove Default Microsoft Store packages from the system. It lets you pick from a curated list of built-in Microsoft Store apps that should be stripped out when a new user profile is created. No, you won’t find Candy Crush or Spotify in there; this is Microsoft’s own inbox app list. Here’s what the GPO looks like:
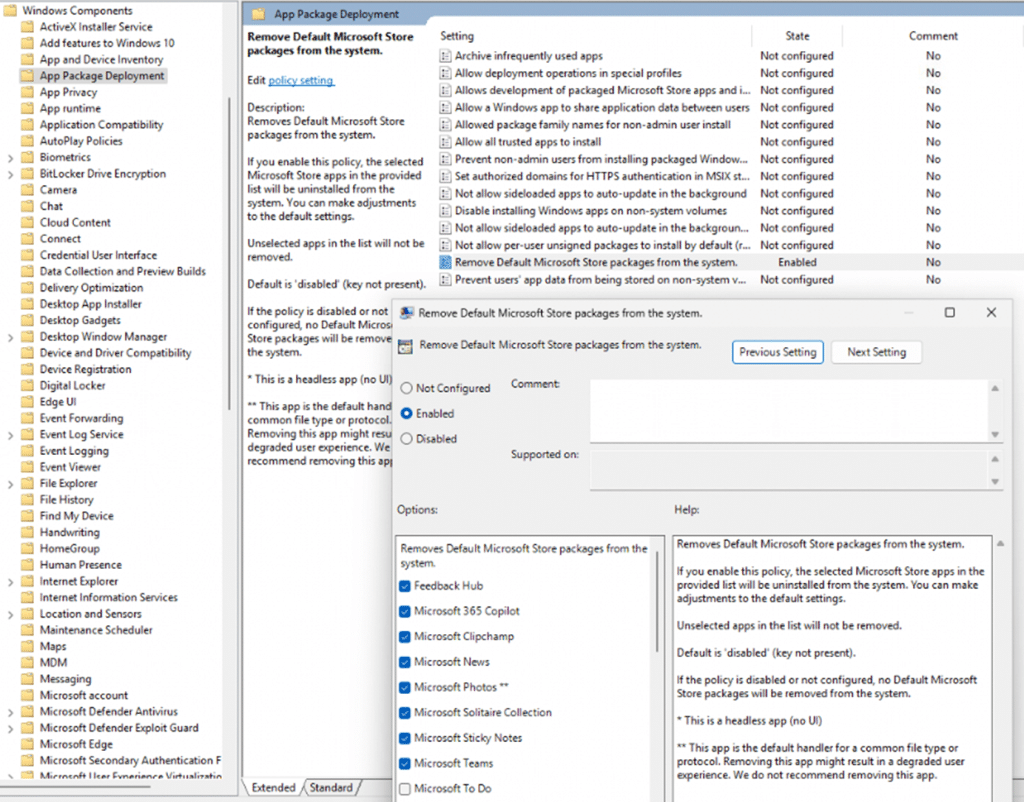
Besides having the good old legacy GPO option to configure this feature to remove default microsoft Store Packages, we can also configure a settings catalog to configure the same thing.
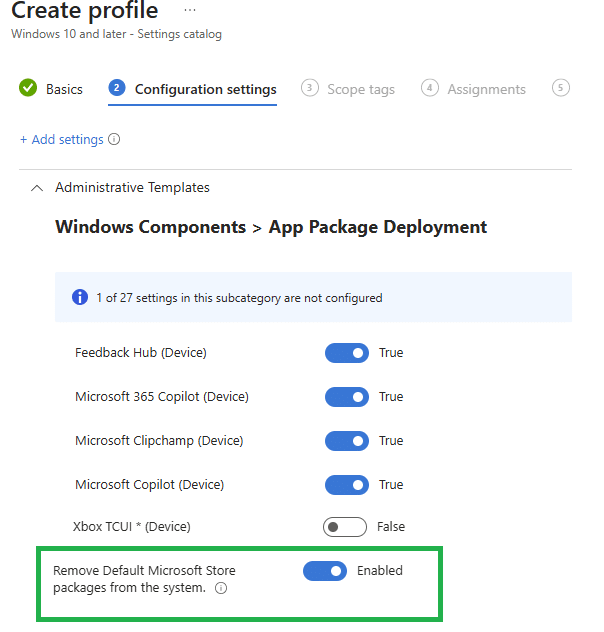
Once you enable the settings catalog policy and deployed it to your Windows 25H2 Devices, Windows creates this registry key: HKLM\SOFTWARE\Policies\Microsoft\Windows\Appx\RemoveDefaultMicrosoftStorePackages
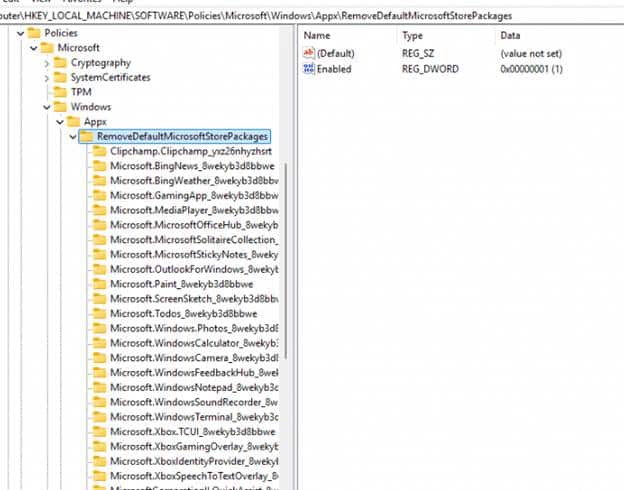
Each subkey corresponds to the selected app, using its package family name.
Windows 25H2 Enterprise / Education SKU
While looking at the code, this Store App feature is only going to be available for Enterprise and Education SKUs, which is a big shame, as I was also hoping that this feature would also be available for Windows Pro devices.
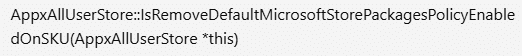
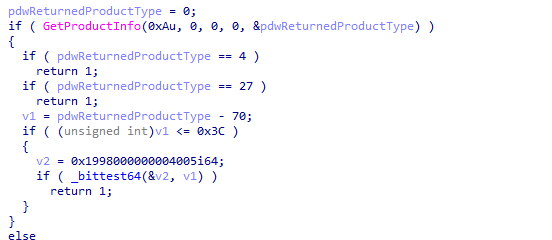
But…. looking further in the code, we noticed RemoveDefaultMicrosoftStorePackages_EnableOnAllOSVersions showing up
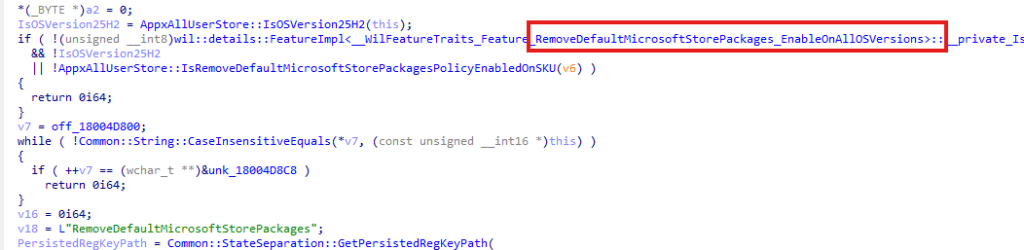
This code clearly tells me that this feature is going to be backported to earlier versions of Windows 11! Which is pretty great to notice
The Remove Default Microsoft Store Packages Technical Flow:
Here’s exactly what’s happening under the hood, straight from the code (yes, we decompiled appxalluserstore.dll in IDA. Check out our video on YouTube to find out more):
- The logic only runs if both Feature_RemoveDefaultMicrosoftStorePackages (57056100) and Feature_UxAccOptimization (48433719) are enabled. You can enable them using ViVeTool.
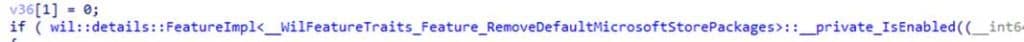
- The feature (GetRemoveDefaultMicrosoftStorePackagesPolicy) checks the HKLM\SOFTWARE\Policies\Microsoft\Windows\Appx\RemoveDefaultMicrosoftStorePackages policy to determine if the policy is enabled.
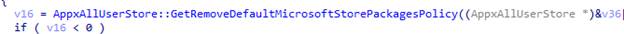
- When a new user profile is created or if the user logs off and on again (as opposed to an existing one), the removal logic is triggered.
- The main function (AddAllUserApplicationsToDynamicArrayForUser) starts enumerating the apps that need to be removed for that user.
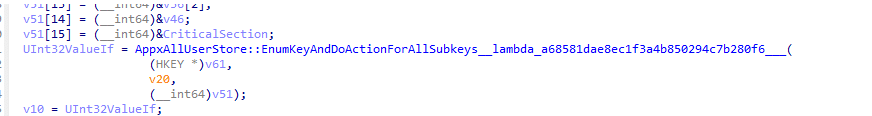
- For each app, the code walks through the subkeys in RemoveDefaultMicrosoftStorePackages.
- If the app matches a subkey and the policy is enabled, it’s flagged for removal.
- The CleanupPackageFromPerMachineStore function is called:
- Copies the registry data for the app to a “deleted” subtree
- Deletes the provisioning info for that app from the machine
- Moves the app’s files to a DeletedAllUserPackages folder
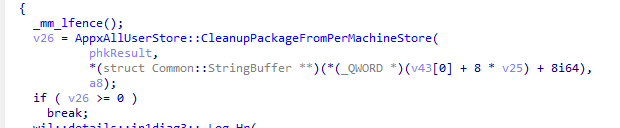
- If successful, the app is unprovisioned and shouldn’t appear for new users logging in.
- The logic writes telemetry to the Microsoft Windows AppXDeploymentServer Operational event log. If the policy or removal fails, you’ll see detailed errors there.
If you want to follow the process yourself, this all happens in appxalluserstore.dll and is orchestrated (and logged) by the AppXDeploymentServer provider. You can watch events in the Microsoft Windows AppXDeploymentServer Operational log.
Results: Remove Default Microsoft Store Packages
To test this new Remove Default Microsoft Store Packages policy, I set both feature flags with ViVeTool and enabled the policy before Autopilot enrollment.
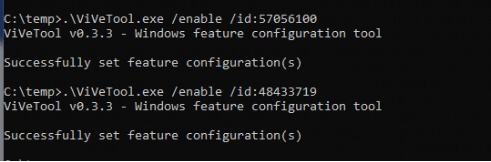
Please note: When using Windows 25h2, this step is not needed!
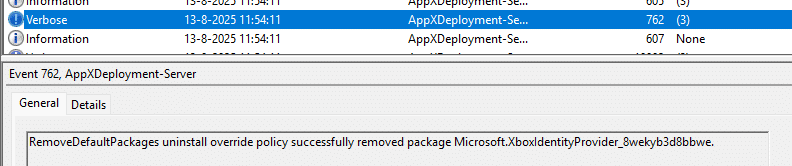
Sure enough, as soon as the device completed provisioning and the user logged in, the removal ran. You’ll see an event 762 like this in the AppxDeployment Server log, mentioning that the RemoveDefaultPackages uninstall override policy successfully removed the package.
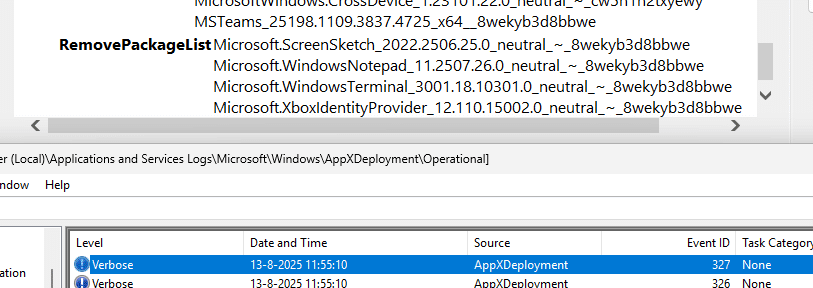
And of course, you can spot a good summary of which apps have been removed in the AppxDeployment Eventlog (event 327). As shown below, you get a perfect, machine-readable record of which apps were targeted for removal.
How the Microsoft Store App Removal really works
If you want to go deeper into what actually happens when Windows removes these apps, how the provisioning data is deleted, how per-machine packages are moved to the DeletedAllUserPackages folder, and how AppXDeploymentServer orchestrates the cleanup, check out my follow-up blog. It walks through the internal functions and registry transitions that make the policy work behind the scenes.
Go Beyond the UI and Remove Any App with PowerShell
Right now, the only official option is through Group Policy or a Settings Catalog Policy (or a CSP). But you are not limited to just what the GPO shows. As we noticed in the technical flow, Windows only looks for registry subkeys in
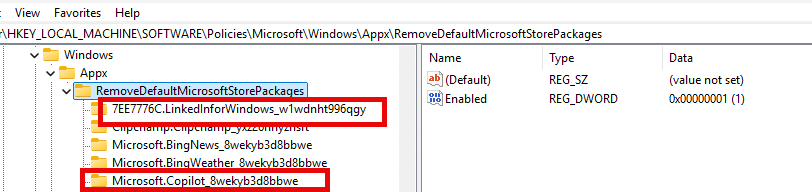
HKLM\SOFTWARE\Policies\Microsoft\Windows\Appx\RemoveDefaultMicrosoftStorePackages. If you add a package family name there, even if it is not in the official Group Policy list, Windows will remove that app for every new user profile.
Why? Because the code to remove the apps just puts all the packages in one big array!.
This gives you much more control. For example, if you want LinkedIn or Copilot removed, just add their package family names to the registry.
The removal process will catch anything you list, not just what shows up in the Settings Catalog or the GPO. So, you are also not tied to Group Policy or a CSP. Since this feature is all registry-driven, you can set it with a simple PowerShell script
Here is what the Script will do.
- Create a subkey for each package family name you want removed
- Set a value called
RemovedPackageto 1 in each subkey - Set
Enabledto 1 at the base key
Example: To remove LinkedIn and Copilot, add these:
"7EE7776C.LinkedInforWindows_w1wdnht996qgy", # LinkedIn
"Microsoft.Copilot_8wekyb3d8bbwe" # Copilot
Add the PowerShell to Intune and assign it to all devices to ensure the script runs before the first user signs in, so the app removal occurs at the correct moment.
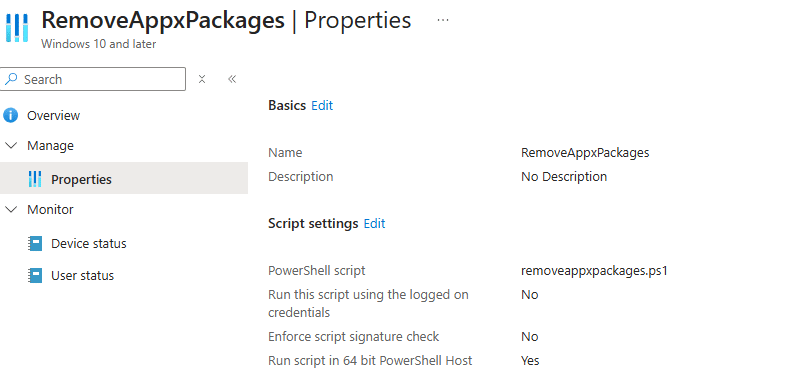
The moment the PowerShell script is executed, the LinkedIn and Copilot apps will be removed and will no longer be able to run.
This approach offers more flexibility than the UI, and you can fully automate it today using PowerShell… which is also the biggest disadvantage 🙂
Final note
If you want to get rid of the Microsoft Store apps (AKA bloatware?), once and for all, this is the most reliable option we have. No PowerShell scripts, no weird Dunning Kruger cleanup script… just a built-in policy that will ensure that all selected Microsoft Store App Packages will be removed for all users!
Check out our YouTube video as well, explaining this Store App removal feature!
Patch My PC doesn’t handle that built-in app removal, we focus on managing, deploying, and updating third-party applications. Want to see how we simplify your non-Microsoft app lifecycle? Book a demo.