This blog is about a security detail in Windows 11 that is easy to miss. If you use Personal Data Encryption you need to be aware of the Automatic Restart Sign On (ARSO) policy. If this policy is not configured (which means it’s enabled), your files are not as protected as you think. I will show you what ARSO is, why it matters, and the steps Microsoft does not highlight, but you need to know.
Introduction
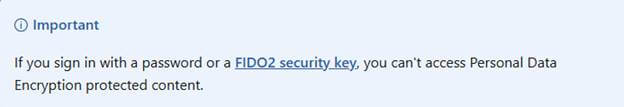
Personal Data Encryption in Windows 11 is designed to secure the user’s/personal files. The goal is that only you, the actual user, can access important folders, such as Desktop, Documents, and Pictures, provided you use Windows Hello for Business to sign in. Microsoft says a password alone should never get you access to the data.
And… believe me, Microsoft mentions it a lot of times

But there is a catch. To get this level of protection, you must meet every requirement for Personal Data Encryption. If you miss just one, Windows quietly falls back to weaker security. The most common mistake? Forgetting to disable a background feature called Automatic Restart Sign On.
What Personal Data Encryption Needs To Work
Personal Data Encryption is not just a checkbox. It needs several things in place to provide real protection:
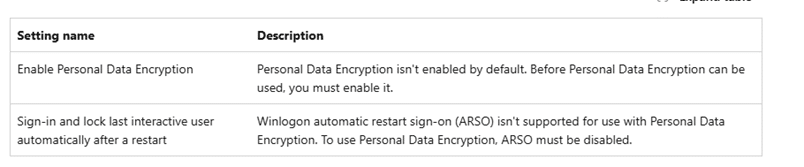
- You must enable Personal Data Encryption for the user folders you want to protect.
- Windows Hello for Business must be set up. That means your users need to sign in with a PIN or biometrics, never just a password.
- And here is the one most people forget: you must disable Automatic Restart Sign On.
What Is Automatic Restart Sign On (ARSO) and Why Does It Matter
Automatic Restart Sign On, also known as ARSO, is a Windows feature that is usually invisible to end users. Its main purpose is to help Windows finish updates. After a restart, ARSO automatically signs in the last user account so Windows can finish setting up updates or features in the background. The session is locked right away, so no one else can use the desktop, but tasks can still run.
Here is the problem. ARSO uses stored credentials, which could include just the user’s password. This means after a reboot, Windows might use a password behind the scenes to finish signing in, not your PIN or fingerprint. That is enough to break the security promise of Personal Data Encryption.
If ARSO is not set to Disabled, Windows cannot guarantee that you are signed in with Windows Hello for Business. So, to avoid breaking the system, Windows silently switches to a fallback encryption method.
The funny thing? ASRO is enabled by default!
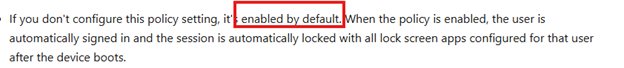
With this policy being automatically enabled by default, we NEED to disable it with a separate settings catalog!
Why Does Windows Switch To Data Protection API (DPAPI)
When ARSO is enabled, the device cannot enforce the requirement that you must use Windows Hello for Business. As a result, Windows stops using Personal Data Encryption for new files and falls back to the standard Data Protection API.
Data Protection API is the built-in Windows encryption system that protects data for a user account. It makes sure that only the same user can open encrypted files. But it does not care how you sign in. You could use a password, a PIN, a FIDO key, or biometrics; any of these will work. This is less secure than Personal Data Encryption, which is supposed to require a stronger sign-in.
What Happens If You Miss The Automatic Restart Sign On Setting
If you enable Personal Data Encryption but forget to disable ARSO:
- You will still see the yellow lock icon on your files, which looks like everything is protected.
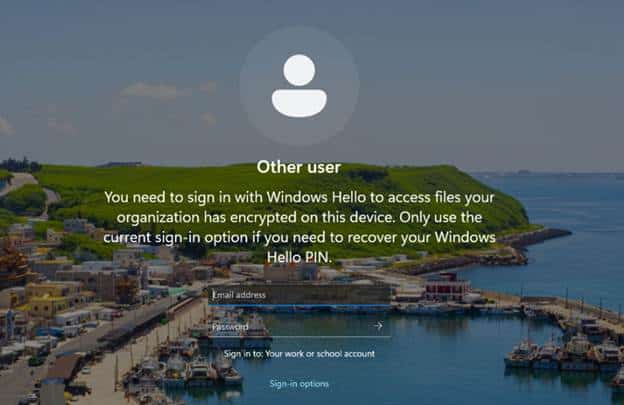
- The lock screen will even tell you to use a PIN for access.
- Local admin accounts are still blocked from opening these files, so it seems secure.
- But here is the issue: as the regular user, you can still open your files with just your password.
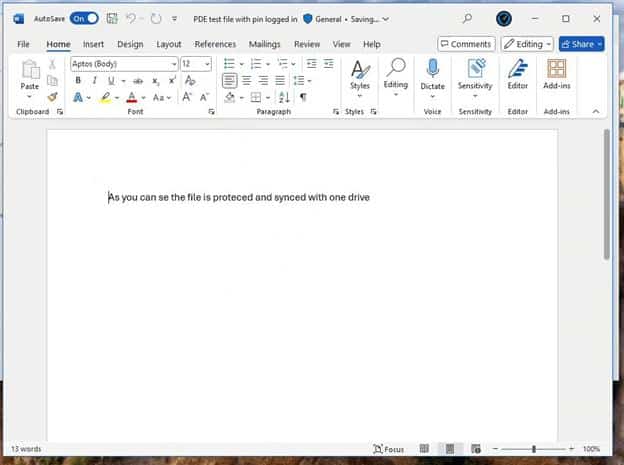
When looking closer at the real protection status by looking at the properties of the file, you will notice that the Personal Data Encryption is off, even while everything else indicates that PDE is enabled
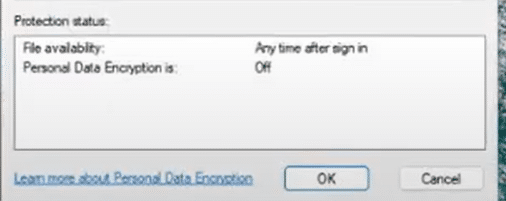
What is really happening is that Windows has quietly stopped using Personal Data Encryption and is now using the weaker Data Protection API. The change is invisible unless you actually test it.
How To Set Up Personal Data Encryption Correctly
If you want real protection from Personal Data Encryption, follow these steps:
- Make sure Windows Hello for Business is fully set up for your users.
- Use a policy to enable Personal Data Encryption on the folders you want to protect.
- Create a separate policy to disable ARSO.
- In Group Policy, go to Computer Configuration, Administrative Templates, Windows Components, Windows Logon Options, and look for Sign in and lock last interactive user automatically after a restart. Set this to Disabled.
- In Intune, use the Settings Catalog. Search for Winlogon automatic restart sign on and set it to Disabled.
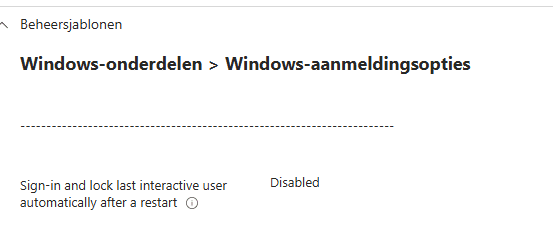
If you do not set ARSO to Disabled, your users will always be able to open protected files with just a password, and you will not receive the expected security.
Why This Automatic Restart Sign On Detail Is So Easy To Miss
- The ARSO policy is not included in the standard Endpoint Security template for Personal Data Encryption in Intune.
- You have to know about it and create an extra policy just for ARSO.
- While Microsoft does mention in their requirements that ARSO should be disabled, they do not explain what actually happens if you skip this step. There is no clear warning that leaving ARSO enabled means Windows will quietly fall back to using Data Protection API. This fallback allows users to access protected files with just a password, which defeats the purpose of Personal Data Encryption.
Because of this, even careful administrators can think they are protected, when in reality, users are only getting standard encryption, not the extra layer tied to Windows Hello for Business.
Microsoft Needs To Fix This
This ASRO step is too easy to forget. In my opion, Microsoft should update their documentation to make the ARSO requirement impossible to miss. Even better, the ARSO setting should be added directly to the Endpoint Security settings for Personal Data Encryption in Intune.
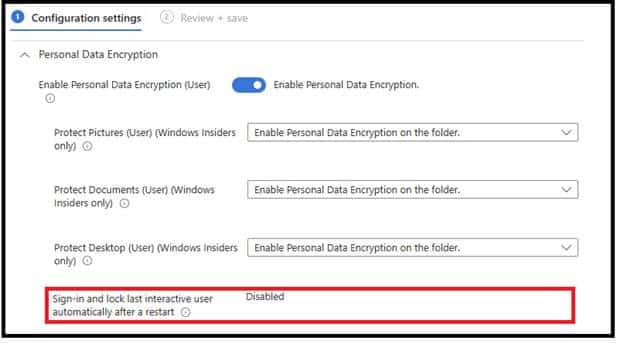
If this were part of the default template, fewer organizations would make this mistake and believe their files are safe when they are not.
Conclusion
Personal Data Encryption can only protect your files as promised if ARSO is Disabled.
If you leave ARSO enabled (which is the default setting), Windows will automatically revert to using the standard Data Protection API. That means a password will always be enough to get into your supposedly protected files.
So, whenever you set up Personal Data Encryption, double-check the ARSO policy. This is the hidden step that makes the difference between real security and just a locked icon.
