
This blog zooms in on the new Windows Quality Update Management Policies showing up on the public Intune roadmap and being partially referenced at Ignite.
Please note: This blog is based on OSINT. So hi! 🙂
Introduction
It all started with a small note on the Microsoft 365/ Intune roadmap.
“Windows Quality Update management policies.”

At first glance, it looked like another incremental addition. One line changed that.
“Manage individual Windows quality updates, including non security, out of band updates.”
That was enough reason to dig deeper and open the Dev Tools.
Finding the Windows Quality Update management policies Wizard
After checking the Intune portal JS code, a new view suddenly appeared. This view got the name: Add Quality Update Policy Wizard. That name alone was interesting, and it made me wonder if it was the one I was looking for. Opening the view revealed a nice new policy wizard that defined five distinct quality update types.

- Monthly b-week security updates
- Monthly non-security preview updates
- Out-of-band security updates
- Out-of-band non-security updates
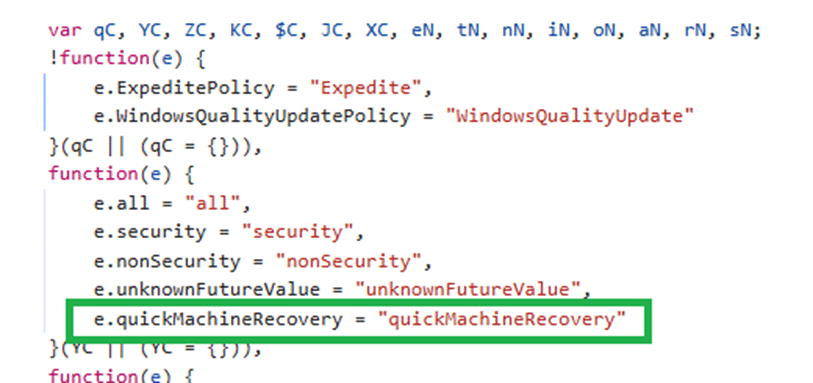
- Quick Machine Recovery updates
Each entry had its own cadence, category, and approval type.
Security and nonsecurity updates were set to automatic approval.
Quick Machine Recovery stood out immediately, with manual approval only.
The policy definition even included a toggle called hotpatch Enabled, confirming that these updates can apply without a restart.
Quick Machine Recovery in the Windows Quality Update management policies
Quick Machine Recovery isn’t new for those who follow the Windows recovery work we’ve been exploring at Patch My PC. In our earlier article, we looked at how Quick Machine Recovery connects to Windows remediation logic and the new recovery framework. What’s new now is how that concept appears in Intune as part of Quality Update management.
By adding it to the same wizard that manages both security and non-security updates, Microsoft is clearly moving toward a unified approval and update release system.
The manual approval flow aligns with the arrival of QMR updates, which are fast, isolated, and controlled by the admin. When the time comes to push an urgent fix or recover machines remotely, this approval method will fit right in with the Quick Machine Recovery process we analyzed before.
Quick Machine Recovery Update Reporting
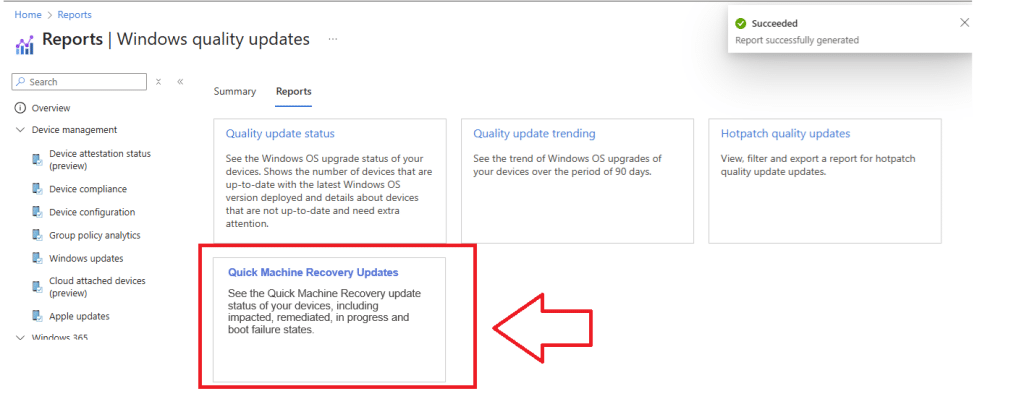
And if we are defining a full set of Quality Update policies that include Quick Machine Recovery, you would expect reporting to follow. It is not exposed in the portal yet, but the Intune JS code already contains a complete Quick machine recovery updates report. (which Microsoft also has shown at Ignite 2025)

The structure is already there: the Quick machine recovery updates blade, the counters, the grid, the routing, and all resource strings. It tracks the same signals defined in the QMR policy model: impacted devices, remediated devices, active recoveries, boot-failure state, QMR status, target QMR version, release dates, and the assigned quality update policy.
None of it is linked into the left navigation yet, but the backend hooks line up with the new Windows Quality Update Management Policies. QMR is not just a policy toggle. It is treated as its own update category with dedicated telemetry waiting to surface in Intune.
Until it does, here is a mockup showing how it will likely appear alongside the existing Quality Update reports.
The Recovery Side of Quick Machine Recovery
Quick Machine Recovery shows up here as its own update category with approvals and reporting, but that only covers the update and reporting side of the story. The real recovery and remediation logic lives somewhere else. If you want to see how WinRE readiness, recovery device status and remediation outcomes are handled, the Windows Recovery and Remediation feature picks up that part. That blog walks through the blade that exposes the recovery signals behind QMR and how Microsoft is shaping the missing management layer.

That leaves one more interesting category in the wizard: out of band updates and hotpatching. So let’s zoom in to that one as well
Out-of-band Updates and Hotpatching
The wizard doesn’t stop at regular or Quick Machine Recovery updates. Out-of-band updates have their own cadence listed beside monthly.

That means admins can manage nonscheduled patches directly from Intune, not just through Update rings. Combined with the hotpatch option, this suggests that Microsoft’s goal is to reduce reboots, even for emergency updates?
Out-of-band updates for both security and non-security purposes default to automatic approval, while QMR maintains manual review. Everything is handled in a single, central policy that defines the cadence, approval type, and delivery method.
Windows Quality Update management policies Approval Flow
The configuration includes a Quality Update Policy Approval Manager, which is where approvals and review actions will be handled.

This aligns with the new approach we’ve seen across other update blades.
Feature, driver, and quality updates all share the same backend now, and the same approval logic will eventually apply to each category.
Once the preview goes live, that flyout will likely become the admin’s main entry point for reviewing pending QMR or out-of-band updates.
From Roadmap to Reality
It’s rare to see a roadmap entry materialize so quickly inside the Intune portal.
Seeing it appear confirms that Microsoft’s plan for granular, real-time update control is almost ready for public preview.
The combination of Quick Machine Recovery, out-of-band cadence, and hotpatch delivery turns update management into something far more flexible than the old rings and pause timers ever were.
What started as curiosity from a single roadmap line ended with a working feature tucked into the next Intune build.
It’s another small but clear sign that Windows servicing is moving toward faster recovery, smarter patching, and full admin control, all within Intune.
