This article covers integrating the Patch My PC Publisher with your Intune tenant. We will go over creating an app registration in your Azure AD environment and configuring the Graph API permissions required for the Publisher to automatically create, update and assign Win32 applications in your Intune tenant; as well as configuring the tenant authority, application ID and application secret within the Publisher.
Step 1: Registering the Patch My PC Application in Azure AD
In order for our service to have permissions to your Intune tenant for application management, start by navigating to your environment’s Azure AD portal, head to App registrations, and click New registration in the top left of the main pane.
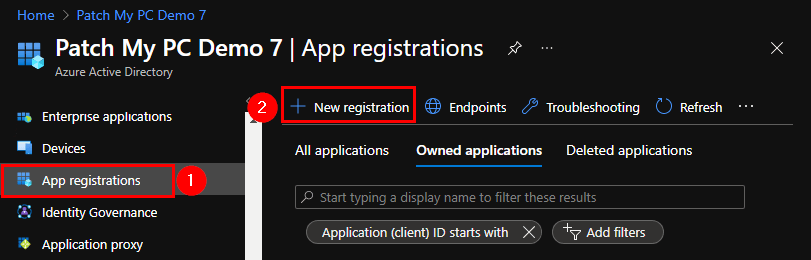
Give your app registration a relevant name such as “Patch My PC – Intune Connector”. Configure the account types base on your tenant requirements. For the Redirect URI, leave it default unless you have specific requirements for configuring the Redirect URI. Then click Register.
Step 2: Configure API Permissions for the New Application
After you register a new application, we will need to delegate certain permissions in order for the Patch My PC Publisher to create and update Win32 applications in your Intune tenant, as well as view Azure groups and create assignments for the applications automatically.
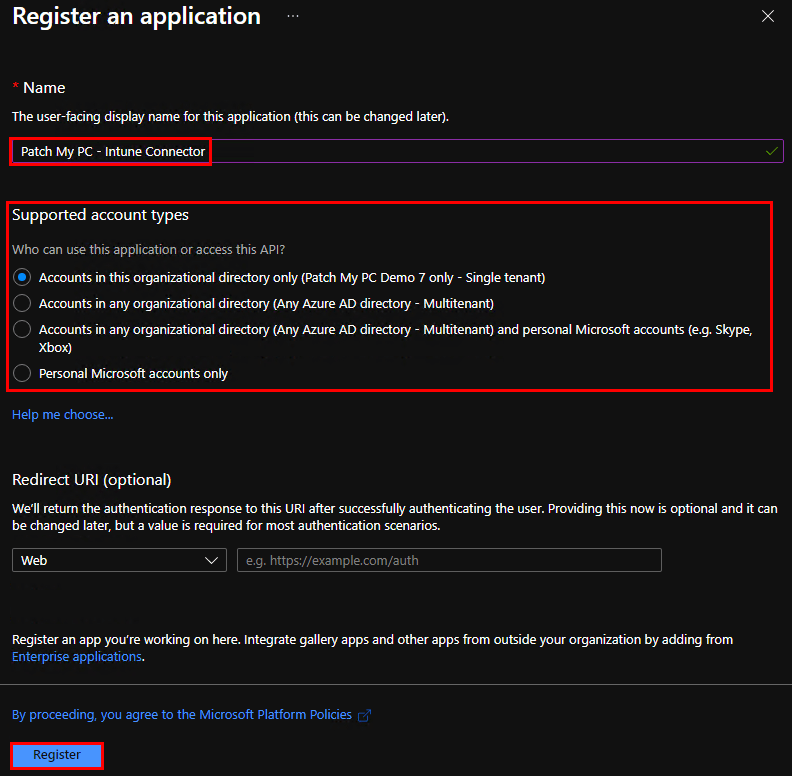
Once the new app is registered, navigate to the API permissions node in the left column of the newly created app’s page. In the API permissions page, click the button to Add a permission, then in the right pane that appears, select the Microsoft Graph API.
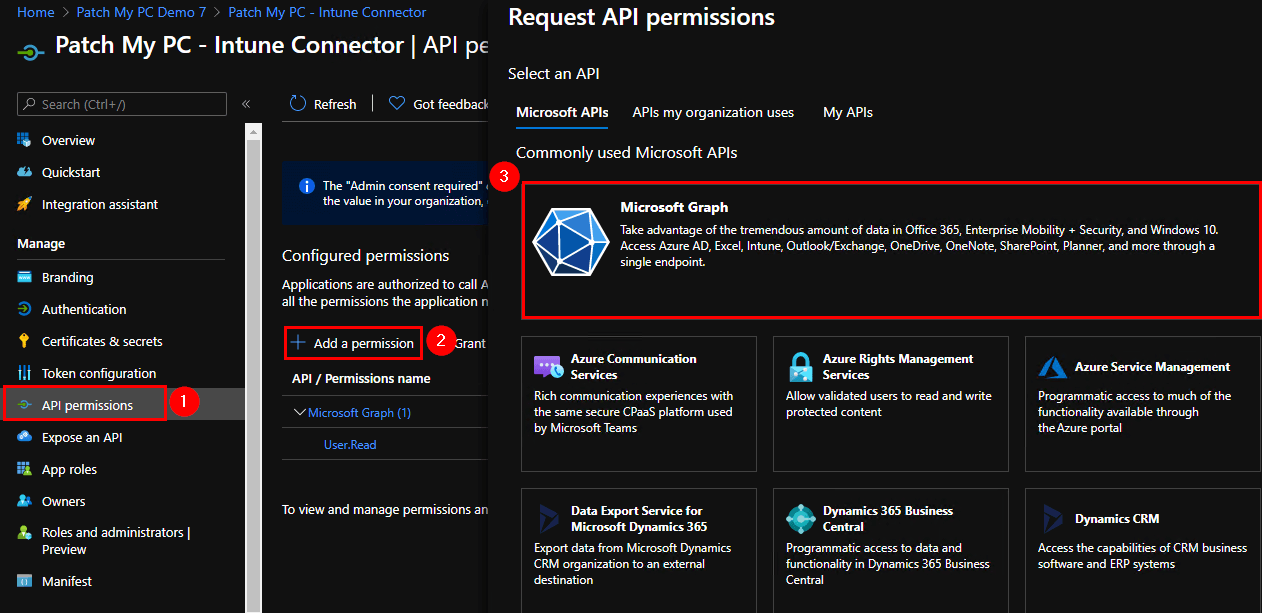
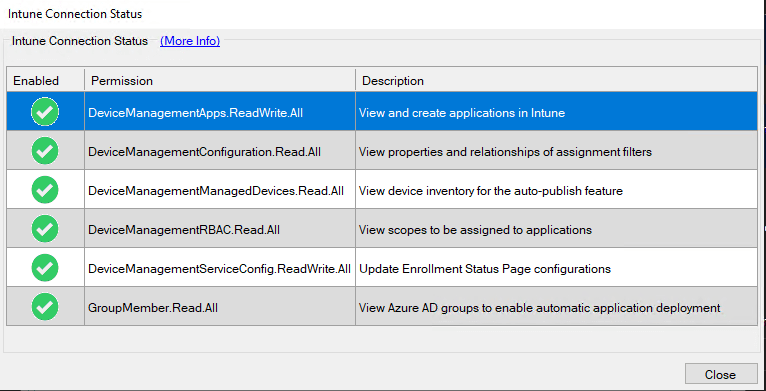
Then, you are prompted for what type of permissions your app requires, select Application permissions. In the Select permissions table view, search for “DeviceManagement” and under those permissions, enable the following:
- DeviceManagementApps.ReadWrite.All
- View and create applications in Intune
- DeviceManagementConfiguration.Read.All
- View properties and relationships of assignment filters
- DeviceManagementManagedDevices.Read.All
- View device inventory for the auto-publish feature
- DeviceManagementRBAC.Read.All
- View scopes to be assigned to applications
- DeviceManagementServiceConfig.ReadWrite.All
- Update Enrollment Status Page configurations
Then, search for “GroupMember”, and under Group permissions, enable:
- GroupMember.Read.All
- View Azure AD groups to enable automatic application deployment
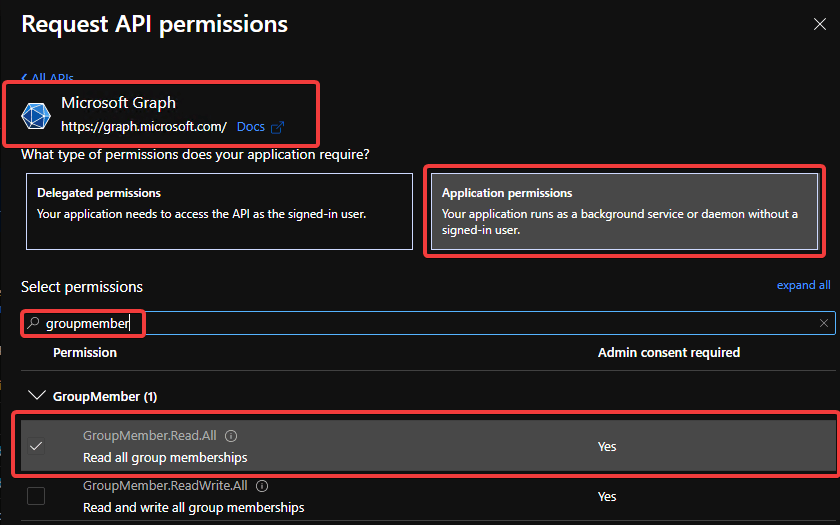
Click Add permissions.
To approve the new permissions, click Grant admin consent for . Choose Yes if you are prompted to consent for the required permissions. You must be logged into an Azure AD account with permissions to perform this task.
The result is shown below.
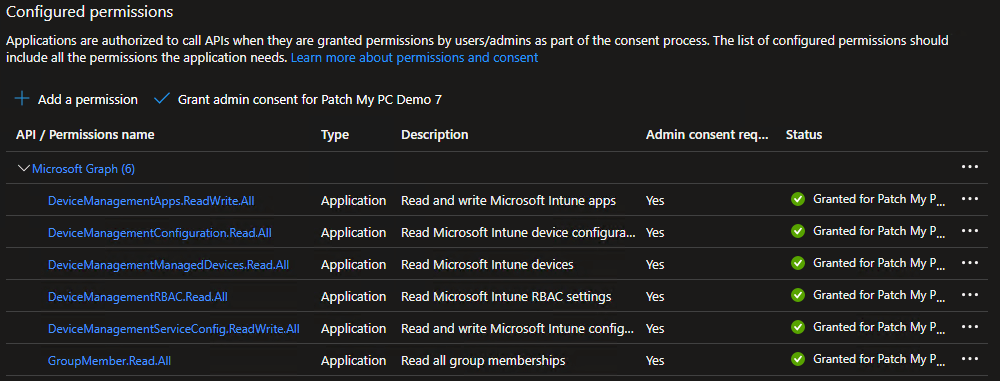
Note: Granting admin consent may require one of the following roles: Global Administrator or Privileged Role Administrator.
Step 3: Getting the Client Secret and Application ID
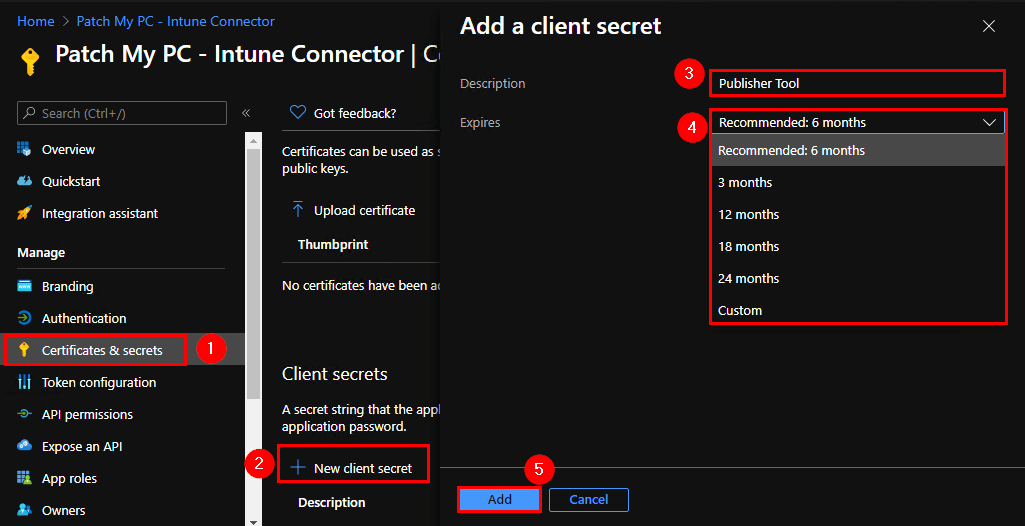
Now, we must add a client secret, a string that our app will use to prove its identity when requesting a token. Navigate to the Certificates & secrets node in the left column, and click the button to add a New client secret. Decide on a description and expiration date (in months) that best suits your organization’s needs, then click Add.
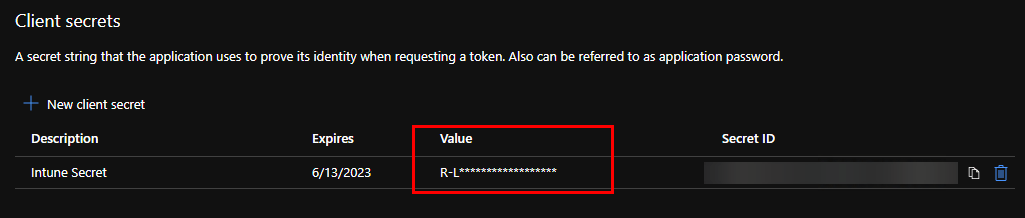
Copy the Value for the Client Secret you created. Save this value to a secure location, you will enter the value under Application Secret in the Intune Options of the Publisher.
Then, navigate to the Overview node, and copy the Application (client) ID. Save this value to a secure location along with your secret key value.
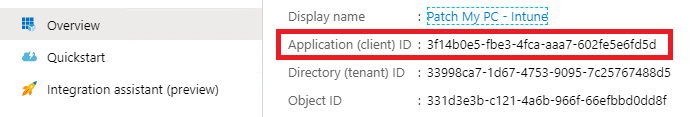
You may receive an error similar to ‘An error occurred while connecting to Intune: AADSTS7000215: Invalid client secret is provided.’ within the PatchMyPC.log file. If you receive this error please repeat step 3 above to create a new secret, or review your existing secret configuration within the Publisher to ensure you are using the correct value.
In addition to the client secret, certificate-based authentication is also available in the Patch My PC Publisher. For more information, see the Microsoft documentation for more information: Create a self-signed public certificate to authenticate your application.
Step 4: Configuring the Patch My PC Publisher to Connect to the Intune Tenant
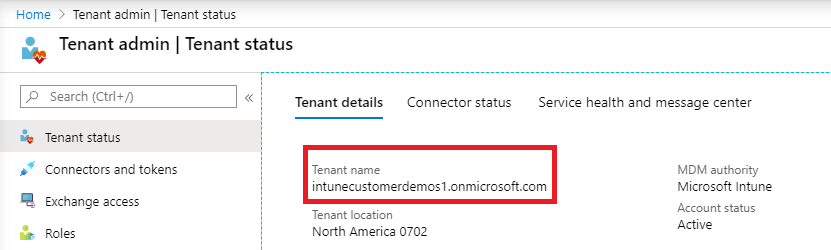
If you do not know your Intune tenant domain, navigate to the tenant status page in your Intune tenant, and look at the property for Tenant name.
Now, it is time to go to the Patch My PC Publisher and input the Authority, Application ID, and Application Secret into the Intune Options window of the Publisher.
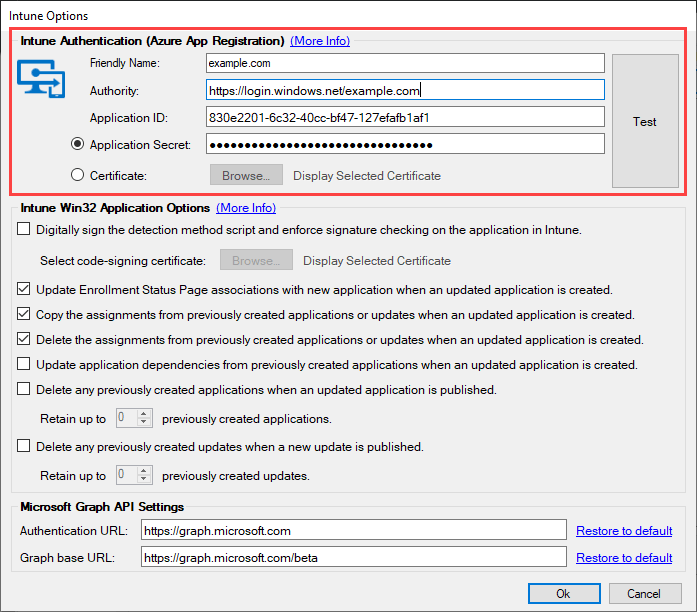
Replace with the Tenant name you found in the tenant status page of your Intune tenant. Paste the Application ID and Application Secret that was saved from earlier. Click Test to view the Intune Connection Status and validate that the Publisher can connect to your Intune tenant. If the listed permissions all have a green checkmark under Enabled, you can now begin to publish applications to your Intune tenant.
In addition to the client secret, certificate-based authentication is also available in the Patch My PC Publisher. For more information, see the Microsoft documentation for more information: Create a self-signed public certificate to authenticate your application.
If you would like to use certificate-based authentication, choose the radio option Certificate and browse out to select the certificate. The certificate needs to be in the local machine’s Personal store.
If the associated tenant is on GCC High, the changes below are required:
- Authority: https://login.microsoftonline.us
- Authentication URL: https://graph.microsoft.us
- Graph Base URL: https://graph.microsoft.us/beta
