Introduction to Intune Custom Compliance Policy
Businesses constantly experiment with new technology and third-party apps to complete tasks swiftly in our fast-paced digital age. The catch is that it’s crucial to make sure these managed devices and apps abide by the guidelines. You must ensure that everything, from your user and device groups to your organizational data, is secure and that you are following the rules.
For our benefit, Microsoft Intune has a clever trick up its sleeve called Intune Custom Compliance Policies. In this blog post, we’ll demonstrate how to use this device and Intune compliance policies to determine whether your third-party apps are abiding by the guidelines. We will make sure your environment and devices are compliant, and we will monitor the Intune compliance policy settings and status. We will be using PowerShell Discovery scripts and JSON files to complete these tasks, but it won’t be as difficult as it sounds, so don’t worry!
Understanding the Importance of Third-Party App Compliance
Let’s imagine that third-party applications are guests at a party you’re throwing. While they can add interesting and distinctive flavors to your event, there is always the worry that someone will slip and spill a drink or perhaps ruin something valuable. These “accidents” can translate to security flaws or data breaches in the digital realm.
Here’s why third-party app compliance matters:
Security Risks: In the same way that you wouldn’t want an accident-prone visitor at your party, your company doesn’t want to introduce apps into your environment that are frequently or easily exposed to online attacks. Applications that are not compliant put your sensitive company data at risk by providing access to malware and hackers. With that access, they can easily manipulate the data and cause changes to the compliance status of the devices in your environment.
Data Protection: Consider your company’s data to be precious possessions in your home. Compliance regulations help you protect organizational data and guarantee that these precious possessions remain safe. They provide guidelines and create rules that apps must adhere to while handling your organization’s resources and data safely.
Smooth Operation: Think about when someone plays loud music at a party. It’s hard to talk and have fun, right? Noncompliant apps can be like that noisy guest and can disrupt how your organization works. Compliance policies act like the host of the party, making sure everyone behaves nicely and everything goes smoothly.
Setting Up Custom Device Compliance Policies in Intune and the Prerequisites
Before you can begin, these are the prerequisites:
- Access to the Microsoft Intune portal
- Administrative credentials for Intune
- A PowerShell script that can detect the presence or version of third-party apps
- Basic knowledge of the JSON format for defining detection rules
Creating the PowerShell Discovery Script
- To create a compliance policy, we must first develop a PowerShell script that checks for the presence and version of the third-party app you want to monitor. This script should return a specific result when the app meets the compliance criteria. Once that is created, we can then ensure the script is properly tested and functional.
Example: In the script below, we are using Google Chrome as an example. The script will check for the presence of the app with the version under the registry hive:
- For 64-bit: HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
- For 32 bits: HKLM:\SOFTWARE\WOW6432NODE\Microsoft\Windows\CurrentVersion\Uninstall
The script will then check the DisplayName and DisplayVersion attributes. If the app is installed, it will show the name and the version. If it is not installed, it will show as “0.0.0.0”.
Note: Make sure to enter the exact display name shown in Add and Remove Programs. While you can use wildcards to search for software, the exact display name discovered in appwiz.cpl will be used as the setting name for the JSON compliance check rule.
- We will be adding a loop to convert the $appInfo array into a single custom object named $objectJSONoutput. This is because we want a single object with all the apps and versions listed as key-value pairs in the JSON output instead of an array with separate objects for each app.
- In the end, we will compress the return output to a JSON file.
Creating the JSON Detection Rule File
Now, let’s configure a JSON detection file that serves as a guide. This guide will describe the specific settings and values you want to use for device compliance with your custom compliance criteria. The JSON outlines what the discovery script will evaluate or check for on the devices.
You’ll need to upload the JSON file when you create a device compliance policy that includes custom compliance settings. Make sure that the JSON file has these parameters added to it and that the file is no larger than 1 megabyte (MB).
- SettingName: The name of the custom setting to use for base compliance. This name is case-sensitive.
- DataType: The type of data that you can use to build your compliance rule. For options, see the following list of supported data types:
- Boolean
- Int64
- Double
- String
- DateTime
- Version
- MoreInfoURL: This is a URL that’s shown to users with noncompliant devices so they can learn more about the compliance requirement they are missing. This links to instructions that will help users bring their devices into compliance.
- Operand: This represents the values that the operator works on.
- Operator: This represents a specific action that is used to build a compliance rule. For options, see the following list of supported operators:
- IsEquals
- NotEquals
- GreaterThan
- GreaterEquals
- LessThan
- LessEquals
- RemediationStrings: This is information that gets displayed in the Company Portal when a device is noncompliant in some way. It is intended to help users understand the remediation options to bring a device to a compliant state. There must be at least one string for the language you want to use (e.g., “en_US”), but you can also specify additional remediation string languages, such as:
- cs_CZ
- da_DK
- de_DE
- el_GR
- en_US
- es_ES
- fi_FI
- fr_FR
- hu_HU
- it_IT
- ja_JP
- ko_KR
- nb_NO
- nl_NL
- pl_PL
- pt_BR
- ro_RO
- ru_RU
- sv_SE
- tr_TR
- zh_CN
- zh_TW
For more information, see Available languages for Windows.
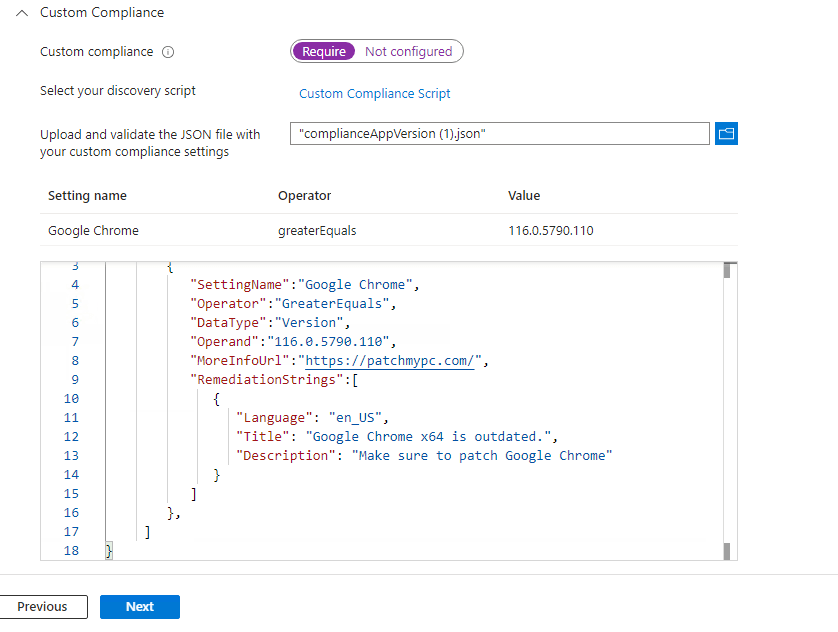
Example: In the JSON file below, we are describing the specific settings and values we’ve laid out. The file outlines what the discovery script will evaluate or check for on the devices. In this scenario, it will check if Google Chrome has a version greater than or equal to 116.0.5790.110. If the version is old, mark it as having a “noncompliant” status in the Intune Portal. If it is up to date, then mark it as “compliant“.
Assigning the Custom Device Compliance Policy
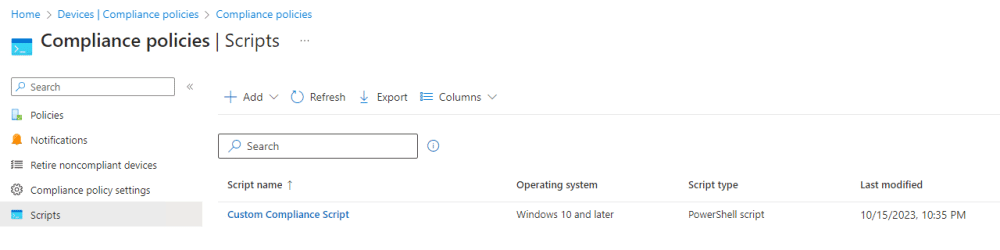
Before creating the actual compliance policy, please make sure to upload the script under “Scripts” in the Compliance policies section.
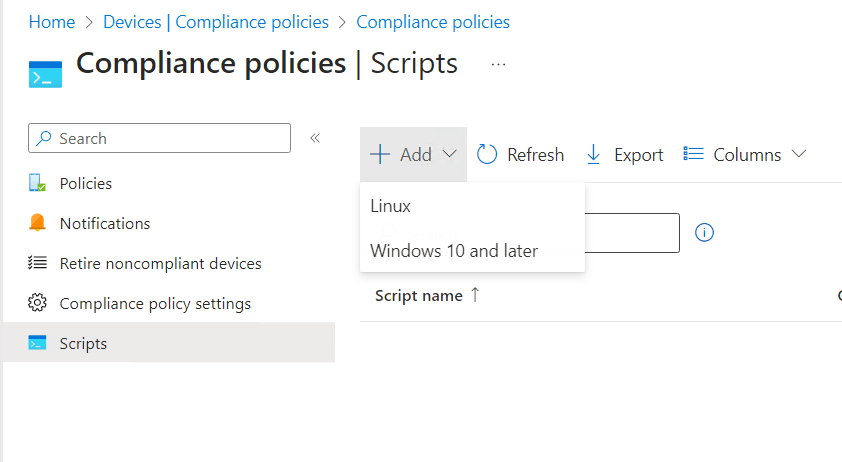
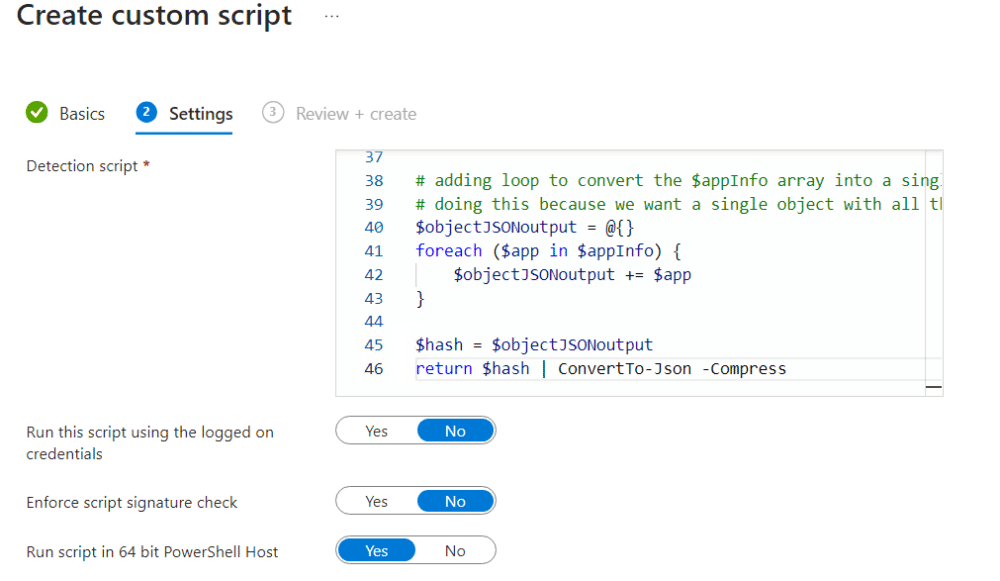
- In the Basic tab, add a name and description for the script.
- In the Settings tab, copy and paste your detection script. Keep all the other options as default. Click Next.
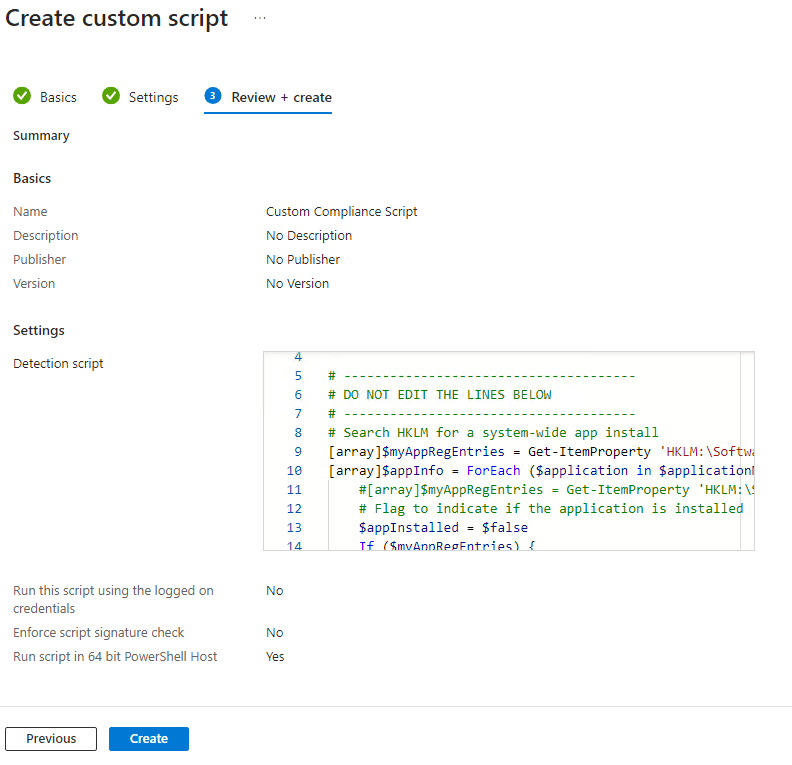
- In the Review + Create tab, verify the settings and click on Create.
- You will get a notification once the script is created.
Steps to create a custom compliance policy for third-party applications in Intune
- Sign into the Microsoft Intune admin center.
- Click on Devices > Compliance Policies > Create Policy.
- Select “Windows 10 and later” as the platform for the policy.
- In the Basics tab, enter a name for the compliance policy settings and select the Custom Compliance setting.
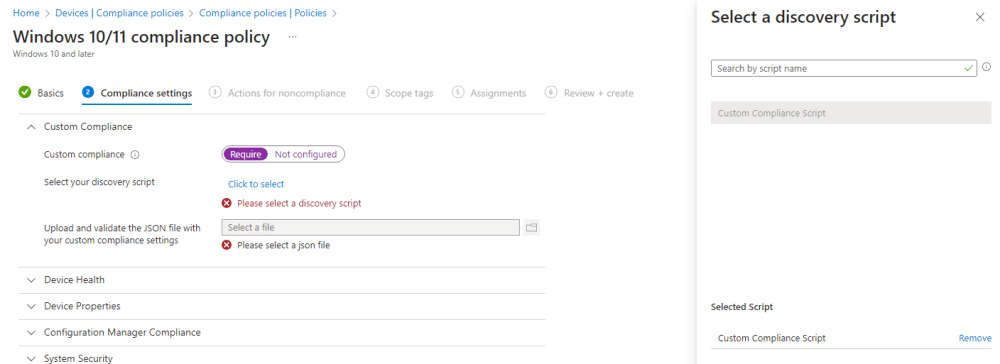
- On the Compliance Settings tab, expand the Custom Compliance section.
- Select “Require” on Custom Compliance.
- Click on Select your discovery script and select the script that you created earlier as part of the prerequisites for this process.
- Click on Upload, validate the JSON file with your custom compliance settings, and upload the JSON file that contains the compliance settings for third-party applications.
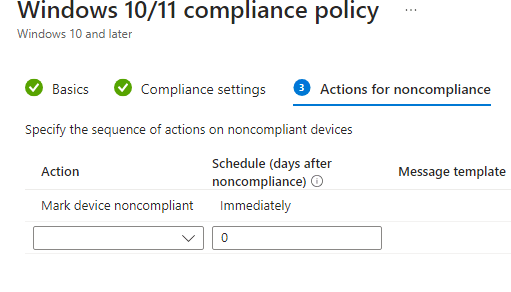
- On the Actions for noncompliance tab, specify which actions that you want noncompliant devices to take.
- In the Assignment tab, select the group you want to deploy the app to.
- Click on Review + Create to review the policy, then click on Create to create the policy.
Monitoring and Reporting
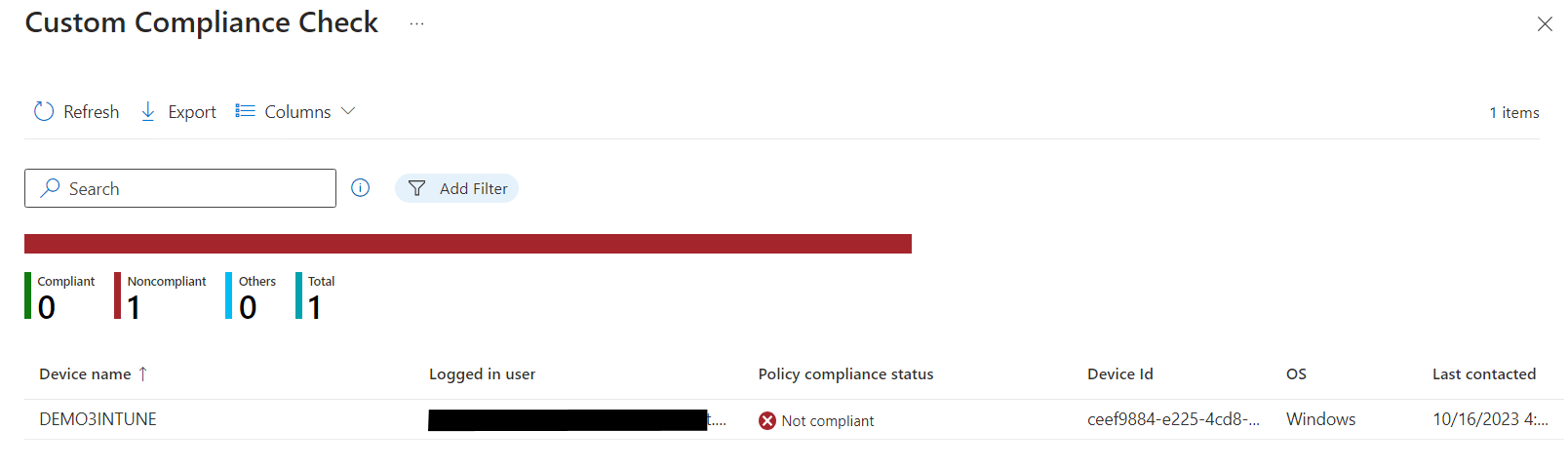
On the Policy overview page, you can see a summary of the policy’s settings and assignments. You can check the device’s actual compliance status value and see whether the device is considered compliant or noncompliant.
To monitor device compliance status, look for the “Device Compliance” section in Intune. Here, you’ll find information about devices that are considered compliant and noncompliant with the policy. Make sure to check for all of the available compliance settings.
View Compliance Reports
Click on “Device Compliance” to access more detailed device compliance policies and reports.
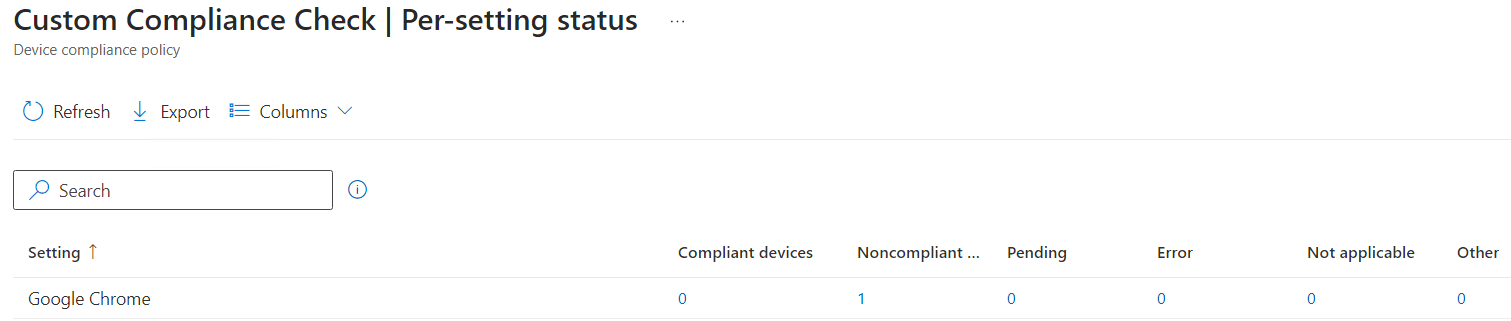
You can filter and sort these reports based on various criteria, such as status only, device type, user, and more. The reports provide a comprehensive view of device compliance within your organization.
Inspect Non-Compliant Devices
To investigate noncompliant devices, click on the “Noncompliant” section of the device compliance dashboard report.
You can view detailed information about each noncompliant device. In here, you can also take action to remediate and block access for noncompliant devices, such as sending notifications to users or implementing a conditional access policy to restrict access for noncompliant devices.
Conclusion
By keeping a close eye on the compliance status of your devices in Microsoft Intune, you’re essentially staying ahead of the game. It allows you to jump on any noncompliance issues before they become big problems. Along with that, you also get to make sure that your organization’s devices are playing by the rules in terms of security and how they operate. In other words, it’s like having a watchful guardian to make sure your devices stay safe and follow the right path. This ongoing process of checking and reporting is the heartbeat of your device management and security efforts—it’s pretty much essential.
It is also important to make sure that the third-party apps that you are using in your environment are up to date. By integrating third-party patch management for Microsoft platforms, Patch My PC improves IT security and guards against infrastructure vulnerabilities. With Patch My PC, you can avoid cybersecurity attacks and ensure that your devices and environment remain compliant.
Reference Articles:
Third-Party Patch Management for ConfigMgr and Intune – Patch My PC
Use custom compliance settings for Linux and Windows devices in Microsoft Intune | Microsoft Learn
Create a JSON file for custom compliance settings in Microsoft Intune | Microsoft Learn
Create a discovery script for custom compliance policy in Microsoft Intune | Microsoft Learn