
If you’ve been wrestling with the Intune Management Extension (IME) lately, you know how essential those little log files are to your sanity. Whether you’re deploying Win32 apps or troubleshooting a PowerShell script gone rogue, those logs are your trusty sidekicks. And guess what? Microsoft has added a couple of new ones to our arsenal—say hello to AppWorkload.log and ClientCertCheck.log!
Why the IME Logs Are Your Best Friends
Let’s face it—troubleshooting without logs is like trying to find your way out of IKEA without those handy arrows on the floor. Every time something goes south with an application deployment, the first place we IT admins look is the log files. They tell us everything we need to know (and sometimes more) about what’s happening under the hood.
With the IME, these logs are like breadcrumbs leading us to the culprit. Over time, Microsoft has beefed up the logging capabilities in IME, giving us more granularity and more places to look when things go sideways.
The New Kids on the Block: AppWorkload.log and ClientCertCheck.log
When you thought you had all the logs under control, Microsoft introduced two more.
Here’s what they’re all about:
1. IME AppWorkload.log
This shiny new log is your go-to for tracking the workload of Win32 app deployments. If you’re wondering how your apps are behaving, this log has got you covered. It dives into the nitty-gritty of app installations, checking off tasks like “Is the app required?”, “Do we need to uninstall anything first?”, and “Is the app even applicable?”. It’s like the IME’s personal assistant, making sure everything runs smoothly.
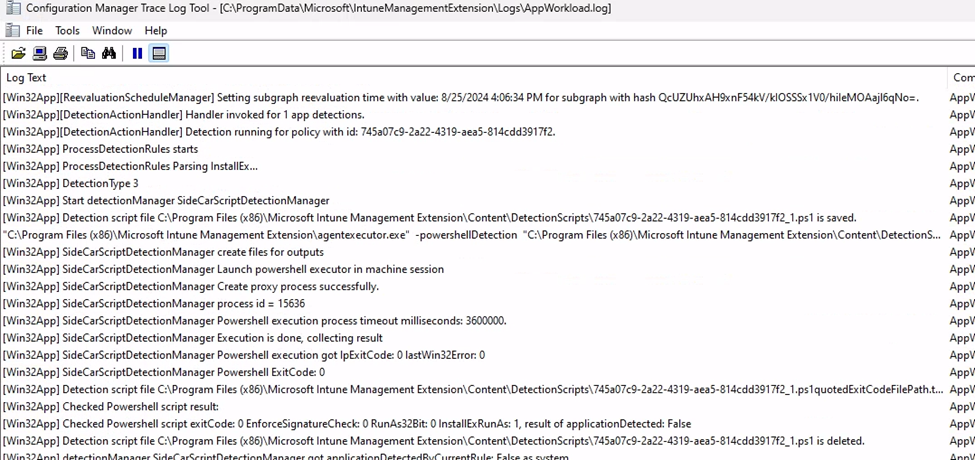
In the past, these events were all logged inside the IntuneManagementExtension.log, but thankfully, Microsoft decided to move them over to this dedicated AppWorkload.log. Now, everything related to app deployments is neatly organized, making troubleshooting and monitoring a breeze.
2. IME ClientCertCheck.log
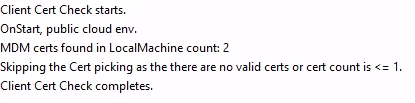
Let’s talk about the ClientCertCheck task in the Intune Management Extension—it’s like your device’s security guard, constantly checking to ensure the client certificates used for device management are up to snuff. It dives into the LocalMachineMy store, ensuring each certificate has the right OID, a private key, and the correct subject name format. If all’s good, it checks the tenant is eligible through a flighting check. This is all about keeping your device management secure and compliant, ensuring only valid certificates
Where to Find These Logs
Just like the other IME logs, these new additions are tucked away in the usual spot:
C:\ProgramData\Microsoft\IntuneManagementExtension\Logs
Open the logs in OneTrace, CMTrace, or your log viewer of choice and start digging. They contain the information you need to keep your Intune App deployments running smoothly.
Why These Logs Matter
You might be thinking, “Great, more logs to check. Just what I needed!” But trust me, these are here to make your life easier. The AppWorkload.log provides a more focused view on app deployments, which is super handy when you’re managing a fleet of devices. And ClientCertCheck.log? Well, that’s is something for an additional blog because when Microsoft decides to hardcode the flighted tenants in it, then it must be special?
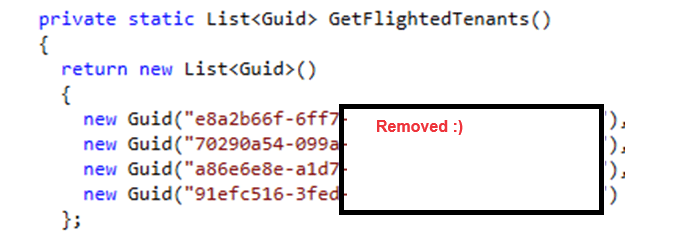
For now, I removed the complete tenant ID as I think it’s weird that those are mentioned in the code. Keep an eye out for the additional blog focussing on this ClientCertCheck task!
Wrapping Up
So, next time you’re neck-deep in troubleshooting an Intune issue, remember to check out these new logs. They might save you from hours of head-scratching. Separating these logs from the IntuneManagementExtension.log into their dedicated files is a game-changer, making your job as an IT admin much easier.
For a deeper dive into the Intune Management Extension and to stay ahead of the curve, check out the Intune Management Extension Deep Dive Webinar by Patch My PC.
Until next time, happy troubleshooting!
