
Microsoft recently announced the Local Administrator Protection feature, a powerful tool for securing local admin accounts by isolating privileges and preventing token theft. However, when paired with Endpoint Privilege Management (EPM), things can get complicated. Local Administrator Protection focuses on locking down the admin account itself, while EPM is all about giving standard users temporary elevation for specific tasks. These overlapping functionalities can cause unexpected errors, making “Local Administrator Protection vs. Endpoint Privilege Management (EPM)” a real headache for IT admins. If you have both features enabled, you’re likely to run into issues that require more than a quick reboot to fix. Spoiler alert: this isn’t the only challenge with Local Administrator Protection. Let’s break down why these two features don’t always get along and how to deal with the fallout.
Local Administrator Protection vs. EPM: What’s the Difference?
Understanding the distinction between these two features is crucial for managing admin rights effectively. Here’s a quick breakdown:
- Local Administrator Protection: This feature is designed to secure local admin accounts by isolating their privileges and preventing token theft or misuse. It essentially locks down the admin account itself, ensuring that even if the account is compromised, the impact is minimized. It focuses on protecting the identity and elevation process of the administrator account.
- Endpoint Privilege Management (EPM): On the other hand, EPM addresses a completely different need. It’s aimed at empowering standard users by enabling temporary privilege elevations for specific tasks, without granting full admin rights. EPM uses virtual accounts to provide these elevated permissions in a controlled and time-limited way, making it a great tool for organizations that need fine-grained control over admin privileges.
The key difference? Local Administrator Protection is about securing admin accounts and their elevation process, whereas EPM is focused on empowering standard users with temporary, task-specific admin privileges. They serve distinct purposes but can sometimes overlap, creating conflicts when both are enabled in the same environment.
The Problem: Virtual Accounts Clash
Both Local Administrator Protection and EPM rely on something called “virtual accounts“. When they’re both enabled, things can go sideways fast. Here’s what you might see:
- Error code: 0x80004005 (-2147467259)
- What it means: EPM tried to create a virtual account, but Local Administrator Protection blocked it by locking down the admin token.

For end users, it might look like this: “There was an error with running this app as administrator. Contact your support person. Error code: 0x80004003 (-2147467261)”
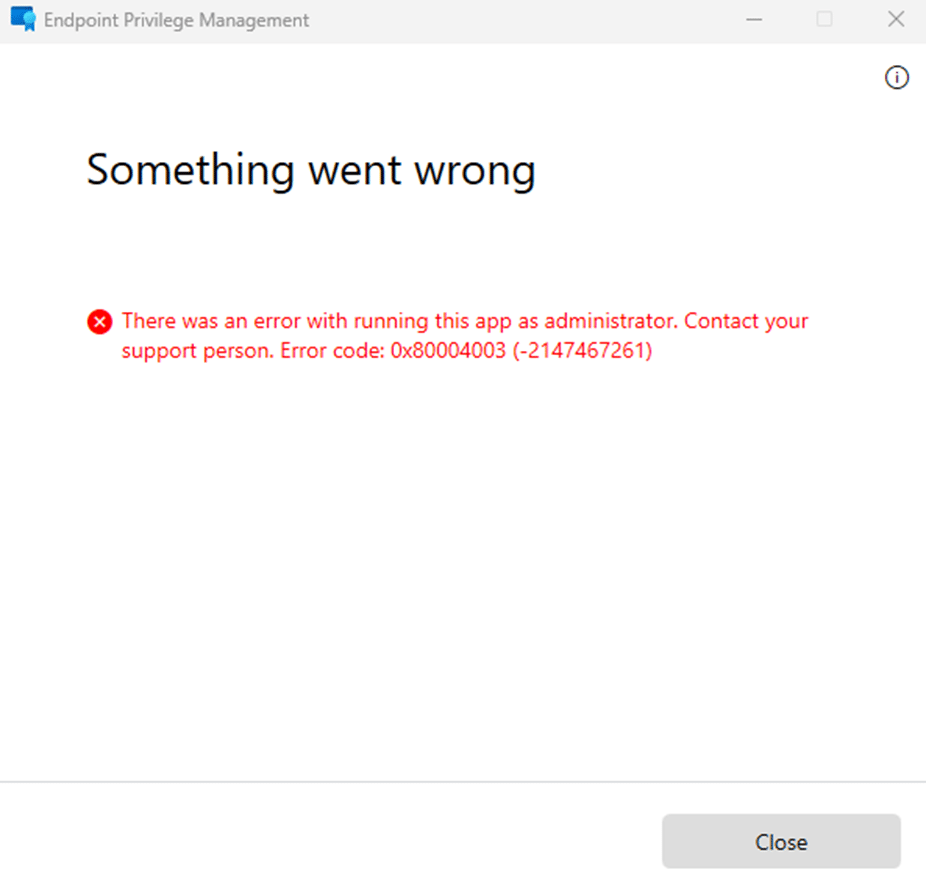
This isn’t just an annoyance; it’s a full-on blocker to EPM’s ability to handle privilege elevations.
Microsoft’s Take on the Issue
Luckily, Microsoft has confirmed the conflict between these features:

“Administrator Protection doesn’t currently support elevations initiated from Endpoint Privilege Management. If organizations enable Administrator Protection on devices where standard users rely on EPM to handle elevation, the elevation will fail.” (source)
They’ve acknowledged the issue and promised a fix in a future release. However, no timeline has been provided yet, so we’re left to deal with it for now.
What Can You Do About It?
Until the official fix from Microsoft arrives, not much…but here’s how you can manage the situation:
Choose Your Priority: Decide which feature is more critical. If EPM is essential for privilege elevations, consider holding off on enabling Local Administrator Protection. If securing local admin accounts is more important, focus on that for now.
Test Before Deploying: Always test these features in your environment before rolling them out broadly. Some setups might behave differently, but it’s better to catch issues in testing than in production.
Stay Updated: Keep an eye on Microsoft’s documentation and release notes. They’re aware of the issue, so a fix should be coming soon.
Wrapping It Up
Local Administrator Protection and EPM are both excellent tools, but right now, they don’t work well together. If you’re dealing with this issue, you’ll need to decide which feature to prioritize until Microsoft releases a fix.
And remember, this isn’t the only potential problem with Local Administrator Protection. I’ve noticed another issue that could cause headaches, especially in environments relying on specific languages. Stay tuned for a follow-up blog where I’ll dive into what’s going on there.
