This blog examines a login issue that may arise after the Windows 11 24H2 upgrade is complete and the device reboots. After the device reboots, the user signs in with Windows Hello using his existing PIN, and everything appears normal. Until it breaks and the login screen shows you that something went wrong, and your PIN isn’t available
Introduction
Sooner or later, most organizations will move to Windows 11 24H2, either through a structured rollout using Intune’s feature update settings or by manually applying the upgrade.
If you’ve read the Patch My PC blog on troubleshooting feature update failures, that blog post focused on getting the upgrade to install. It covered how we could perform some troubleshooting on the device, but also using Graph, to find out why the feature update was not getting deployed. In this blog, we will zoom in on what happened after the device was successfully upgraded to Windows 11 24H2.
Windows Hello Works Fine… Wait… Your PIN isn’t available
A few hours after the upgrade to Windows 24h2, support tickets start rolling in. Users who signed in earlier that day with their PIN now find themselves stuck. Their PIN no longer works…. After they tried to sign back in again, the Windows Sign-in screen mentioned that: “Something went wrong and your PIN isn’t available and the error code: 0xc000006d.

Luckily, the issue is different from the Blank PIN issue we discussed here. But still, the outcome is the same, the user is not able to log in with their WHfB PIN. The PIN issue doesn’t happen the moment the user first logs in after the device was upgraded to Windows 11 24h2. It seems to appear after the device resumes from sleep, when Windows silently refreshes the primary refresh token (PRT) in the background.
There’s no noticeable policy change, no reboot…that could have broken it, but the result is a funny and weird broken Windows Hello for Business (WHfB) experience. The funny thing is that there is no easy path back in when you implemented the Passwordless experience. How are people going to log in with their Password if they don’t know their password? Something with a chicken-and-egg situation.
UPN change caused the 0xc000006d: Your PIN isn’t available error
This is not really a bug introduced in Windows 11 24H2. In fact, the issue may have existed long before the upgrade ever happened. But the upgrade caused the Windows Hello PIN to become unavailable (PIN isn’t available: 0xc00006d).
In many organizations, user principal names (UPNs) change over time. This could be due to mergers, rebranding, or just general cleanup. A user might go from [email protected] to [email protected]. These changes are handled smoothly in Entra ID if you follow the proper guidelines from Microsoft. The user logs in with the new UPN, applications adjust, and most of the time, you will not notice anything weird.
However, Windows Hello for Business (WHfB) is built on top of strong key binding. When a user sets up Hello for the first time, Windows generates a key pair stored in the TPM, tied to the UPN in use at that moment. You can check this by using: certutil -csp “Microsoft Passport Key Storage Provider” -key
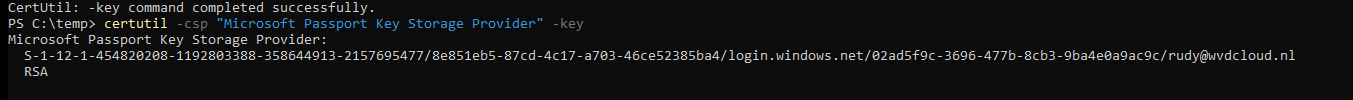
This key is used to silently request tokens from Entra ID. If the UPN later changes, the Hello credential still seems to point to the old name. We can spot the same thing in the event log. As shown below, the computer attempted to validate the credentials for an account (which is the old username)
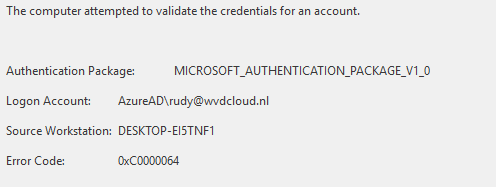
From there on, it gives us the error code: 0xc0000064 (username does not exist)
Windows 11 24H2 Just Enforced What Was Already Broken.
With Windows 11 24H2, Microsoft enabled Local Security Authority (LSA) protection by default for supported hardware. This includes enhanced checks around key use and identity binding. Once the device refreshes its primary refresh token (PRT), which seems to have happened during sleep, Windows validates the Hello credential against the currently known user identity.
If the Hello key references a UPN that no longer exists, the token request fails. In turn, the Hello login fails. The system provides very little feedback, leaving users to stare at a broken sign-in screen. Behind the scenes, the Entra ID response includes errors like AADSTS50034 (user not found) or AADSTS135010 (missing key binding), but these are not shown to the user.
This explains why everything worked after the upgrade and why it stopped working hours later. The key was broken all along. Windows 11 24H2 simply enforced the rules more strictly. With it, the existing Windows Hello PIN became invalid.
Verifying the UPN Failure Using dsregcmd
To confirm the underlying cause of The PIN isn’t available error, the following command can be run while signed in or during troubleshooting: dsregcmd /status /verbose
In the output, the section labeled “Ngc Prerequisite Check” will often contain clues. Look for lines referencing 0xC0000064, AADSTS50034, or AADSTS135010.
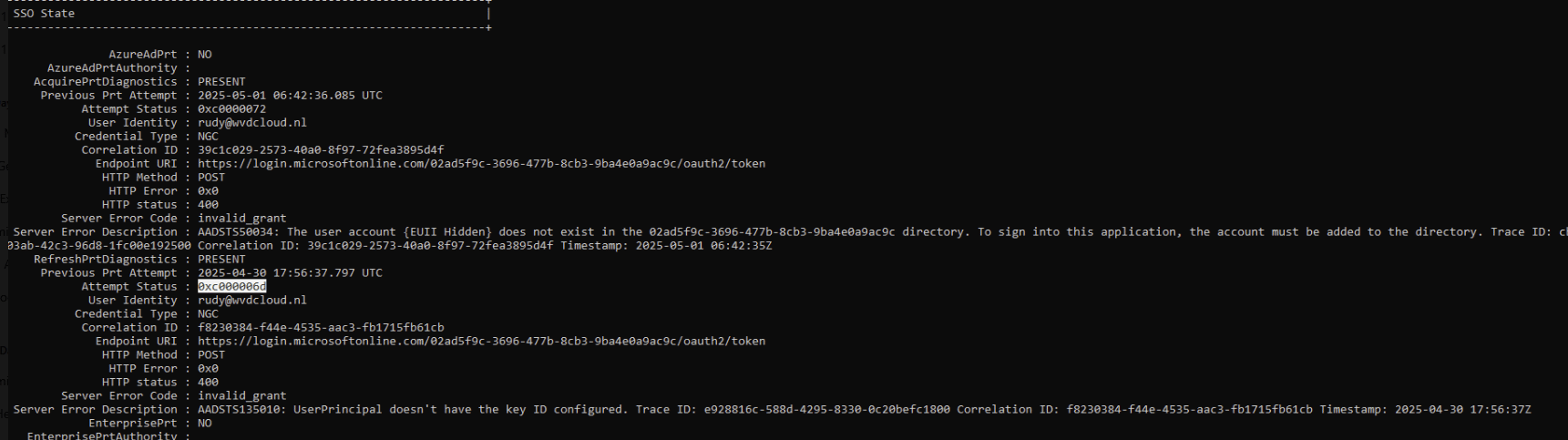
These indicate that the Windows Hello credential failed to authenticate with Entra ID because the identity no longer matches the key that was originally provisioned. This serves as confirmation that the failure is not caused by TPM hardware, Hello corruption, or device misconfiguration, but by an identity binding mismatch.
Windows Hello Recovery with Password… If You Still have one
If your environment still supports password fallback, recovery is simple. At the login screen, select “Sign-in options” and choose the password method. Sign in using the user’s current UPN and Entra ID password. After sign-out and sign-in, Windows will detect the outdated Hello container and prompt for PIN setup. This rebinds the credential to the correct UPN.
In passwordless-only environments, this option isn’t available. Without a valid Hello credential, the user is locked out. Let’s examine two possible fixes.
Option 1: Removing the NGC folder
For the first option to fix it, you’ll need a local administrator account or recovery method to remove the broken Hello container. After opening PowerShell as an admin, we need to delete the NGC folder :
C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Ngc
After deleting the Ngc folder, you should be able to log in as the user.. but yes..again… with a Password..
Option 2: CertUtil:
If you don’t want to use an additional local admin account to fix the Windows Hello credential issue, we could use the certutil.
Open op PowerShell as the signed-in user (yes… again, you need a password to log in) and enter the certutil -deletehellocontainer command. This command will delete the Hello Container for the logged-in user, which fixes the issue as well.
Option 2+ TAP
If we don’t have the password and want to delete the Hello container, we could use a Temporary Access Pass (TAP).TAP gives the user a one-time credential they can use to sign in and reconfigure Windows Hello.
Another Windows 11 24H2 Surprise Worth Noting
Windows 11 24H2 also exposed issues with AppLocker and PowerShell Constrained Language Mode. In some environments, script enforcement quietly stopped working after the upgrade—no errors, no warnings.
That issue is covered in a separate blog:
Windows 11 24H2: AppLocker + PowerShell Constrained Language Mode = Broken
Luckily, Microsoft already fixed that issue with the latest 2025-05 update, but still…. test multiple devices before upgrading the whole fleet of devices to Windows 11 24h2 to ensure everything works.
Conclusion
Windows 11 24H2 didn’t break Windows Hello; it just enforced what was already broken. The PIN credentials are tied to the UPN used during setup. If that UPN changes, the credential may silently fail. Before 24H2, this often went unnoticed. Now, with stricter checks like LSA protection, the mismatch causes sign-in failures, and it shows you the message that your PIN isn’t available.
If password fallback is available, recovery is easy. Without it, you’ll need a local admin or recovery flow to reset Hello.
