
Microsoft is redefining Windows 11 compliance with Microsoft Azure Attestation (MAA). They are doing so with some new evaluation settings, such as firmware protection, virtualization, and memory integrity, taking compliance policies far beyond the existing compliance based on Device Health Attestation (DHA). Want to know more? Continue reading!
Introduction to MAA
Every now and then, while scrolling through the Intune portal’s JavaScript code, something unexpected caught my eye. This time, it wasn’t a new button or redesigned blade; it was a feature hinting at the next major shift in Windows compliance. Buried deep in the Intune portal code, sat a line that read:
Enable Windows 11 supported device health settings backed by MAA.

That small piece of text opened the door to something big: a clear sign that Microsoft is preparing to replace Device Health Attestation (DHA) with Microsoft Azure Attestation (MAA).
And once you connect that to what Intune is starting to surface under the hood, the story becomes much more interesting.
Device Health Attestation
Before discussing what we uncovered, it’s worth understanding what is currently underneath Intune’s device compliance engine, Device Health Attestation (DHA).
For years, DHA has been the silent validator behind the scenes, confirming whether a Windows device is trustworthy, meaning it has not been tampered with. Let’s start with a history lesson on how Compliance policies are evaluated.
Each time a system boots, the firmware, bootloader, and OS components are measured and stored inside the TPM as PCR values. These measurements prove whether Secure Boot, BitLocker, and Code Integrity ran cleanly.
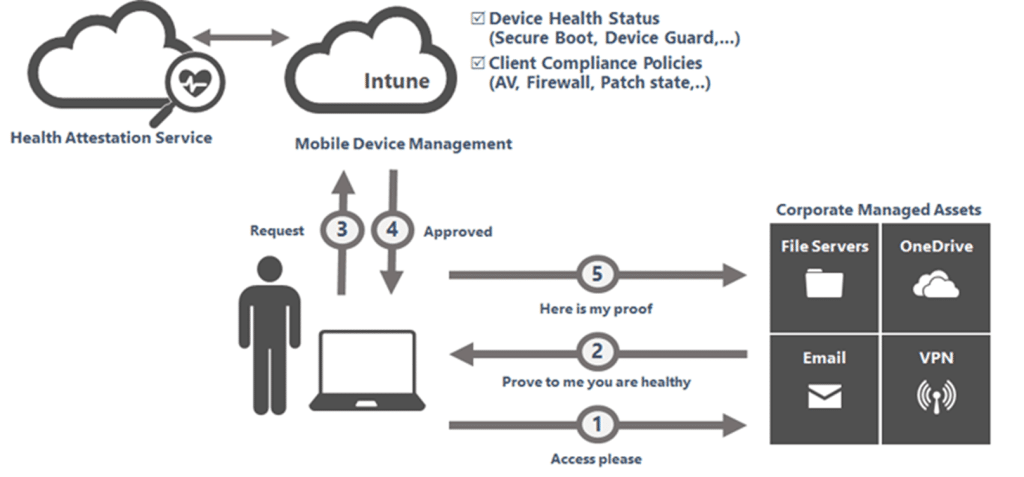
When Intune checks compliance, it doesn’t just ask Windows for a status flag. It triggers the HealthAttestation CSP, which reaches out to the Device Health Attestation service (has.spserv.microsoft.com)

The device health attestation cloud service verifies the TPM evidence, signs a report (health certificate), and sends it back.
Intune then reads that report and updates the isCompliant attribute in Entra ID, the value Conditional Access relies on, before allowing access to corporate resources.
Without that health attestation cycle, a device’s health state simply can’t be proven.
Why Microsoft Needed Something New
The old DHA model worked fine for core features, but didn’t evolve with Windows 11.
It could only validate a small subset of modern platform protections: BitLocker, Secure Boot, and basic Code Integrity….nothing more.
Windows 11, however, introduced a much broader set of security baselines: Firmware Protection, Memory Integrity (HVCI), Kernel DMA Protection, and Virtualization-Based Security (VBS).
The DHA service couldn’t recognize these states or evaluate their attestation logs, which meant the compliance system was effectively blind to several of Windows 11’s most important security features. That’s where Microsoft Azure Attestation (MAA) comes in.
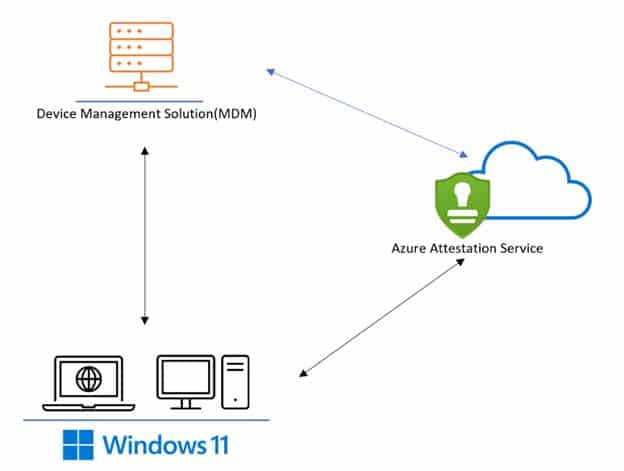
Moving to Microsoft Azure Attestation
Microsoft Azure Attestation is the cloud-based evolution of DHA.
It extends the same concept, verifying TPM measurements and signed boot logs into a broader, modern attestation model. Instead of using legacy SOAP and XML calls, MAA uses a REST-based service hosted on attest.azure.net.
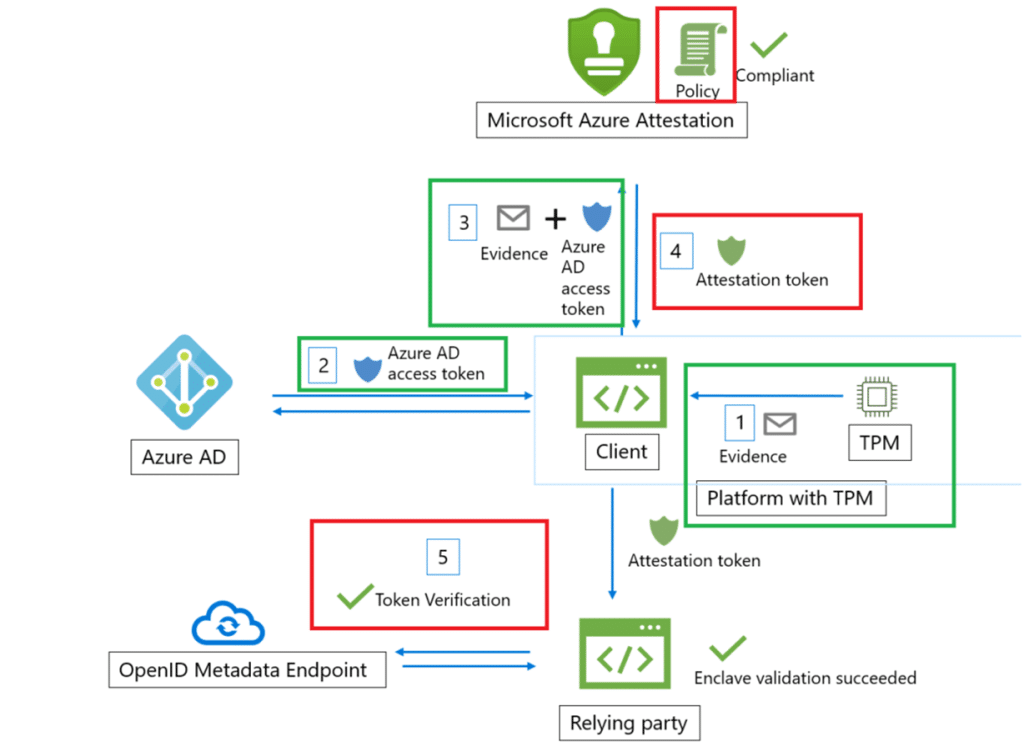
When Intune triggers attestation, the client (HealthAttestationClientAgent.exe) now sends its evidence to that Azure endpoint, authenticated by an AAD bearer token.
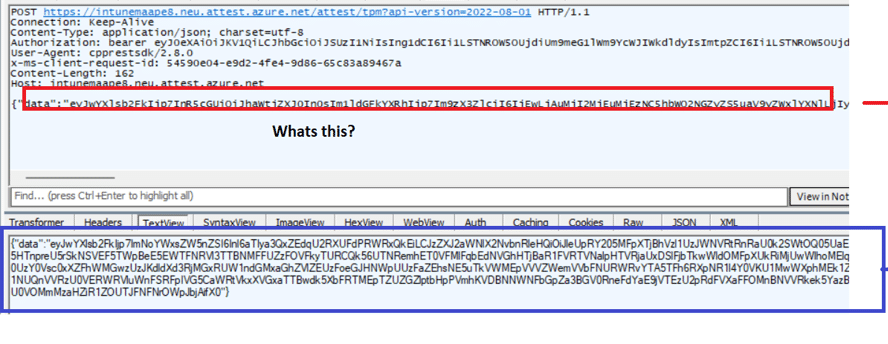
The report that comes back isn’t a simple XML anymore, it’s a JSON Web Token containing richer attestation claims. Alongside BitLocker and Secure Boot, it can now confirm if ELAM, firmware protections, HVCI, DMA protection, and VBS are all active.
Microsoft started using this new model across Azure confidential computing long before it appeared in Intune. Now it’s making its way into Windows compliance. Now we know how it worked and how MAA is kicking in, let’s switch back to the Intune Portal.
New Microsoft Azure Attestation Evaluation Settings
After digging through the Intune portal code, I noticed something interesting: a new section titled “Microsoft Attestation Service evaluation settings.”
Although it wasn’t visible in the actual UI, the JS code made its purpose clear. A new object named enableMAAWindows11Settings appeared with the description:
- name: “Enable Windows 11 supported device health settings backed by MAA”,
Scrolling further through the JSON revealed the new attestation settings listed under it, all tied to the same feature: enableMAAWindows11Settings.
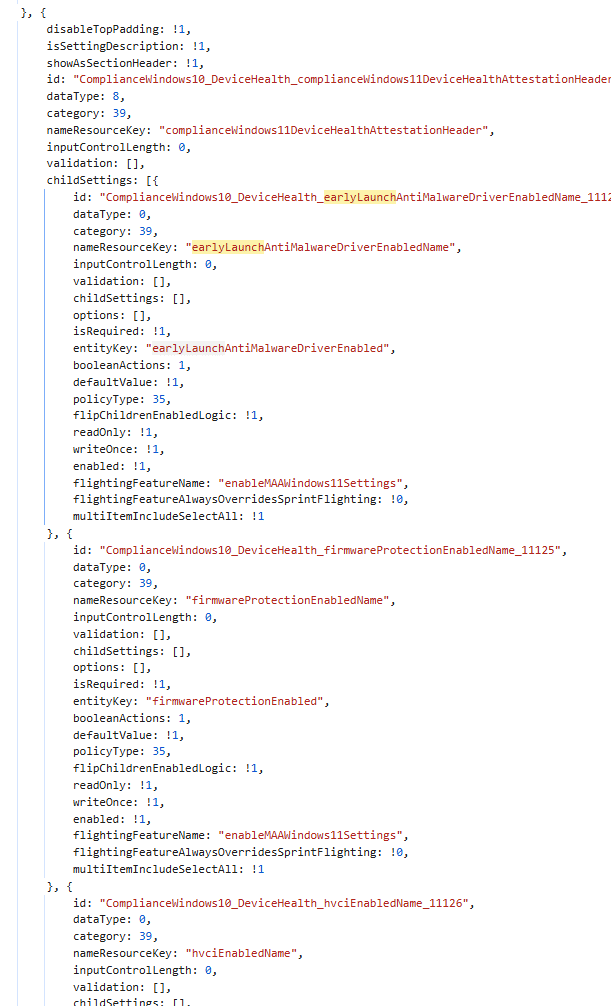
What Appears Once Microsoft Azure Attestation is Enabled
If we transform the JSON into something more readable and visual, this is how the new Microsoft Attestation Service evaluation settings will appear, based on what my LLM told me it would look like.
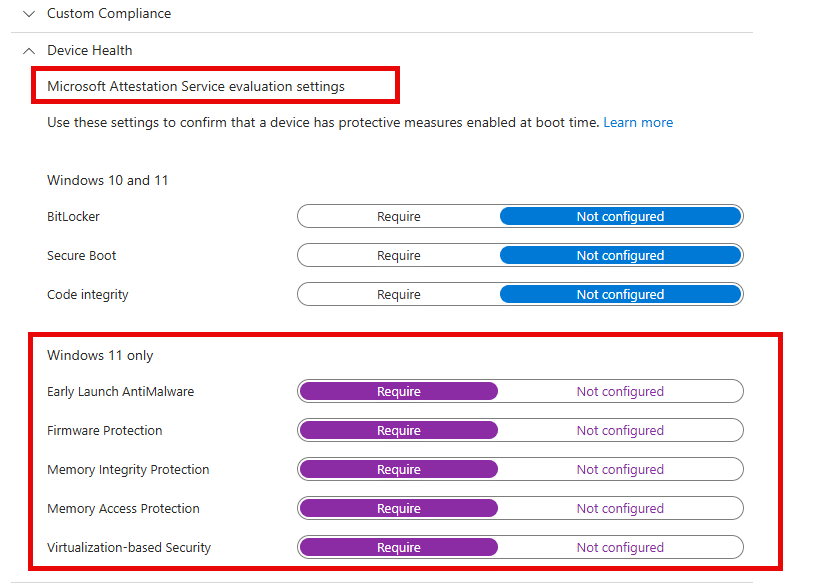
The Microsoft Attestation Service evaluation settings will add five new Windows 11-only checks:
- Early Launch AntiMalware
- Firmware Protection
- Memory Integrity Protection
- Memory Access Protection
- Virtualization-based Security
Each one maps directly to attestation claims in the MAA report, the same values returned by GetAttestReport through the HealthAttestationCSP.
This aligns perfectly with the updated attestation evidence MAA now provides.
The compliance engine will soon be able to validate the full platform posture of a Windows 11 device, not just its legacy DHA boot integrity.
Why Microsoft Azure Attestation Matters
This isn’t just another compliance option buried in the portal. It’s the visible start of Microsoft migrating the old-school Health Attestation trust to Microsoft Azure Attestation
For administrators, this shift means:
- Better compliance checks directly tied to TPM-based attestation.
- Faster responses using the Azure service instead of the legacy DHA endpoints.
- Future consistency across Windows, Azure, and other managed workloads.
MAA turns what was once a basic “is the device healthy?” check into a complete attestation model that understands and works with the deeper security layers built into Windows 11.
Closing Thoughts
Device Health Attestation laid the foundation for modern Windows compliance.
But the world around it has evolved, and so has Microsoft’s approach. By embedding EnableMAAWindows11Settings into the portal, Microsoft signals that Intune’s compliance engine is about to move away from the legacy DHA model entirely.
